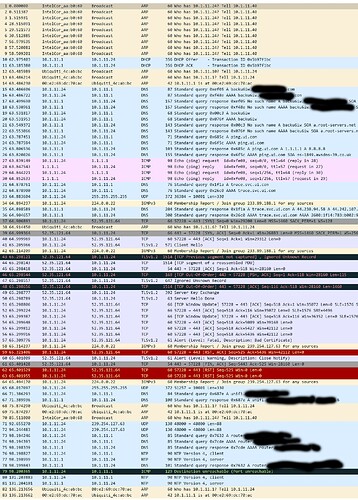
I am rather puzzled. Starting last night I’ve had a large number of Snort Alerts coming from all of my unifi devices.
SID 3-15450 MALWARE-OTHER Conficker C/D DNS traffic detected
This is a rather old SID and I certainly don’t have any vulnerable devices. Also, the alerts are triggered even in the absence of clients, and even by PDU-Pro when it’s the only thing connected to the network.
I have reset the devices with recurrence of this.
I also captured the packets associated with the alerts by unplugging all but one of the devices and eliminating any clients for clarity, and they just seem like unifi telemetry traffic.
I was wondering if anyone has encountered anything like this and whether my network is in trouble. Thanks in advance.