Additional Resources:
Our pfsense tutorials
Getting Started Building Your Own Wireguard VPN Server
https://staging-forum.lawrencesystems.com/t/getting-started-building-your-own-wireguard-vpn-server/7425
pfsense manual
https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/index.html
Christian McDonald
pfSense Software + WireGuard Package - Project Report 011
Connecting With Us
Lawrence Systems Shirts and Swag
►👕 https://teespring.com/stores/lawrence-technology-services
AFFILIATES & REFERRAL LINKS
Amazon Affiliate Store
 Lawrence Systems's Amazon Page
Lawrence Systems's Amazon Page
All Of Our Affiliates that help us out and can get you discounts!
 https://www.lawrencesystems.com/partners-and-affiliates/
https://www.lawrencesystems.com/partners-and-affiliates/
Gear we use on Kit
 Kit
Kit
Try ITProTV free of charge and get 30% off!
 Learn technology and pass IT certifications with ITProTV
Learn technology and pass IT certifications with ITProTV
Use OfferCode LTSERVICES to get 10% off your order at
 https://www.techsupplydirect.com/
https://www.techsupplydirect.com/
Digital Ocean Offer Code
 DigitalOcean | Cloud Hosting for Builders
DigitalOcean | Cloud Hosting for Builders
HostiFi UniFi Cloud Hosting Service
 HostiFi - UniFi Cloud Hosting
HostiFi - UniFi Cloud Hosting
Protect you privacy with a VPN from Private Internet Access
 Buy VPN with Credit Card or PayPal | Private Internet Access
Buy VPN with Credit Card or PayPal | Private Internet Access
Patreon
 lawrencesystems | creating Tech Tutorials & Reviews | Patreon
lawrencesystems | creating Tech Tutorials & Reviews | Patreon
 Timestamps
Timestamps 
00:00 pfsense Wireguard remote access
02:30 pfsense Wireguard Documentation
03:00 Lab Setup
05:31 Install Wiregaurd Package
06:05 Wireguard Firewall Rules
07:02 Creating Wireguard Tunnel
08:46 WAN Wireguard Rule
09:22 Wireguard Outbound NAT Rule
11:03 Adding Peers
11:44 Configuring Linux Peer
16:00 Configuring Windows Peer
19:52 Split VS Full Tunnel
22:19 Wireguard Troubleshooting
#Wireguard #pfsense #VPN
I have watched Tom’s video and am having trouble completing a successful handshake.
I am using pfSense as my home firewall and attempting to setup my iPhone (on cellular) as a peer.
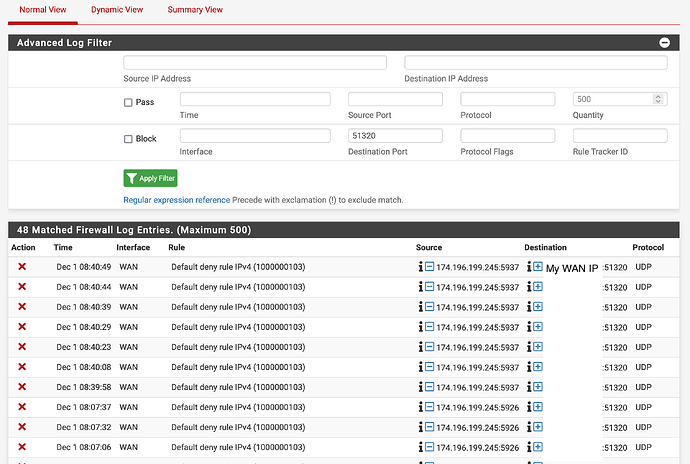
I see in my pfSense system logs that the incoming packet is blocked by the default deny rule, however I believe I have created the WAN firewall rule correctly.
Here is the system log filtered for WG traffic:
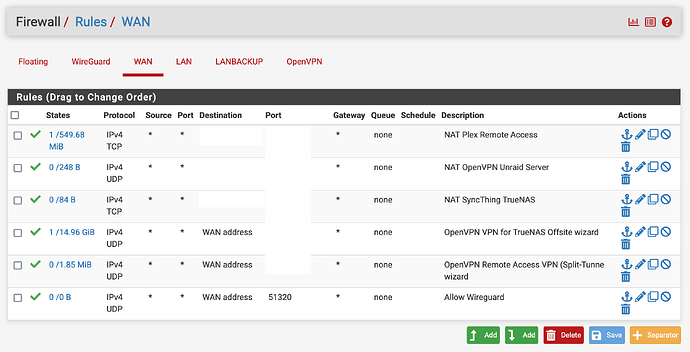
Here are my WAN rules:
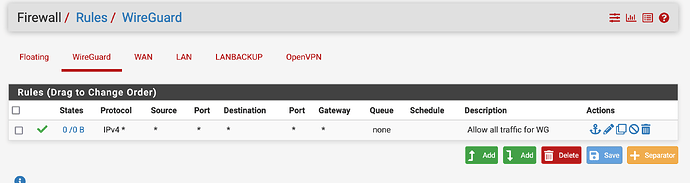
Also have an allow all traffic for wireguard:
I am using pfBlocker but I don’t think pfBlocker is causing the issue as the system log shows it’s being blocked by the default rule, not any pfBlocker rules. This implies to me that I have not setup my WG WAN rule correctly, but I believe I have followed Tom’s video to the T.
Any ideas from the community? Thank you
This is absolutely a great tutorial (!!!), but when I tried to set up WireGuard this way I realized things are somewhat more complicated than what Tom describes using his internal test network. The issue is the ADSL modem provided by my (your) internet provider (AT&T in my case). My modem is configured for “pass though” mode, which means that the internet-facing address of the modem is not the same IP address as the NATed WAN address provided to pfSense, since the modem provides the DHCP address that pfSense uses on the WAN. So for WireGuard I still need to specify the outward facing internet address of the modem to configure clients but need tp specify a different incoming client IP because of NAT. I’m trying to work this all out now.
Follow-up to my own post: my issue getting Wireguard to work had nothing to do with the NATed WAN address. Rather it was because the AT&T BGW210-700 modem still does packet filtering even when in pass through mode. I needed to create a rule to pass through UDP port 51420 traffic. On the BGW210 navigate to Firewall → NAT/Gaming → Custom Services and create a service named “Wireguard” with the “global port range” of the Wireguard port you have chosen and protocol UDP. Then click on Add followed by Return to NAT/Gaming and confirm that your new entry is listed in a table under Hosted Applications. After doing that Wireguard connected just fine for me. Of course it took a while to figure all this out. Running tcpdump on the pfSense command line helped a bunch in determining that packets from the remote Wireguard client were not reaching my pfSense firewall and that I needed to look further upstream for the problem.
Thanks for your great tutorial video!
I configured Wireguard and it works perfectly.
However I do not see ANY Syslog messages sent to Graylog syslog server if a new remote user dials in.
Does the current Wireguard package [0.1.6_2] supports syslog?
I would like to configure an alarm on Graylog syslog server every time a new Wireguard remote user dials in.
Is syslog support implemented in Wireguad package?
So far I saw just the following syslog message for Wireguard, but it does not seem to be related to the remote user dial in event:
full_message
<27>Jun 18 13:34:32 php-fpm[93212]: /wg/vpn_wg_settings.php: Configuration Change: admin@192.168.1.138 (Local Database): [pfSense-pkg-WireGuard] Applied package default settings as necessary.
 https://twitter.com/TomLawrenceTech
https://twitter.com/TomLawrenceTech![]() Lawrence Systems's Amazon Page
Lawrence Systems's Amazon Page![]() https://www.lawrencesystems.com/partners-and-affiliates/
https://www.lawrencesystems.com/partners-and-affiliates/![]() Kit
Kit![]() Learn technology and pass IT certifications with ITProTV
Learn technology and pass IT certifications with ITProTV![]() https://www.techsupplydirect.com/
https://www.techsupplydirect.com/![]() DigitalOcean | Cloud Hosting for Builders
DigitalOcean | Cloud Hosting for Builders![]() HostiFi - UniFi Cloud Hosting
HostiFi - UniFi Cloud Hosting![]() Buy VPN with Credit Card or PayPal | Private Internet Access
Buy VPN with Credit Card or PayPal | Private Internet Access![]() lawrencesystems | creating Tech Tutorials & Reviews | Patreon
lawrencesystems | creating Tech Tutorials & Reviews | Patreon![]() Timestamps
Timestamps ![]()