After reading a bunch on VLANs and networking and supposing I understood something (apparently I was wrong) I am attemping to set up the (for now) basic system:
- VLAN10 → management network on 10.1.1.1/24
- VLAN100 → servers network on 10.0.10.1/24.
ESXi ìis running a FreeNAS VM and I want to expose the web interface on the management on VLAN10 and the storage services (for now SMB) on VLAN100.
The Network is run by an USG 3P and UniFi 24ports PoE+ managed switch.
The VLANs are configured as follows on the router:
link
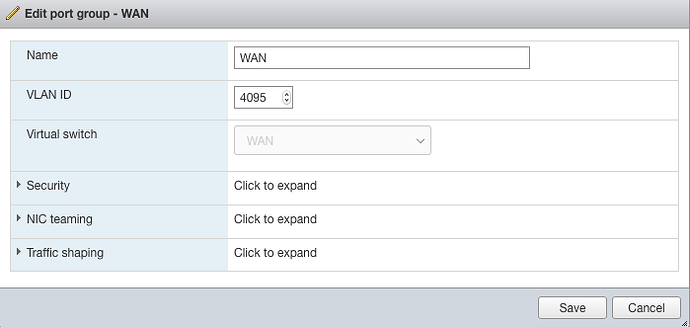
The switch port that is connected to the server is set to pass all vlans and networks, and the ESXi port group is using the 4095 VLAN ID to forward all VLANs.
With default FreeNAS settings I am able to access the FreeNAS box on the LAN network (10.0.1.1/24) for initial setup, and I can successfully add in the FreeNAS network interfaces the VLANs (with em0 as parent) for VLAN100 and VLAN10.
Then, if I change the port profile on the UniFi switch from “All” to the following profile I lose all access, until I reset the configuration on the FreeNAS from the CLI.
Next up, I tried to first set the switch port profile and then run the configuration, which connects the FreeNAS server on the 10.1.1.1/24 subnet (on the VLAN10 but showing as LAN on the freenas, as its the “native” VLAN) but not on the 10.0.10.60 ip address I set up on the VLAN100.
If then I try to invert in the setting the interface that uses the DHCP (In FreeNAS it can only be one) the only interface that works is the one with the DHCP connected.
On the other hand, if I allow “all” profile on the switch port I can access everything (but firewall rules blocking inter VLAN connectivity dont work).
Currently there are no firewall rules preventing inter vlan traffic, and all are set up as corporate, which should allow traffic by default, and a traceroute from my workstation to the non working interface stops at the gateway.
Do you have any suggestions or am I going at thist the wrong way?