I think I need a fresh pair of eyes…
I’m trying to set up a new network at home. The Unifi controller and access points all sit in the 10.0.10.0/24 range. This is my management range. There is also a pfsense box which does DNS, DHCP and wireless RADIUS authentication on this range.
I have another VLAN using the 10.0.30.0/24 range which is locked down using firewall rules and pfsense.
My wireless clients will connect to the AP and I can see them hitting the RADIUS server and getting the OK from there (RADIUS sits at 10.0.10.1), but clients fail to get an IP address from the DHCP server (pfsense) sitting at 10.0.30.1. They just timeout.
I have confirmed that the Unifi wireless networks are set to use VLAN 30 and the physical port profiles that the access points are set to are set to “all”.
I just can’t work out what I’m doing wrong.
So let’s follow the hardware all the way up.
Unifi APs plug into what brand switch? Unifi switch? Or some other brand managed switch.
Do you have your PFSense box terminating the VLAN tagging? Or just a raw ethernet interface…that you have another network cable linking to a switch port? Either approach can work, just a matter of how you have them configured.
For example…I have a lot of clients networks using UBNT switches and APs…but I’ll have Untangle as their UTM at the end. And on Untangle…I’ll often use at least 3 or more ETH interfaces. ETH0 for the WAN, ETH1 for the primary LAN, ETH2 for a different VLAN (say VLAN2), ETH3 for Guest VLAN, etc.
Now I can have Untangle terminate the VLANs for 2 and 3 by tagging those to that port…in which case having all ports of the switch tagged with all VLANs would make it easy. So the switch would have 3x ports linking to the 3x different LAN ports on Untangle and it would work.
OR…I can have it so Untangle doesn’t tag any VLANs on its ETH interfaces…I leave the VLANs out of Untangle. And I use the switch ports facing those ETH interfaces on Untangle to control the egress of VLANs. The switch port facing (uplinking to) Untangles ETH2…I have UNtag VLAN2, and EXCLUDE all other VLANs. For the switch port facing Untangles ETH3…I UNtag VLAN3, and exclude all other VLANs.
If you have a single Unifi switch on a small network, it’s easy enough to manipulate your ports individually for VLANs and POE. If you have multiple switches and a larger network…it’s more elegant and efficient to setup Profiles in the controller and manage ports through profile memberships.
2 Likes
So the core of the network is a pfsense router plugged into a core Cisco switch. Each VLAN has it’s own physical NIC port to a physical untagged switch port. From there, there are two uplinks for the two VLANs (untagged) from the Cisco switch to the Ubiquiti switch. On the UBNT side, the untagged ports correspond with tagged (?) ports/network profiles on the Ubiquiti switch/controller.
When I say “tagged” on the UBNT side, there are separate network profiles set up with the appropriate VLAN number configured in each.
I had this working before (on the old network) but I must be missing something.
Gotcha. Hmmm…OK so let’s peel back the layers on the Unifi side…as it sounds like you’re good from PFSense…to Catalyst…to handoffs to the US switch.
On the properties of the wireless network bound to VLAN30…do you have “Black LAN to WLAN Multicast Data” checked? If so…is the MAC address of the host the DHCP service runs from (assume that ETH interface on PFSense) entered to allow to bypass?
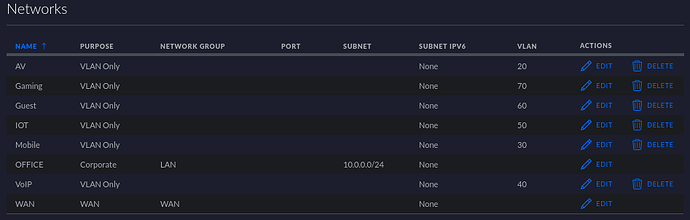
In Unifi…are the networks that the VLAN is created as VLAN Only? Or Guest?
Guest policy enabled or not on that SSID?
Nope, that’s disabled. Along with DHCP guarding and DHCP snooping.
I’m also not getting any blocked firewall rules on the pfsense side (in case it was coming in on the .10 VLAN and back out the .30 VLAN for some strange reason).
I did originally have the VLANs set up as Corporate/Guest. I have now changed them to VLAN Only thanks to your advice as I now remember this is how I originally had them set up.
Guest policies are disabled.
Still same the same result I’m afraid.
Well…//drums fingers on desk…
Guess it’s time to pull apart the pieces and work backwards.
Unplug the patch cable linking the ETH interface on PFSense for that VLAN to the Cat …plug a PC or laptop right into that PFSense port…see if you pickup a valid IP.
If so…next…connect the Cat switch again…and go to the other end, unplug the patch cable that uplinks it facing to the untagged port for that VLAN on the Unifi switch…plug the laptops patch cable into that port on the CAT…still get a valid IP?
If so…narrowed down to something in the Unifi setup…possibly the profiles.
If not…now at least you have the PFSense and the Cat to look at.
1 Like
So I tried all of that last night (after hours of mucking around, going down rabbit holes).
I get an IP address just fine on the .30 VLAN on the (primary) Cisco switch, including on the uplink port connecting both switches together.
However, I don’t get an IP address on the UBNT switch, even with the port profile set to VLAN 30, so I can confirm that the issue is somewhere upstream of Cisco switch (i.e.: the (secondary) UBNT switch).
I also tried swapping the priorities of the STP around in case something funny was going on there, but all of the ports were forwarding anyway.
Just thinking out loud:
-
The controller is a brand new install (I replaced the Cloud Key Gen 1 with a Linux box). The switch was factory recent via the front panel reset switch, but the access points were just “Advanced Adopted”. Maybe something strange from the previous network is still stuck somewhere? Although this doesn’t explain why the copper ports on the UBNT switch don’t get an IP on that VLAN.
-
There are two uplinks from the Cisco switch to the UBNT switch (one for the .10 VLAN and the other for the .30 VLAN). On the controller, the .10 port shows up as an “Uplink” port (with a chevron icon), the .30 one doesn’t. This is not something I set, obviously the switch is detecting this? I can’t seem to find a setting for “uplink”. Not sure if this is relevant or not?
-
The .10 VLAN is set up as the default “Corporate” network on the switch. DHCP etc… works perfectly fine on ports set to this profile. I tried creating a Corporate profile but for VLAN 30, that fails. No traffic gets through.
-
If I uncheck “Use VLAN” in the Wireless network config. It works fine (but goes to the native .10 network). Setting this to anything (even VLAN 10) causes it to fail again.
It’s a really strange one. The untagged VLAN works and all tagged ones don’t.
This just gets stranger…
I SSH’d into the Ubiquiti switch (and after configuring a firewall rule to allow ICMP), I can ping the gateway on VLAN 30.
So some traffic at least is getting through across the trunk port.
I can’t see anything in the firewall logs however to suggest that DHCP is being rejected or blocked.
On the Unifi switch…the port facing the Cat switches VLAN 30 port…is that port on the Unifi UN-tagged for VLAN30…and all other VLANs are excluded?
As far as I can tell, the port on the Unifi switch is tagged (the port profile is set to VLAN 30 and that profile has the VLAN Only network selected with all others unselected). Although I can’t be sure as I’m not sure how Unifi labels tagged and untagged ports in the GUI.
The Cisco switch is configured as a Trunk port with the native VLAN as 30. I’ve also tried it in access mode and setting the native VLAN to anything other than 30, but same result. I have also tried other physical ports and cables.
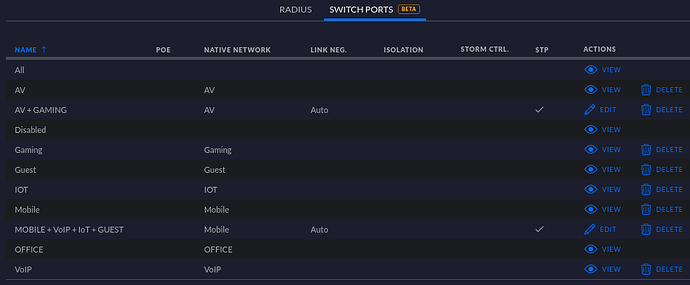
Do these help?
Note that the “All” switch port profile will carry all VLANs without specifying a “native” VLAN.
Yep, so my “VLAN 10” is set up as the Corporate network. The rest are VLAN Only, same as your screen shots.
Try this…create a profile that has VLAN30 as its default VLAN. None others. Can call it “VLAN30Untag”
Yeah traditionally with other brands managed switches, we’re used to checkboxes for port profiles, with T (tagged), U (untagged), E (Excluded) by each port.
But with Unifi…they take a different approach, and later added profiles, I hated it at first…but when doing larger networks, I learned to appreciate the elegance of it.
With Unifi…the equiv of a port set to untag a vlan and exclude others…is to just set that VLAN as the default one, and not add any others.
So it sure seems the breakdown is in this uplink from Cat to Unifi Switch.
Can you provide a screenshot of the settings of this uplink port on the US?
Sorry for the delayed reply guys, I’ve had a lot going on over this past week.
A bit of an update, I suspect what the problem has been was the Cisco switch itself.
I rebooted the Cisco switch as one of my new servers which I provisioned over the weekend basically “fell off” the network. The switch showed a link light, but Proxmox reported link down on all the NICs. Some other devices on that switch continued to work however. I rebooted the switch and that’s when the major problems started. Since that reboot, it powers on, seems to boot up OK, but none of the ports show a physical link anymore. Even factory resetting doesn’t seem to work.
It looks like it just died.
I’ll need to order a replacement switch then do further testing, but I get the funny feeling all will be OK.
1 Like
Alright, so last night I provisioned the new (Ubiquiti) switch and changed the VLAN settings over from 'VLAN Only" to “Corporate” and everything is working exactly as it should. The Cisco switch was indeed at fault.
The symptoms I experienced are nothing like I’ve ever seen before. Traffic (ICMP) was clearly getting through the trunk but DHCP wasn’t. No errors logged on the switch itself, the firmware appeared to be operating normally and nothing else really seemed to be misbehaving (until I rebooted it the other day). Really bizarre. Although I wasn’t happy that the switch failed, I’m happy that the problem is resolved.