Clients do not know what they do not know. Sounds like someone is just repeating their documentation, with non reason as to why they want this / why their choice is needed / why their choice is better than your suggestion.
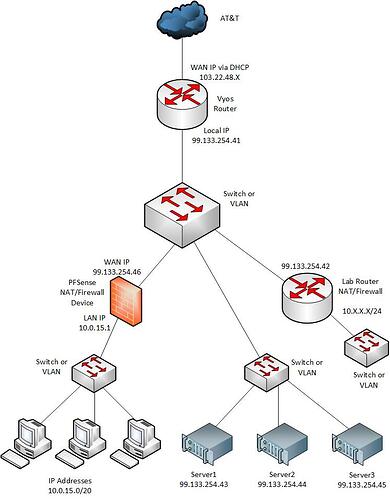
I’m curious as to what exactly are you routing with the “Lab Router”? What are the IP addresses/subnet on the other side of the Lab Router? The Lab Router is a separate device from PFSense right? One side of the Lab Router is assigned 99.133.254.42 with a static/gateway 0.0.0.0 pointed to 99.133.254.41 right? What’s on the other side of this Lab Router? The side where these clients that can’t ping…
Y-ASK
Reading all of this over again it almost reads that you want to have to two gateways on the same subnet 99.133.254.41 & 99.133.254.42 both on PFSense. Not to mention the IP address 99.133.254.46 that will be the NAT’d IP address for the 10.X.X.X subnet. All of this running on the same PFSense box. If this is the case then I’m out and wish you luck… This is a crazy setup even for someone who really knows their stuff.
The Lab router just doesn’t get the address properly, it’s Linux based and with a quick ifconfig, it lacks a WAN IP, it has to do with my pfsense config.
Please clarify, is the lab router also running PFSense?
Also, in this case, there should be no DHCP running on the interface/subnet with the public IP block, so all IP information must be programmed into the devices (lab router and servers) completely - that means IP address, subnet mask, default gateway, DNS servers, and NTP server - all of the things that are usually provided by DHCP.
Please follow the steps and answer the questions that I previously posted, they are the steps I would take if I was troubleshooting this network directly. I can’t provide assistance without proper information.
I was asked via PM how I would configure everything so here it goes:
You can use one “Managed” switch and separate the different subnets into VLANs. Both Vyos and PFSense are free to download and use. For the “Lab Router” you will need to use a non-internet-routeable IP address subnet. If you want the devices on this non-internet-routeable subnet to be able to route to the internet you will need to NAT the traffic as it goes through the router.
Y-ASK
I agree with this design - it is much more conventional. Having a dedicated router to handle the public IPs is always easier. I have set up what was originally asked for, which is why I was trying to explain how to make it work.
Yeah, the problem with trying to do it his way is to have three public IP addresses from the same subnet configured as three bridged ethernet ports with those associated public IP addresses will be difficult to implement. Especially if one needs to be NAT’d for the 10.0.15.X/20 subnet, one needs to just be a routable gateway for the servers, and one needs to be one side of some sort of Lab Router. Can you imagine trying to explain “hairpining” in order to get a fourth ethernet port with 10.0.15.1 NAT’d so that traffic flows into and uses 99.133.245.46 as their public IP address. And then apply Firewall rules to that path. All of this on the same single device. I’m not even sure if you can have three separate ethernet ports with different addresses from the same subnet. Like Bruce said it would have to be bridged but if they are bridged wouldn’t it be difficult to separate them with NAT and Firewall rules. I mean difficult to explain…
Y-ASK
You’ve hit the nail on the head. And honestly, the originally requested network design would be easier to implement with a Mikrotik router because they offer unlimited control over this type of odd routing setup. But I do not recommend someone who doesn’t fully understand routing to try RouterOS. Better to stick with more conventional routing operating systems like VyOS and PFSense.
VyOS is a good choice for the “just a router” because it will have less stuff set up by default that you have to disable/change in order to have a subnet not be NAT’d.
What if i just skip the servers, i just want to get my lab router connected, what would be the easiest way to have a WAN IP block and have it go to a OPT1. I also have a edgerouter i could use as the main router but my linux routing skills are limited that’s why i wanted to try this with Pfsense but maybe the Pfsense skills are about the same. And the Lab router is a UDM Pro hehe. And also there is absolutely no documentation on what i’m trying to do.
I already have the 10.0.15.x/20 subnet working and its already attached to my 108.14.24.0 public IP that isn’t my problem. My problem is just the static IPs and how to setup a bridged interface that uses my public IP block.
The EdgeRouter is based on Vyatta which was also the source for VyOS. The Edge CLI is fairly well documented, and overall it is a fairly normal router.
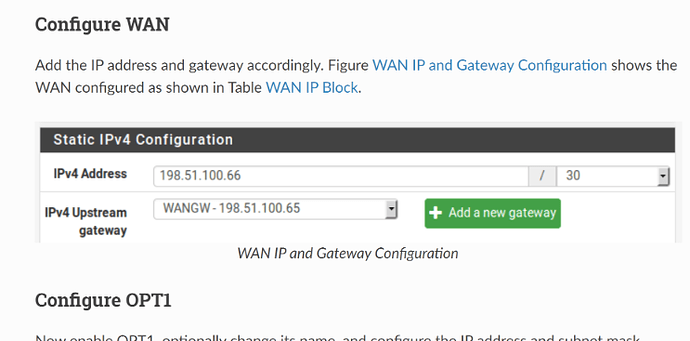
Configuring OPT1 with a public IP subnet is literally what @LTS_Tom shared with you 3 weeks ago at the top of this thread: https://docs.netgate.com/pfsense/en/latest/recipes/route-public-ip-addresses.html - just wherever they mention the /30 subnet, that is the IP/subnet you are getting via DHCP (108.14.24.0).
Followed that to a T, could not get that to work. Except for the fact that i had my firewall rules set to allow anything through, don’t need to DMZ since its a firewall.
I don’t know what to tell you then.
What should my firewall rules look like to allow everything through on just my static block? I also can’t do this:
since it would break my connection to AT&T. What do need to do instead of changing the WAN IP, add a virtual IP?On WAN interface:
Source: Any
Destination: IP Subnet - your /29 subnet
On OPT1 or bridge interface:
Source: (interface) network - this is the same as manually putting in your /29
Destination: Any
If you want to prevent your public IP hosts from reaching your private LAN then put a block rule for that above the allow all rule.
If you’re suspecting a problem with firewall rules, then you should watch the firewall logs as you run your tests. By default it will log dropped/blocked packets (for the default deny rile hidden at the bottom of the rules list) and not log passed/accepted packets. To log packets affected by your own rules (drop or accept) enable the logging in the rule itself.
So then don’t. I already told you that where the guide talks about a /30, that is where you have you DHCP. So you skip that “Configure WAN” section.
Finally got it working, didn’t have my firewall rules right, you guys definitely helped, thanks so much to @brwainer and @Y-ASK. Really appreciate, finally got a whole day to work on it. This link is also very helpful for people trying to do the bridge interface.
I’m glad you got it working!