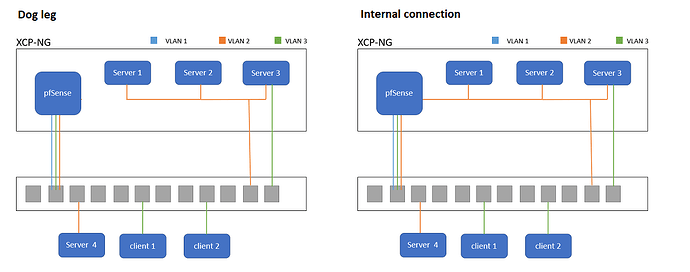
I have a fairly simple network with multiple VLANs. I’m wanting to take my physical pfSense machine and virtualise it in to my existing XCP setup. At present it is just a dog leg, but with XCP-NG having sketched it out (below) I’m a bit worried about how this might be handled having recently had (unrelated) issues with STP , something I know little about.
VLAN 2 is for my servers / management and most access is restricted. Some of my clients can access certain ports but it is controlled via pfsense. It’s used for inter-server communication, mainly NFS where I don’t want to have everything go via the router.
VLAN 3 is for my main client machines. They mostly talk to servers via pfsense, but for SMB I expose an adapter from one of my servers on to VLAN 3 so SMB does not have to go via the router.
I could virtualise my pfSense as a dog leg, but then I would have to come out of XP-NG then back again. It would make sense to do some switching internally.
What I’m wondering is if XCP-NG, Unifi or pfSense going to have any sort of issues with this setup?
If the serves and pfsense are on the same interface in XCP-NG then the data will not leave XCP-NG to go through the switch.
Yes, the idea would be they are on the same internal network, but that could also be attached to an external port.
So if there is a direct path from server 3 to 4 over the switch / vlan, it would not take this route, it woudl go via pfSense?
If they are on the same subnet then it will go through the same port.
Yes so the server subnet is the same 192.186.11.0/24 and all on the same VLAN.
It would make sense that the traffic went via the red route because it is on the same vlan / subnet without any router hops, but it could easily go via the router.
How does it know it can reach it via another port and without a router hop?
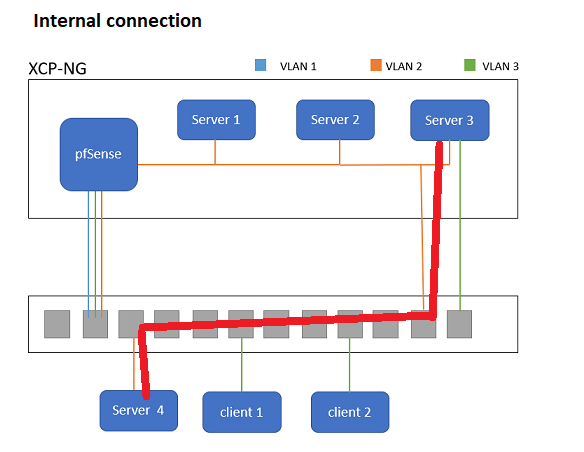
Devices go through the router when they are on different subnets, if they are on the same they don’t.
ok great thanks for confirming. so how does it work?
is the switch maintaining this in a MAC / state table so it knows what it can switch where?
how does pfSense “know” to send it via the internal XCP-NG link rather than back out on to the switch when it has two paths like this?
It’s how layer 2 switching works in Xenserver.
that’s a really useful document thanks for sharing. So basically it is like any other setup where you might have a handful of switches and a router connected to your network somewhere. the fact it is internal or not does not really matter.
1 Like
Hi @LTS_Tom
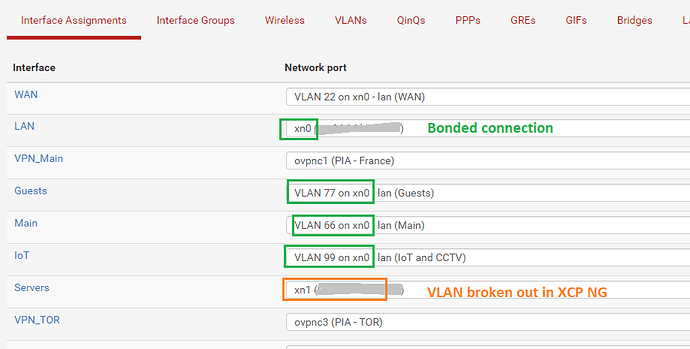
I note that I can now add VLANs to pfSense Interfaces on an XCP-NG interface.
I haven’t got it to work properly but an updated video on this would be awesome.
I was playing a round a bit more today, a bit more info for anyone interested and didn’t know this …
I have a Servers, Main, IoT, Guest and WAN all setup as VLANs then the usual LAN.
I then have 2 1Gb ports going to XCP-NG bonded together.
I add this to my pfSense and setup my VLANs on it.
Except for “Servers” which I break out as an XCP-NG network.
This does simplify the number of networks in XCP-NG, you just need to remember where you are defining / setting up your VLAN.