Hi all,
First post here. I heard about this forum from a podcast @LTS_Tom participated in (uncast with ed).
Briefly about me:
I’m a long term “homelaber” ![]()
I was not professional in IT/Security field but an enthusiast.
I’ve been setting up home networks for me and my family, building pc, setting up smart home,… for a long time.
I even managed my small company it for 10 years.
For various reasons i’m making a move to career change in cybersecurity. And as you need to start somewhere, i’m completing google cybersecurity certificate.
Logically i want to enhance my home network security; obviously for security concerns but also to learn.
I decided to start with network segmentation. I watched videos and read articles on the subject. I think i understand what it is, the purpose and the way to define vlan.
But what i miss is how to assign vlans (particularly to dockers).
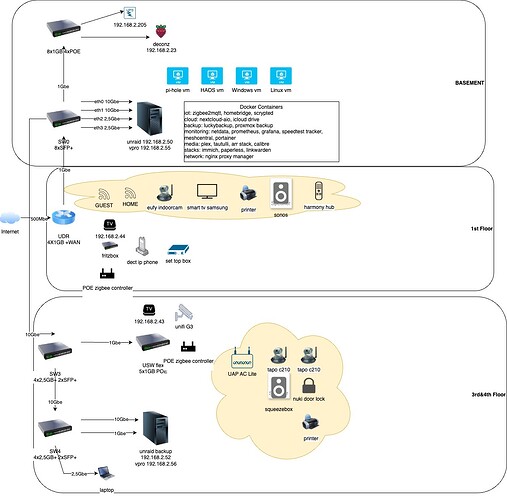
To be clear i’ll first summarize the gearr and services i have in my network.
For the network i have an unifi dream router, usw-flex, uap plus 4 non unifi vlan capable switches. I also have a usw48 poe but decommissioned for now.
As i moved from a big house to an apartment i had to reduce the number of servers (from 6 to 1, actually 2 but the second is a backup server only powered up when needed).
My server runs unraid. It has 2x10G and 2x2,5G interfaces. 1 2,5G is dedicated to vpro.
It runs a few vms (home assistant, jeedom, pihole, windows) and many docker containers (around 70 some of them published through nginx proxy manager like nextcloud, homeassistant or plex).
I also have a bunch of devices like laptops, iphones, tablets, smart tv, apple tv, cctv cam, poe zigbee controllers, logitech squeezebox, nuki and other smart devices.
For now i have a flat network.
My first step would be to leverage vlans.
I plan to keep it simple so i guess default, guest, iot and cctv vlans are a good option.
For the devices it’s not difficult. But for containers and vm what vlan do i need to choose?
let’s talk about home assistant vm. It needs to communicate with every smarthome device so logically i have to put it into iot vlan.
It also need to communicate with my zigbee2mqtt, mqtt, scrypted, homebridge dockers. So i would create a docker network on this vlan and put these containers in it.
Can i assume unraid doesn’t have to communicate with containers trough networks ? Control is made trough docker.sock and storage need through path mappings.
But my laptops and phones need to communicate with homeassistant and the containers.
I read somewhere tom put smartphones in iot vlan.
Where do i put laptops ? in the default vlan and then define a rule to authorize communication from default to iot ?
For NPM i would put it in he same vlan as the published service (iot for plex and home assistant). But for nextcloud ?
All these questions is why i have been waiting to tomorrow for so long to set up vlan ![]()
And this just the first step i also want to implement sso, install siem tools, …
I hope that i’ve not been too long ![]()
![]()