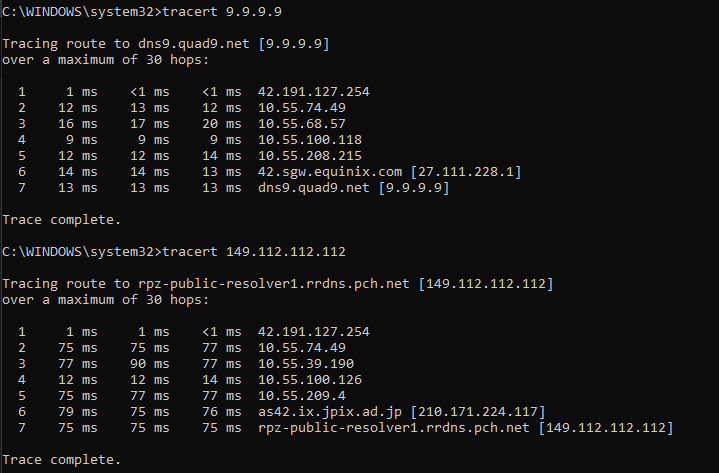
Hi, Bob. I’m Bill Woodcock, John’s counterpart at PCH. As he said, if you’re reaching a server 188ms away, rather than the 3ms-5ms you should expect if you were reaching the Bangkok server, it’s because your ISP is choosing to send the traffic that way. Can you post a traceroute so we can see where it’s going? Maybe we can reach out to them and try to get them to fix the problem.
As Jefronty points out, there’s a second IPv4 address, 149.112.112.112, but there’s also a primary and secondary IPv6 address, 2620:FE::FE and 2620:FE::9, and you should definitely configure those as well, since you may have a faster or more reliable path over IPv6 than IPv4 in some cases. May as well take full advantage of it!
As John says, it’s up to your ISP to decide where to send your traffic. You can see the current server clusters here. The closest ones would be Sofia, Tirana, and Istanbul.
thanks @woody.
Earlier today, I reached out to GR-IX based on John’s recommendation. You might hear directly from them for setting up a POP in Athens.
With respect to the closer than London POPs, keep in mind that the term ‘balkanization’ remains true even on internet peering. ISPs prefer peering with LINX rather than their counterparts in nearby countries ![]()
I spoke with the CEO of GR-IX. It looks like there’s a bureaucracy loophole that stopped PCH having a POP at GR-IX that started 2 years ago. I will send an introduction email. I can find the email of woody via his public slides ![]() but John’s is nowhere to be found!
but John’s is nowhere to be found!
John, please PM me your email address
Marcos
This is a really interesting video and topic.
I do wonder though, if the sample size might be a bit too small and as mentioned by others stale.
I know @quad9dns can’t and/or won’t confirm that this list may be one of their intel sources, but for them to block or not resolve all but a few of the domains and other services are resolving does it not say that this list may in fact be a list used by Quad 9 for their intel. It may be an idea to compile a bigger list of sites and then run the test again.
Have a great day!
CR
Hi Woody,
My pings are now 29 ms, which means that the resolver is most likely Singapore, and the tracert confirms that:
C:>tracert -d 9.9.9.9
Tracing route to 9.9.9.9 over a maximum of 30 hops
C:>tracert 9.9.9.9
Tracing route to dns9.quad9.net [9.9.9.9]
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms wpad.nsasia.co.th [192.168.200.10]
2 3 ms <1 ms <1 ms myrouter
3 2 ms 1 ms 1 ms 203.146.1.133
4 2 ms 2 ms 1 ms 203.146.97.30
5 4 ms 3 ms 3 ms 202.183.233.61
6 2 ms 2 ms 2 ms 202.183.233.38
7 2 ms 2 ms 2 ms 202.183.138.126
8 30 ms 32 ms 30 ms 7568.sgw.equinix.com [27.111.228.68]
9 34 ms 33 ms 36 ms 42.sgw.equinix.com [27.111.228.1]
10 30 ms 30 ms 29 ms dns9.quad9.net [9.9.9.9]
Trace complete.
Should I have reason to expect this could be improved if my ISP used BKNIX?
Thanks
yup using 9999 and the 149
Don’t use IPV6 nor do my clients, no one really wants to deal with it.
Using 1.1.1.1 from cloudflare to protect against malware is wrong because this is not the right ip.
Cloudflare have 3 tips protections.
Family (Normal DNS)
1.1.1.1
Malware
1.1.1.2
Malware & Porn
1.1.1.3
Plase run the tests against 1.1.1.2 to be right and just to cloudflare!
You should consider watching the video and reading through the previous posts where all of that is explained.
He did test both. His spreadsheet has .1 and .2 both in there.
Also, on the topic of active threat feeds. Here is a sample that has bad active bad malware that I just verified. (don’t download it unless you know what you are doing) This was posted 14hrs ago AlienVault - Open Threat Exchange and as today 6/4/20 @ 15:34 EST Cloudflares 1.1.1.2, Cisco Umbrella (not OpenDNS) both resolved the address, Quad9 did not and DNSFilter replied with “The domain 198.251.90.71 is blocked due to a network filtering policy.”
I need to work on building some automation for this testing because one single IP is not at all a high quality or even good test. I just wanted to say thank you again for everyone who keeps posting and helping out with this and to let people know I am not done yet. ![]()
FYI ISC pulled the malicious domain feed today based on feedback from this project.
Hmm, so them pulling their lists makes me wonder about the accuracy or conclusions of this “experiment”. I’m not doubting any methods that were used it just seems the “data” list might not represent the best set to test against. I’m aware Tom clearly stated he was wanting other list sources but no one at this point had volunteered any alternative. I just wonder what conclusions to draw – if any – from this elegant test.
I ran into a site called Threatcrowd that is interesting too. It maps out domains/subdomains that perpetrate attacks and spam.
I came across it when researching a domain that fished an old email account I stubbornly held on to way too long. As a result of the fishing, I dumped it, swapped all my accounts over to new address and picked up a secure email provider for important communications.
https://www.threatcrowd.org/domain.php?domain=exacttarget.com
This domain was the source of the fishing attempt. Apparently a lof ot spam or fishing originates from here.
Hi there, thanks so much for coming here and posting about quad9. I have been load balancing between quad9 and cloudflare dns for awhile now but thinking about switching to quad9 exclusively. I have a question about routing though. When I do a traceroute to 9.9.9.9 I get consistent results that I am routing to your Atlanta POP which is great because I am located in Nashville. However, whenever I do a dns leak test it always shows an IP for the Miami POP? Could the dns leak test just be getting it wrong? Is there any way to tell what POP I am connected too? According to quad9 locations both POP’s are up. It does add a decent amount of latency to have to round trip that distance to make a dns request so I’ve been trying to figure it out. Thanks again!
Hi Networking-Nerd389. I would expect that your traceroute and DNS queries would be consistently going to the same location, so something is amiss there in the two tests. I’d suggest doing a traceroute to 9.9.9.9 and then also from the command line doing a “dig @9.9.9.9 CH TXT id.server” which will give you the node & POP which answered that particular query. While the node will often change, the POP should be very consistent, though it may shift from day-to-day but not minute-to-minute (usually.) In your traceroute, be aware that sometimes inverse address DNS is not always telling the truth or is misleading. Also note that load balancing between Quad9 and Cloudflare might give you some redundancy between organizations, but you’ll have inconsistent protection results if your systems automatically shift. And are you really load balancing or just setting one as backup? Different stub resolvers behave differently - some will actually load balance, while some will just send all the queries to the first one listed and only use the alternate if the first one is non-responsive. In any case, we’d suggest picking one organization and just using the secondary addresses of the same organization’s servers as the “backups” (149.112.112.112 and 2620:fe::fe for Quad9.) - JT