I have been working to connect via OpenVPN client to a remote OpenVPN served by NetGate 2100 and pfsense.
Local win11 desktop <-----> local Netgate 2100 <----> OpenVPN Client <-----> Remote NG2100 <----> NG2100 admin.
Local NG2100/pfsense configured per default Lawrence Systems Youtube video in home operation for approximately on year. No public IP attached to WAN . No previous FW wan rules. Basic LAN rules before OpenVPN client installed.
System firewall logs indicate the following:
May 9 15:35:01 LAN Default deny rule IPv6 (1000000105) [fe80::ccf:561b:79c:adef]:5353 [ff02::fb]:5353 UDP
May 9 15:35:00 LAN Default deny rule IPv6 (1000000105) [fe80::ee67:df24:1b80:a0da]:56016 [2600:1901:0:f8b::]:443 TCP:S
May 9 15:35:00 LAN Default deny rule IPv6 (1000000105) [fe80::ee67:df24:1b80:a0da]:56014 [2600:1901:0:5723::]:443 TCP:S
May 9 15:35:00 LAN Default deny rule IPv6 (1000000105) [fe80::ee67:df24:1b80:a0da]:56011 [2600:1901:0:4ba4::]:443 TCP:S
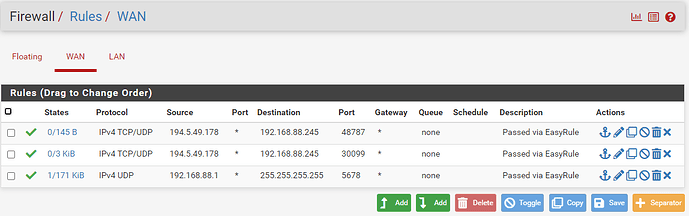
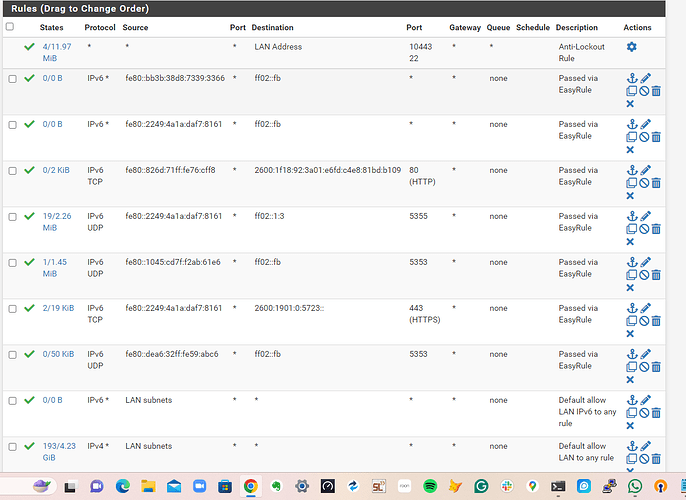
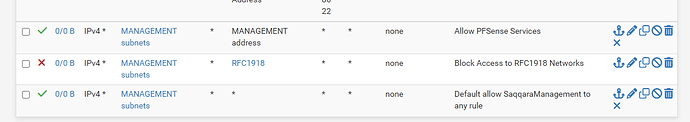
I have added the appropriate FW rules via the EasyRule function from the FW log entries. (7 LAN and 3 WAN) but continue to be blocked by the default deny error as follows:
| May 9 15:41:20 | LAN | Default deny rule IPv6 (1000000105) | [fe80::2249:4a1a:daf7:8161]:17169 | [2600:1901:0:4ba4::]:443 | TCP:S |
|---|---|---|---|---|---|
| May 9 15:41:12 | LAN | Default deny rule IPv6 (1000000105) | [fe80::2249:4a1a:daf7:8161]:17169 | [2600:1901:0:4ba4::]:443 | TCP:S |
| May 9 15:41:09 | LAN | Default deny rule IPv6 (1000000105) | [fe80::ccf:561b:79c:adef]:5353 | [ff02::fb]:5353 | UDP |
The OpenVPN client logs indicate the following:
Thu May 9 15:39:27 2024 SIGUSR1[soft,tls-error] received, process restarting
Thu May 9 15:43:24 2024 SIGHUP[hard,init_instance] received, process restarting
Thu May 9 15:43:24 2024 OpenVPN 2.6.7 [git:v2.6.7/53c9033317b3b8fd] Windows [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] [DCO] built on Nov 8 2023
Thu May 9 15:43:24 2024 Windows version 10.0 (Windows 10 or greater), amd64 executable
Thu May 9 15:43:24 2024 library versions: OpenSSL 3.1.4 24 Oct 2023, LZO 2.10
Thu May 9 15:43:24 2024 DCO version: 1.0.0
Thu May 9 15:43:25 2024 TCP/UDP: Preserving recently used remote address: [AF_INET]170.247.154.236:1194
Thu May 9 15:43:25 2024 UDPv4 link local: (not bound)
Thu May 9 15:43:25 2024 UDPv4 link remote: [AF_INET]170.247.154.236:1194
Thu May 9 15:44:25 2024 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Thu May 9 15:44:25 2024 TLS Error: TLS handshake failed
Thu May 9 15:44:25 2024 SIGUSR1[soft,tls-error] received, process restarting
Thu May 9 15:44:26 2024 TCP/UDP: Preserving recently used remote address: [AF_INET]170.247.154.236:1194
Thu May 9 15:44:26 2024 UDPv4 link local: (not bound)
…
My route print list is as follows:
===========================================================================
Interface List
17…Wintun Userspace Tunnel
21…ExpressVPN TUN Driver
20…b0 7b 25 27 20 d2 …Killer E2600 Gigabit Ethernet Controller
11…00 ff 5e 84 ba 4f …TAP-Windows Adapter V9
7…OpenVPN Data Channel Offload
6…44 af 28 ba fa 13 …Killer(R) Wi-Fi 6 AX1650i 160MHz Wireless Network Adapter (201NGW)
14…44 af 28 ba fa 14 …Microsoft Wi-Fi Direct Virtual Adapter
12…46 af 28 ba fa 13 …Microsoft Wi-Fi Direct Virtual Adapter #2
9…44 af 28 ba fa 17 …Bluetooth Device (Personal Area Network)
1…Software Loopback Interface 1
In summary, I have been working for several days to connect to the remote Netgate 2100 via the openVPN client export it generated for Windows 11 desktop but seem to be blocked by my local gateway Netgate 2100 pfSense firewall.
Any suggestions?
Thank you.