Im thinking that maybe wireguard does not act the same as openvpn
Ive setup the split tunnel before with open vpn and it all worked with pia, i have no such luck with wireguard.
i moved to Proton vpn becuase its faster and it allows you to generate wireguard configs really easy
I see a lot of people making videos on how to use wireguard to connect to the router from anywhere and thats fine and all, but i don’t see any tutorials on hot to make this behave like a openvpn / split tunnel where traffic i choose from my lan is routed through the vpn provider then to the wan from my network like the tutorial with pia useing vpn, i see people say it can and that they have done it soo i assume it can. i think they call it client to server with wireguard? not really sure
maybe I’m overthinking the setup, maybe it doesnt work the way i think it does, id love to know cause man im stopmed, been trying for 72 hours and i just cant figure out
Any help would really be nice
running pf-sense CE 2.8.0 and attempting config with proton wireguard config
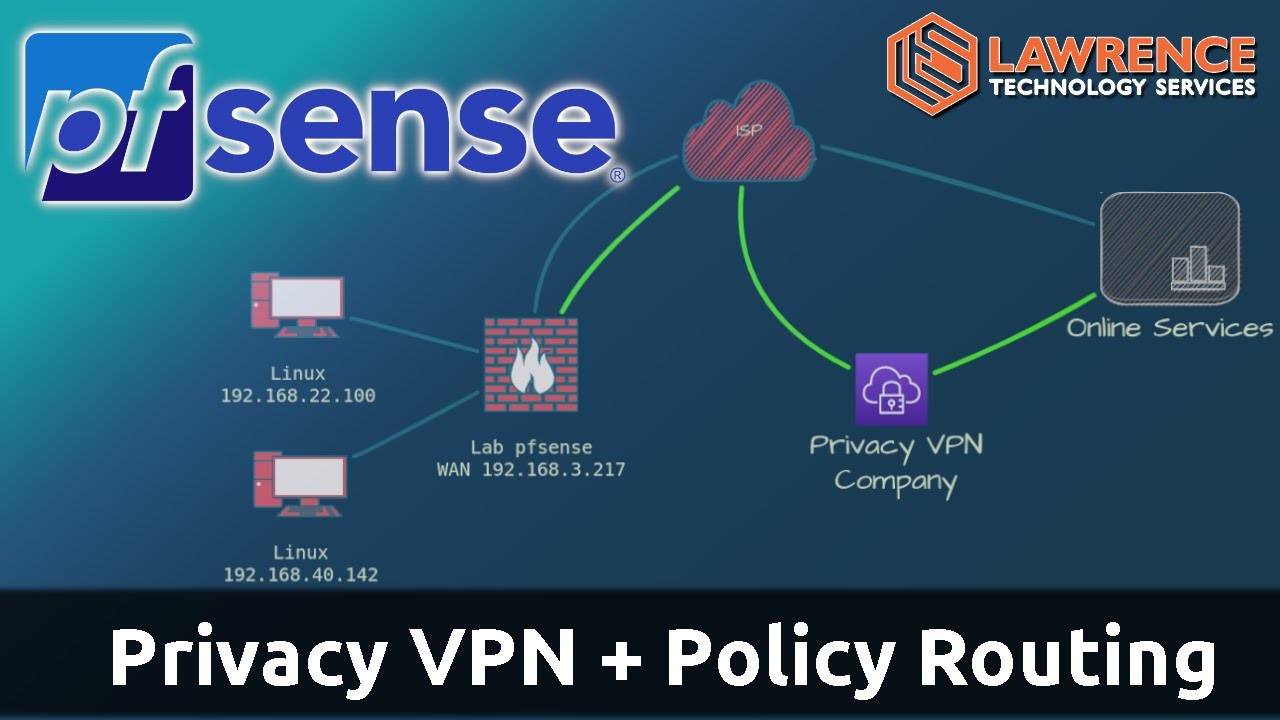
In theory this video should work if you build it out with Wireguard instead but I have not tested that because I still use OpenVPN as it’s easier.
Thank you for the reply and tutorial
it seems as if with wireguard it doesn’t do as openvpn, from everything im seeing wireguard requires each client outside of itself to be setup with these special keys that are generated, I was hoping to not have to go through all that hassle. is there way to allow clients from in my network to use the wireguard tunnel without having to supply each client with a special key for wireguard itself
It’s really unclear what you are asking for. Are you saying for clients trying to connect on OpenVPN to your pfsense that hosts a OpenVPN server? Or are you saying that you have OpenVPN client setup on your pfsense and you want to policy route traffic through that tunnel?
I’m glad you pointed that out because i wasn’t really sure how to ask for what i was asking for, LOL
I think i finally know how to ask the question in hopes of getting the solution i seek.
If i understand wireguard properly it can be setup as a server or client. The only tutorials i find on wireguard as relates to it and pfsene is how to set it up as a server. I on the other hand want to set it up as the client and have systems I choose within my network use wireguard while it is connected to the vpn provider as a mean of getting internet connectivity aka (split tunnel)
Hopefully that makes sense.
Its pretty clear to me that pfsense has to setup in a client/server config for this to happen.
I’m just not certain how to make it so
I think there is some terminology being used wrong. Split tunnel means that a device can access VPN resources while also access local resources.
any time you want a device to go over a privacy VPN you typically don’t want split tunnel. You would want all your traffic to go over the VPN. Otherwise there is no purpose.
Tom explains how to do policy routing. Meaning how to configure a device to go over the VPN tunnel and block it from send traffic out the normal gateway.
Proton actual has a guide on how to set this up with pfsense.
Just know on step 7 that if you want to selectively choose which device goes over the tunnel you have to modify the firewall rules on what devices go out the tunnel and the rest of them go out the normal gateway. But if you want everything to go out the VPN then do what they did in the article.
Okay I see now. Or at least I think I do. Okay so the correct terminology is policy based routing. And as relates to step seven that is where I would define what systems utilize what portal. I think I better understand.
I will give that configuration a try and report back. I’m kind of nubish to this entire policy routing with a VPN thing.
Thank you for taking time to assist me.
You got it. When you get to step 7 you’ll want to refer to Tom’s video about the firewall rules and creating a kill switch.
1 Like
I will try as have been suggested later today when i wake up and will report back the progress
I am happy to report that i finally got it working.
So it turns out that I did everything proper.
And I read somewhere here on the forum where Tom said that if there is no handshake between the servers that there is a key issue
So I deleted my old wire guard config and generated a new one and this time I made sure that my key was proper however it still failed to connect.
I then read on the proton sight where it said it is preferable to have a fresh install before trying to do the wire guard install
My PF sense install was indeed flawed.
So I thought to myself like okay no biggie I’ll just reset the factory default.
I did a factory reset and when it came back up it retained a good amount of my original settings. Just let me know that something he went all the way wrong with my PF sense install is it has been installed and upgraded and rewritten over many times.
So I just said whatever. Nuclear option it is.
I then went downloaded the 2.8.0 image. Performef the fresh install
But this time whenever I went to set up the wireguard config which was extremely easy and quick, Even more so than open VPN, although I’d like to note that I’m running the CE edition but I’m certain it’s easier for those with I guess the pro or paid for addition because they can import open VPN generated configs.
Anyway, I then went set the alias, firewall rules and kill switch.
In this time when I test it everything was proper.
Thanks A lot, I was totally stomped I mean I just couldn’t figure it out for the life of me and I had to keep researching and with the help of everyone I finally got it up and running quite easy like 10 minutes 
 crazy….
crazy….
1 Like