Hi All,
Im wondering if there is a special or a better way of doing this, I believe Im correct but I’d like to get some extra input on this before I do it.
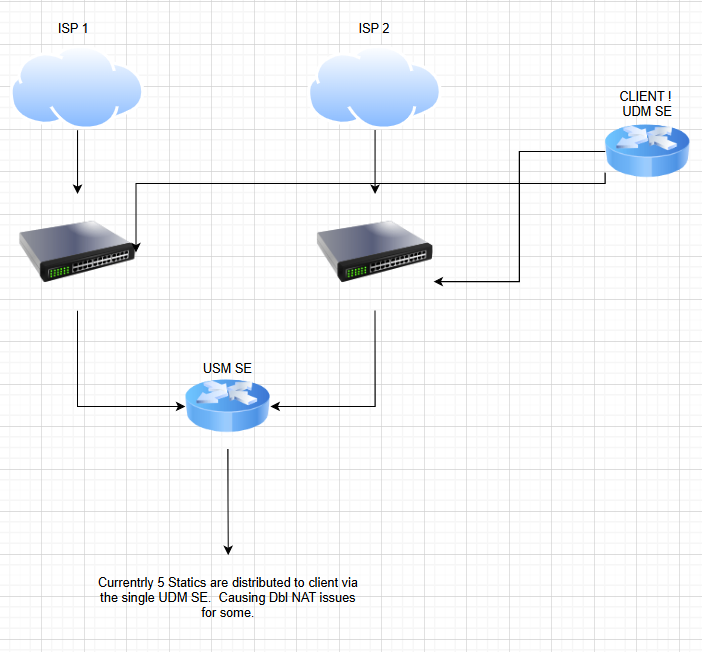
I currently have 2 ISP coming in to the building, both have 5 static IPs available. Currently these ISPs are connected to a UDM SE, and this distributes the static IPS out to clients via the GUI but causes Dbl NAT issues for those also running their own UDM SE devices. Current two clients have this.
I believe I can insert a switch between the Providers router, and the UDM SE for the building, Im thinking (or I have on hand and EdgeSwitch 10x).
Is my thought process correct that If I connect the provider to the edgeswitch, and then connect Multiple UDM SE devices to the ports I can then configure them all to use a static IP address in my range? Would it be best to VLAN each port off.
Can someone tell me or guide me if this is a bunk idea on how to achieve this please? In essence the end result would be to have a direct connection with static ip from my range to each client UDM SE
If I am understanding you correctly, what I would do is create a VLAN for you ISP (if your current switches are layer 2) and then connect the WAN ports to the same access port of the ISP VLAN to your client routers.
1 Like
Either putting a dedicated switch in place, or creating VLANs on your LAN switch to isolated the ISP traffic is fine. The former is called a “DMZ switch” and the latter is called a “Core switch” (all connections from the routers connect to the same switch or same switch stack, both LAN and WAN).
1 Like
Apologies for the delay in responses, Ive managed to break my back .. literally, and im recovering. But this project is coming up and im trying to use my time wisely whilst not in pain.
My Switches are USW Pro 48’s by the way. But I only have Edge Switch 10x swithes on hand to make the DMZ switch option work.
Maybe i was a little barren in the way i explained it, and using the two answers on this post I’ll use some of the terminology correctly. Forgive me if not.
So its looking like im wanting a DMZ switch.
Lets just take one incoming WAN for arguments sake. The provider (BT in this case) provides a router with only one RJ45 out, this currently goes to my building UDM SE (this is not shown in the picture originally posted). This UDM SE then services the whole building via a connection to a Switch Agg, and then a 5 switch stack of USW Pro 48’s. The switches are between the patch ports with little cables to each port. Nice and neat.
In some of the offices, for arguments sake floor port 34 in Office 4, there is a client that has their own network in that office and a UDM SE connected on the WAN port to Floor port 34.
Instead of having Floor port 34 connected to the building switches, I’d like it to connected to a DMZ switch between BT and Building UDM, and give it a static IP from the range that way. Removing the building switches and UDM SE totally. And Double NAT
An explanation on how to config the switch would be appreciated, and i cannot do much testing from my horizontal position right now.
If you want to go the DMZ switch route, then there is no configuration needed for it to work for a single ISP, just connect it between the ISP and each of the router WAN ports. You’ll end up with some longer cables to your patch panels for the specific clients that have their own router, but you can cable manage them neatly still and then it’ll be clear which patch panel ports are special.
If you want two ISPs to share a single DMZ switch, then you simply create a VLAN for each of them, and all ports on the switch would be Access for either the ISP1 VLAN or ISP2 VLAN.
If you want to maintain management access to the switch, then you would have a single cable from it to your building switches, and the IP address of the switch would be on a VLAN on that cable. You would ideally set the ports on both sides to allow only that VLAN (either Access mode or Trunk with a limited set of allowed VLANs).
If you want an explanation of using the building switches with dedicated VLANs instead (the core switch model) I can explain that too. One the one hand it is cleaner in terms of cabling and extra equipment, but on the other hand it mixes public and private traffic on the same switches. I’ll note that VLAN separation of traffic is sufficient for PCI-DSS, SOX, HIPAA, and every other IT security standard I’ve come across.
1 Like
Thank you so much for this detailed explanation, and although I think this is the way I will go .. if you could take the time to explain the alternative I would love to have the knowledge anyway!
Well it really just comes down to “make a VLAN for each ISP and set whatever ports needed for the uplink and for routers to Access that VLAN”. Best practice is to also modify any ports that allow VLANs but don’t need those, such as to APs, to remove those VLANs.
1 Like
Thanks to @brwainer and @xMAXIMUSx for their comments and help on this one. Apologies to both for the time its taken to get back to each comment. Back surgery is looming and I havent been able to get online much. I have managed to get one of the two DMZ switches in place and will be testing over the coming weekend. I’ll let you all know how i get along.