Here is my take on all this.
Part I - OPNsense revisited
I’ve decided to retry OPNsense that I had black flagged in 2019 for being really boggus and behaving often eratically while I was teaching network security in college. I was already a pfsense user at that time and was satisfied with it so OPNsense was new and tried it.
So last weekend, I removed pfsense+ that was running on a 8700k rig with 32GB and 2 x 10GE NIC that was doing marvels for my home lab, and installed OPNsense. After 30 minutes of fiddling with it and having discovered that I had to enable some tunable to bring up my Chelsio 10GE NIC, I also read that this problem existed since a few years already with OPNsense. I thought to myseld “this doesn’t bode well” if this is still maybe not properly recognized by the kernel. Strike one.
I continue setuping my network and when I was about to clean up some auto-generated rules, that’s when I remembered that this was an issue with OPNsense opening/allowing way to many things on every network. And you can’t just close those ports if you didnt need them. For me, every port facing the Internet must have zero opened port - so no IPsec NATing, etc. But there is no way to remove those on the WAN port. Same for the LAN ports who has other “built-in” rules. Strike two.
Time for some benchmarking as I always do when basic stuffs is in place. Well well, as in 2019 on slower links, even on the same hardware that pfsense+ was running, I couldn’t saturate the 10GE passing through it with a simple NATing rule. There is something in OPNsense that is wrong, or it could be the Chelsio driver that is really not optimized. Strike tree.
Please, watch out if you want to go OPNsense juste because you now hate Netgate.
Part II - Enters IPFire
Seeing that I will not use OPNsense with all the hickups it has, I’ve decided to retry IPFire that I was not really fond of because of the way to configure it and the lack of control while it runs.
So, after battling the setup again with the GREEN/RED zone thing - at least it recognized my Chelsio right off the bat… but of course : it is Linux under it - I am just configuring 2 networks (for now) just to test drive it again.
One thing that I really like about IPFire is the Pakfire and the tons of package you can use afterward from the command line. Very neat indeed. But, the ugly face of performance hit showed its face and I was kind of stumped. Between my workstation and IPFire, I was able to max at 9.41Gbps non-stop via iperf3. On the other side of IPFire, I was able to max at my ISP’s max bandwitdh of 3Gbps. But when I tried from my workstation to the ISP via a simple NATing rule, I couldn’t even reach 2Gbps on the same hardware pfsense+ was running.
I said “wait a minute!”, this is Linux how come there is such a performance hit with NAT with that hardware? So I started adding some more stuff to try to single out if it was the hardware or the software with IP blocklists (another neat thing built-in of IPFire) and there, I took another 300-400 Mbps hit on the performance! On pfsense+ with a FireHol L1 IP blocklist, there is not a single bit that drops from the speed. With IPFire, well, you saw what I just wrote.
I know IPFire is using IP Table, but I can’t believe the hit on performance. If you guys encountered this, please enlight me!
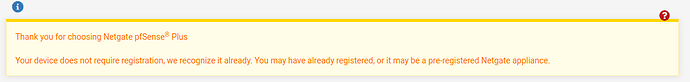
And with that, my adventure with other free Open Source firewalls ended at 4AM after I reinstalled pfsense+. I decide to go back and see what the fuss about that licensing, but I was able to upgrade back to pfsense+. When I went to register again (I wanted to see what would happened), this is was I saw:
Yes I already bougth a SG-3100 in the past, and I did register that 8700k rig when pfsense+ upgrade was available, so I don’t know.
Will I try other solutions? Well, I lied to you: I have a second network at home behind a Fortinet infrastructure and it runs very well - I am a Fortigate specialist btw - and it is quite easier to manage than pfsense for a price though.
Why am I wasting my time with pfsense then? Because I like it. It is the Swiss Army Knife of firewalls that just work and where I have full control.
Does Netgate makes bad decision? Yes like many other companies. But you know what: buy their hardware - at 189$ you have a decent home router/firewall that will last you 5+ years. And no more licensing drama either.
Do I have hope a new kind of license will come out from Netgate? Yes I do. If Netgate roams any forums here, or theirs own or Reddit, they will adjust.
TL;DR
Stay with pfsense, you wont regret it. Other solutions like OPNsense are still subpar. Buy a Netgate appliance as cheap at 189$ and be done with the licensing FUD.