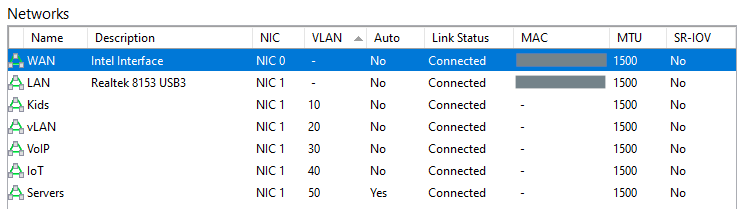
I have a VDSL router in bridged mode connected to an Intel NUC. The NUC is then also connected to an Netgear GS724T switch. A UniFi AP completes the hardware aspects.
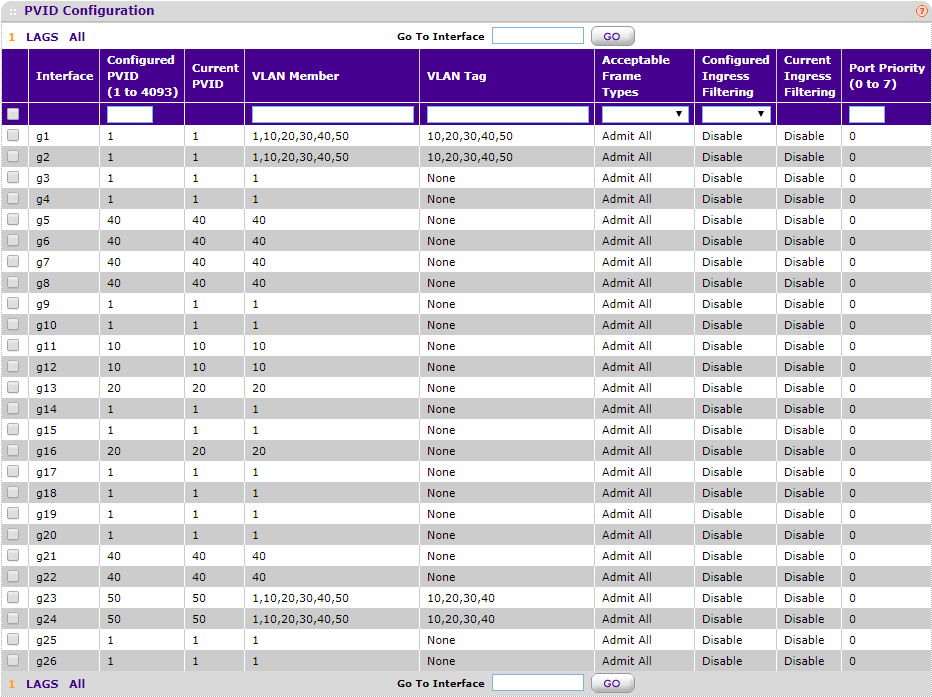
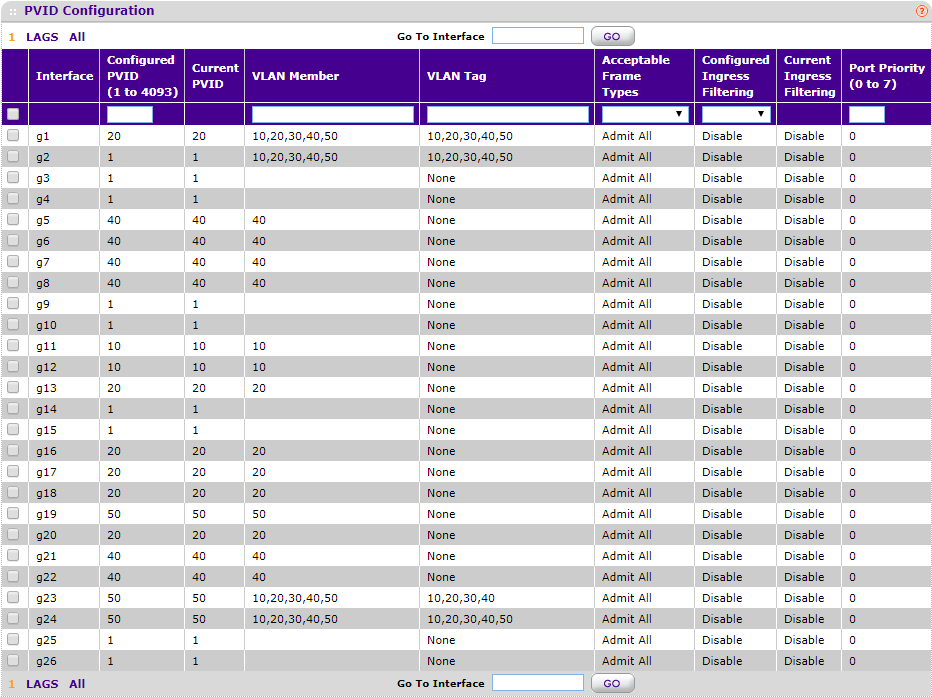
The NUC (XCP host) is connected to port 1 of the switch with the UniFi AP-AC-Pro on port 24.
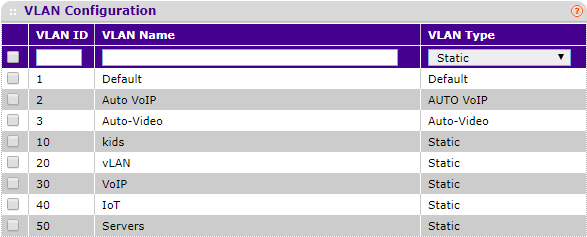
I then defined 5 VLANs on the switch.
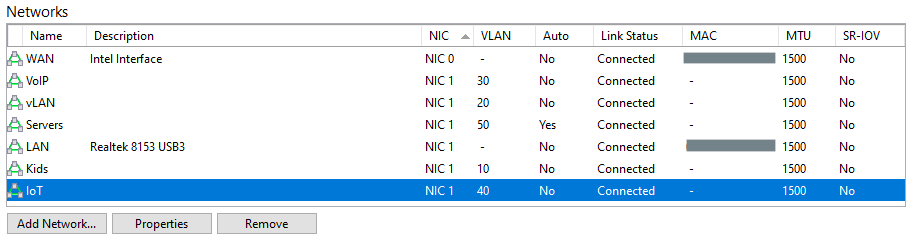
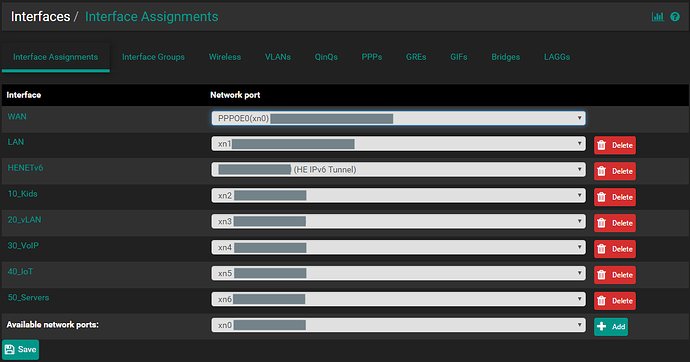
In XCP a network is created for each VLAN. This seems to be the only way as to address frame tagging within pfsense via a trunk interface.
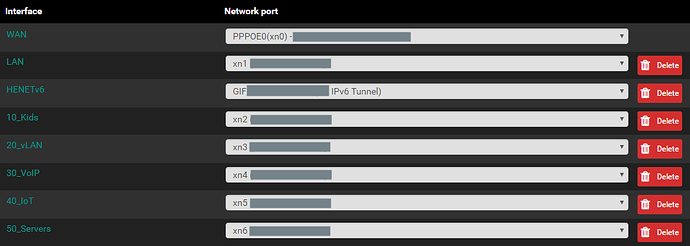
Each network (as created within XCP) is then presented and can be assigned as an interface in pfsense.
VLANs cannot be specified within pfsense
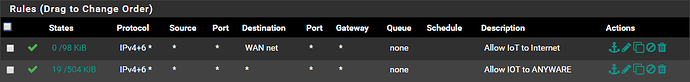
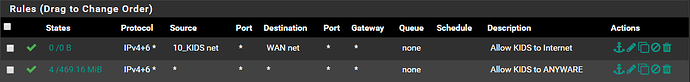
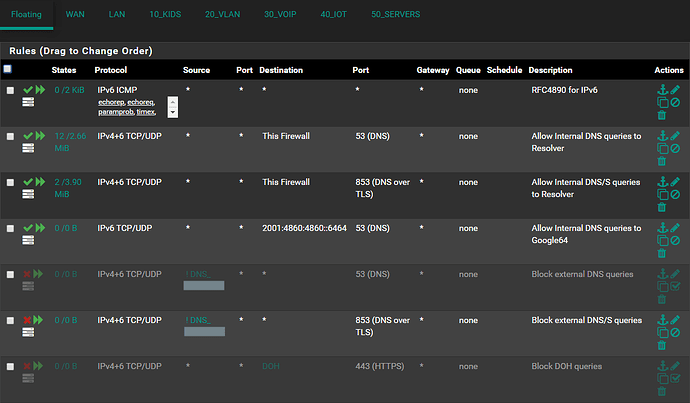
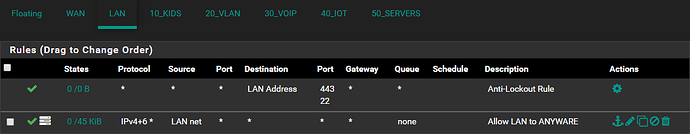
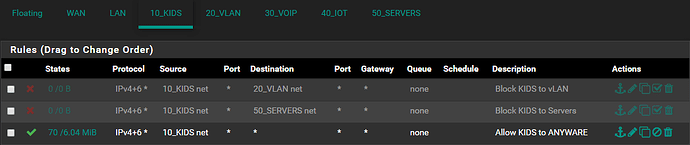
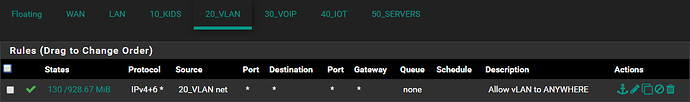
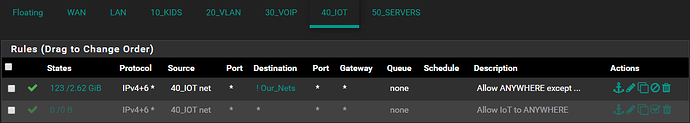
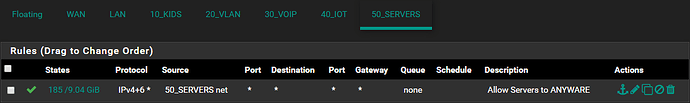
Everything works perfectly fine at this point should there be a rule allowing anything anywhere on each interface.
However, the moment I amend the “Allow ANY to ANYWHERE” rule by specifying a SOURCE or DESTINATION, this new rule gets skipped.
Inter VLAN traffic fails the moment an inter VLAN rules is created, yet does traverse fine should a “Allow ANY to ANYWHERE” rule be specified.
My head truly hurts on how I’ve banged it continuously against this issue. Any guidance would be greatly appreciated.