Hello K-rolll - Quad9 also has a node in Malaysia (Kuala Lumpur) at the Malaysia Internet Exchange. Seeing traceroutes like this is not unusual, and is a result of decisions outside our control. Many large incumbent telecom firms choose not to deliver traffic in the most efficient way for various reasons. We could be getting your traffic inside of Malaysia, but that is a decision that is entirely under control of Telekom Malaysia. (https://www.peeringdb.com/ix/250 - both AS4788 and AS42 are on that IX) However, since you are a customer of Telekom Malaysia, perhaps you could ask them - we do not pay them, so our requests for interconnections are not as interesting to them. You do pay them, so maybe they have an interest in keeping your business. This is one of the secondary goals of Quad9 - to improve connectivity by encouraging the use of local IX interconnections.
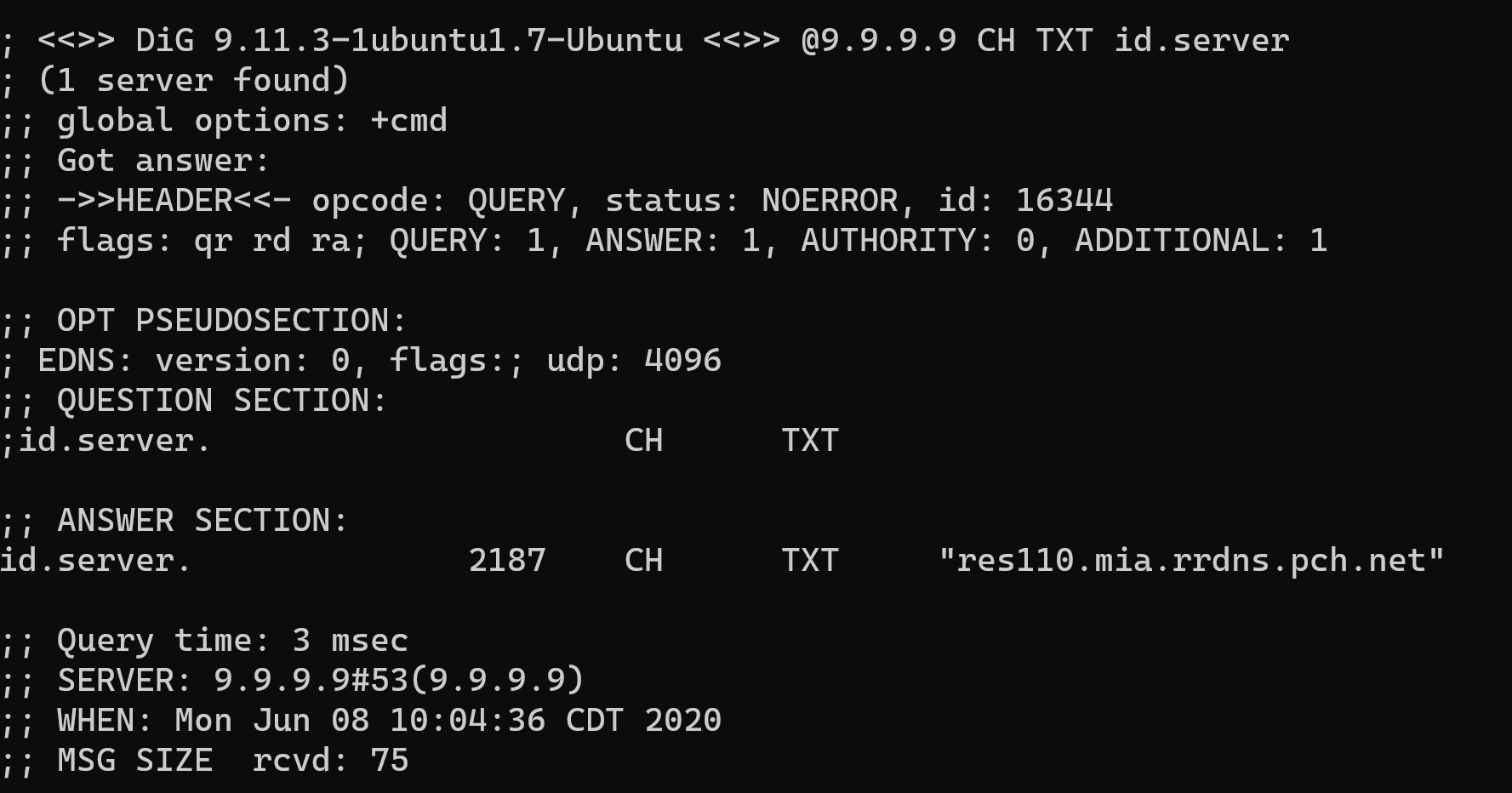
Ok thanks for the info. I am using DNSCrypt proxy with DoH and I mainly use cloudflare and quad9 for performance and privacy (no logging), though now I’m leaning more toward quad9 because of the malware blocking. This is how DNSCrypt proxy load balances, “Load balancing: pick a set of resolvers, dnscrypt-proxy will automatically measure and keep track of their speed, and balance the traffic across the fastest available ones.” I ran the command you suggested and still seem to be getting the Miami POP even though the Atlanta one is closer. I suppose this could be blamed on Comcast’s routing but I don’t know for sure. I’ll attach the screen shot below.
Right now, I’m using Cloudflare coz it’s the fastest filtered DNS for my ISP (route to Malaysia IX). I was hoping Quad9 fast too ![]() I’ll try to reach them. Thank for your response John. Quad9 ftw!!!
I’ll try to reach them. Thank for your response John. Quad9 ftw!!! ![]()
In terms of up to date DNS blocking lists, I have been using this one for some time now - https://oisd.nl/. It goes a little beyond just blocking malware, also blocking cryptojacking, malvertising, phishing, telemetry, etc but has never broken anything I needed to work.
His methodology seems fairly sound in terms to keeping his list up to date. It can be found in the reddit post here.
Might be of some value to those looking to test against a well maintained list. If you’re looking to pick out a particular type of list, you can see the lists he’s pulling in and pull some malicious domains from there to test against, just be careful of course.
Just to add one more: https://firebog.net/ is a nice collection of blocklists grouped by categories
I just came to register and say thank you for the video, and it is great to see the community working together.
Just wanted to follow up on this. I decided to test this on my firewall since it is actually doing the DNS queries on behalf of my devices and it is consistently showing answers from the Atlanta POP. So it looks like I’m being routed correctly after all. I cleared the DNS cache on my firewall and switched to using quad9 exclusively a few days ago and it could be placebo but responses have been very fast! A little better than I was getting before plus the malware protection. Thanks again for a great service!
@Mike-DNSFilter Does DNSFilter have plans for home users? instead of per user pricing
It seems that Suspicious Domains is no longer available.
Is there an alternative list that I could run against my Untangle / pfSense combo?
So I’m curious if a plug-in that rejects domains without a recent lookup would cause issues with network troubleshooting. I can think of a few potential issues, but those are likely limited to those in development environments where you don’t want to push an A record yet.
That being said, I’d be willing to push it to a few of my firewalls if it had a “log only” mode where I could see the potential impacts before I enable it. I may have to check out his module and do a little coding.
Hey @quad9dns
Just a reminder about your pfsense project mentioned in the video being uploaded to GitHub ![]()
Thanks - will try to get to it shortly. On the road for a bit, but maybe this weekend. Side note: there is a project called “Portmaster” which has this functionality. I haven’t yet had time to test it out, but might be worth looking at as well. https://github.com/safing/portmaster
Morning from Cape Town South Africa @quad9dns. I’ve tried contacting your support through the channels on your website and also my ISP through the NOC email but having little success. It seems that your anounces at CINX in Cape Town have all but stopped but your website shows all is running. If and maybe you can have a look or just point me to someone whom can have a look that would be wonderful. Thanks again for a great service.
Edit: Had a response from PCH that some hardware has died and are in the process of replacement but no turn around time to mention.
Hi MDE86 - Looks like a hardware issue in CPT, and we’re trying to work out replacement gear. Hopefully you’re routed to a nearby .za city (depends on your ISP) and as soon as things are back online you should automatically switch back if that’s the best path. The slow response on the support side is them waiting on a hardware estimate, but it’s taking longer than anticipated.
@quad9dns Many thanks.
Hi sir, We don’t have a good latency here in the Philippines or maybe I need to change something?
Residential ISPs in PH have decided that least cost routing should be taken literally and the cheapest routes be chosen, no matter what.
Example: Globe Telecom AS4775 from Cebu City route to Singapore via Japan, then Los Angeles, then back to Singapore. What could / should be 40-80ms becomes 200+ ms. Play around here and do some MTR from the Cebu node to see what I mean.
You will see that for Quad9 they go to Seattle first… Where they could just go to Tokyo, Seoul or Singapore.
9.9.9.9 | MTR from Globe Telecom AS4775 in Philippines, Cebu 11. AS19281 dns9.quad9.net (9.9.9.9) 0.0% 0 10 10 182.8 182.8 183.1 183.4 0.2 183.1 0.3 0.1 0.3 1.1
Loss% Drop Rcv Snt Last Best Avg Wrst StDev Gmean Jttr Javg Jmax Jint
1. AS??? 10.91.2.198 0.0% 0 10 10 20.5 16.6 20.0 31.8 5.0 19.5 2.1 2.4 7.9 17.7
2. AS??? 10.205.252.154 0.0% 0 10 10 17.0 16.2 16.7 17.1 0.3 16.7 0.3 0.4 0.8 3.6
3. AS132199 180.190.228.5 0.0% 0 10 10 17.0 16.5 16.9 17.1 0.2 16.9 0.1 0.2 0.6 1.3
4. AS??? ??? 100.0 10 0 10 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0.0
5. AS??? ??? 100.0 10 0 10 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0.0
6. AS1239 sl-mpe50-sea-.sprintlink.net (144.228.93.141) 0.0% 0 10 10 183.2 183.2 183.8 186.4 0.9 183.8 3.2 0.8 3.2 7.4
7. AS2914 ae-19.a01.sttlwa01.us.bb.gin.ntt.net (129.250.8.149) 0.0% 0 10 10 185.9 185.5 187.3 197.3 3.6 187.3 0.4 2.7 11.1 19.4
8. AS2914 ae-2.r05.sttlwa01.us.bb.gin.ntt.net (129.250.5.97) 0.0% 0 10 10 180.7 180.4 180.7 180.9 0.2 180.7 0.3 0.3 0.6 2.3
9. AS2914 ae-1.a00.sttlwa01.us.bb.gin.ntt.net (129.250.5.134) 0.0% 0 10 10 184.6 184.1 184.5 185.3 0.4 184.5 0.1 0.4 1.2 2.8
10. AS2914 xe-0-0-50-1.a00.sttlwa01.us.ce.gin.ntt.net (129.250.204.110) 0.0% 0 10 10 201.3 200.8 201.3 201.5 0.2 201.3 0.3 0.2 0.6 1.8
11. AS19281 dns9.quad9.net (9.9.9.9) 0.0% 0 10 10 182.8 182.8 183.1 183.4 0.2 183.1 0.3 0.1 0.3 1.1
PLDT / Smart seem to do similar stuff. There is no competition in PH so they do all sorts of crappy things.
Google and OpenDNS seem OK from PH, Cloudflare and quad9 are borked and this is most likely not something quad9 can resolve.
1.1.1.2 (1.1.1.2) : xmt/rcv/%loss = 10/9/10%, min/avg/max = 183/183/183
dns.google (8.8.8.8) : xmt/rcv/%loss = 10/10/0%, min/avg/max = 48.2/48.4/48.7
dns9.quad9.net (9.9.9.9) : xmt/rcv/%loss = 10/10/0%, min/avg/max = 182/183/183
resolver1.opendns.com (208.67.222.222) : xmt/rcv/%loss = 10/10/0%, min/avg/max = 58.4/58.8/59.5
Only one good ISP exists in PH (RISE, AS63927) but they don’t do residential.
when will you have a data center in brazil?