I have seen some posts already about UDM Pro and pfSense.
We are needing to use the controller, protect, and access applications, but not the firewall/routing/dhcp fucntions.
If it was not for the access application only being on the UDM Pro, we would not have purchased it :).
That being said, we have a pfSense firewall with 1 wan interface and 3 lan interfaces along with site to site vpn and client Open VPN setup.
We are looking for the easiest way to integrated the UDM Pro with our existing pfSense firewall.
Right now we just have our primary vlan connected to WAN to give it an internet connection so it will stop complaining.
@LTS_Tom Love the videos!
Thank you, Blane with Church of the Harvest
- Create a new VLAN on the PFSense and your switch(es) which will be purely for the UDMP’s WAN.
- Move the UDMP’s WAN port into this new VLAN.
- Change the “LAN” network on the UDMP so that DHCP is disabled, and the “gateway IP” is something in your primary LAN but not conflicting with anything else. E.G. 192.168.1.2/24.
- Connect the UDMP LAN port to your primary VLAN.
At this point, as long as you don’t manually put the UDMP’s LAN IP into any device as the default gateway, nothing will use it as a router to get to the internet.
3 Likes
@brwainer
This makes total sense, you have saved us a lot of time! 
+1 for @brwainer’s answer. couldn’t have put it better.
@brwainer
Can we trunk our VLANs from pfSense to a port on the UDM or should we go to our first Unifi Switch as a trunk?
Thank you.
The LAN ports on the UDM are basically a switch anyway - here’s a page that shows the internal layout of the UDM Pro: https://ubntwiki.com/products/unifi/unifi_dream_machine_pro
So it almost doesn’t matter whether you go to the switch inside the UDMP first or some other Unifi switch. Either way, the port connecting to the PFSense needs to be set to the “All” port profile, and you need to create each VLAN as a “VLAN only” network in Unifi.
@brwainer
Firstly thanks for all your contributions to the forums. Could I ask for a little clarification on this as I am struggling to get this to work having the UDM Pro behind pfSense.
I have created a dedicated LAN port on pfSense and have setup a network with a VLAN tag of 10 with the LAN interface on pfSense being: 192.168.10.254/24
I have connected this to the WAN port on pfSense and setup DHCP so that the UDM Pro and my three Unifi Switches and two APs all have static IP addresses issued via DHCP from pfSense
The problem I think am running into is the LAN network on the UDM Pro cannot be deleted and there is no option to add a VLAN tag either? Do I need to assign different IPs on the UDM Pro for the LAN & WAN interfaces? I used ifconfig to work out the different MAC addresses for the WAN1 interface and LAN interface.
Also does the LAN interface in pfSense need to be set with no IP address so that VLANs can be assigned to the interface?
I have the following VLANS and DHCP ranges defined in pfSense.
10 - 192.168.10.254/24 - UDMPRO, Switches, and APs
20 - 192.168.20.1/24 - OFFICE
30 - 192.168.30.1/24 - HOME NETWORK
40 - 192.168.40.1/24 - GUEST NEWORK
50 - 192.168.50.1/24 - IOT NETWORK
60 - 192.168.60.1/24 - UNIFI PROTECT CAMERAS
If you could help me out I would be most grateful as I am only just starting out on my homelab journey and have so much to learn.
Kind Regards Ian
If you have Unifi switches and APs, it would be easiest to have a management VLAN that you can leave the UDMP in charge of for DHCP and routing. Maybe even use “VLAN1” (the LAN) as the management network, and don’t put any non-network devices in there. You can set all the ports that aren’t in use to a different port profile that has a native vlan as something other than 1. In the CCNA course I just took, the instructor recommended making some VLAN that intentionally gives no service, even if a static IP is used, so that an administrator has to be involved in assigning any port for use. Of course you could just shutdown unused ports as well.
Yes you cannot delete the LAN network, and I’m not surprised the UDMP doesn’t allow it to have a VLAN either. The multiple-role configuration of the UDMP requires certain assumptions. I prefer to use VLAN1 as management with Unifi for this reason.
You never want a router to have the same subnet on both LAN and WAN.
I’m not an expert on this. I haven’t had to in the past.
@brwainer
Thanks so much for the advice, I have followed what you said and let the UDMPRO handle all LAN routing and used pfSense to provide a virtual WAN interface for the UDMPRO. This allows me to have DNS, IDS/IPS, and HA Proxy all working
In a world where the UDMPRO can accept multiple VLAN IDs I may change it back so pfSense can provide DHCP for the VLANS and provide Firewall Rules in one place rather than two.
Kind Regards Ian
@brwainer
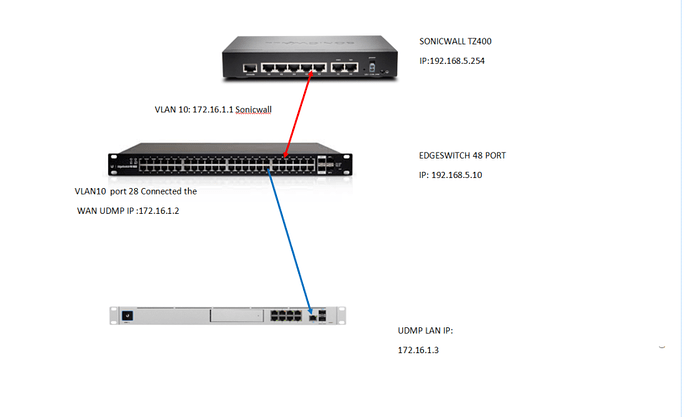
Can you help me I have sonicwall and UDMP also edgeswitch
Can I make UDMP be controller only? I Try to create VLAN from Sonicwall and Switch but when I try to put the UDMP did not detect the UDMP
My first recommendation is to use the CKG2+ and/or UNVR instead of the UDMP - then you don’t have to deal with special setups to make the UDMP work.
If you can’t do that, this is a fairly simple exercise in VLANs, subnets, and routing. I am measuring “simple” in comparison to other networking workarounds and tricks I’ve experienced.
The UDMP has a few requirements you have to handle:
- It needs to have internet access via one of its WAN ports.
- None of its other logical interfaces (the LAN and VLANs) can have an overlapping subnet with the WAN.
- NAT is applied to all traffic that leaves through the WAN port of the UDMP and cannot be disabled through normal means.
Therefore, the easiest solution is to make a VLAN on your “actual” router and the switches that provides internet access and uses a subnet different from everything else (which is only a challenge if that other router/firewall isn’t the only place for all your VLANs). Connect the UDMP’s WAN (and only its WAN) to this VLAN. If your switches are Unifi and you need to program this VLAN in, you would make it as a “VLAN only” network - in fact you would do this for every VLAN that the sonicwall is the default gateway of.
The UDMP will normally out of the box only work as a controller for devices on its LAN side (LAN network or a VLAN that is not made as “VLAN only”). This means it is easiest to allow the UDMP to be the gateway and DHCP server for the management VLAN, into which you put all of the APs, cameras, etc that the UDMP will manage.
If you need the UDMP to be available as a controller in a VLAN, but not be the default gateway, then you can add it as a network but disable DHCP and set the “Gateway” IP address to be something different from the other router/firewall.
If you want the UDMP to allow connections to the controllers from its WAN port/IP, you’ll need to open the controller’s TCP/UDP ports on the WAN-Local firewall.
@brwainer
I’m so very thankful to you for this answer. However when I try to create Vlan in my Sonicwall and Switch and the WAN of UDMP connected in that VLAN the connection from UDMP is intermittent. meaning useless that why did not connect the LAN of UDMP to may Edge switch
My setup to my UDMP right now is Sonic wall will be the give DHCP to Switch and the UDMP connected to the EdgeSwitch with Static IP and the DHCP is off. the WAN of UDMP slot empty
Right now I can use UDMP as a Controller locally but I cannot access the GUI outside.
Please provide more details about the VLAN you created, and how the connection is “intermittent”.
It is normal in this mis-use of the UDMP to have both the WAN and LAN of the UDMP connected, as long as they are different subnets and you don’t end up with a routing loop where the UDMP’s WAN goes through its LAN.
This is my first setup, the problem here is when I try to access the GUI on the internet the device is intermittent on and off and very slow to open.
Should I put another cable from the UDMP port to the Edgeswitch port?
UDMP is DHCP off also the WAN-local open 443
thank you for your help
The WAN and LAN on the UDMP need to be in different subnets. I’ve said this multiple times. Your diagram has then in the same subnet.
Yes, without extra tricks, you should have two cables to the UDMP.
Interested in your HA Proxy setup with the UDM Pro behind pfsense and how it’s configured. If the UDM Pro is handling the routing how does it know what backend to send the traffic to? Thanks in advance.
I use of plsense as a DNS server with fully qualified domain names with pfsense as a DNS forwarder to Cloudflare which hosts the domain.
I use Let’s Encrypt to provide SSL where possible, otherwise I have a wildcard domain SSL for devices such as the UDM Pro.
This allows me to use Cloudflare as the HA proxy
I also have a static IP address from ISP in place which helps.
Otherwise in terms of the routing, that is done in UniFi and essentially all Internet traffic is routed via the WAN interface using the setup recommended by Bruce. Wainer.
My local devices are as follows:
Raspberry Pi 4B - Home Assistant Server
Raspberry Pi 4B - Homebridge
UDM Pro - UniFi Controller for Network & Protect
UniFi 16-Port PoE
UniFi Aggregation Switch (10G)
UniFi 6LR Access Points
House cabled with CAT 6E to provide 10G across any LAN connections.
Next steps:
Create local Homelab server running either XCP-NG or Proxmox, looking for a Ryzen Pro 5750g to match with an ASRock Rack X570 but seemingly very difficult to find!
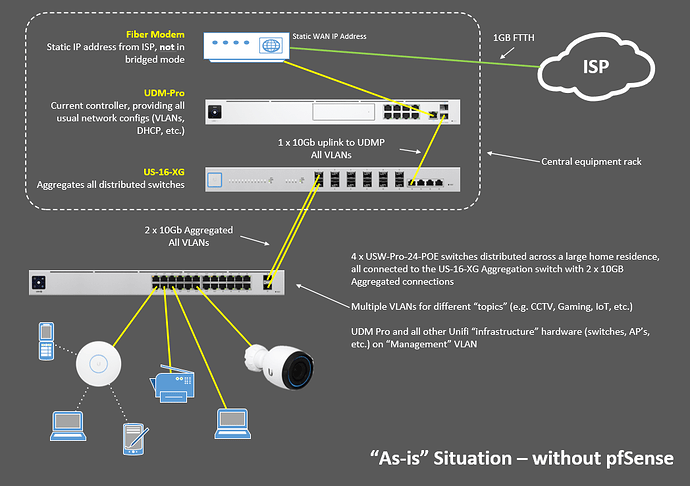
This is something I am struggling with and have been banging my head against the wall with. I’m sure I’m just overthinking it and at its core it’s straightforward. I just can’t seem to get my head wrapped around where the UDM Pro should / can be placed in the network, even though I’ve seen Tom’s video on it (100’s of times)
This is my current architecture:
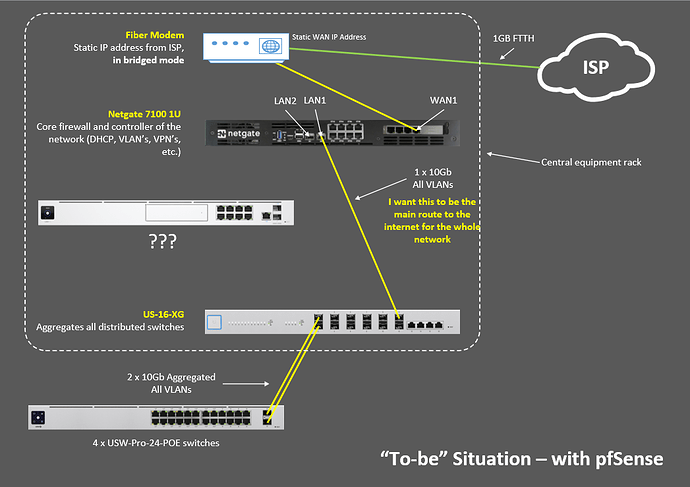
This is how I envisage the to-be architecture, but my question is, if the UDM Pro needs to connect to the netgate on 2 different ports (one for Internet connectivity, one to be “present” on the Management LAN, how would members of this forum connect this up?
(can’t add the second image as I am new to the forums and restricted to only 1 image per post)
Make these connections:
UDM-Pro WAN1 to PFSense LAN2.
UDM-Pro LAN1 to USG-16-XG (same connection it has now, don’t move it)
All you have to do on the UDM-Pro is:
- Change the Unifi networks to disable the DHCP server
- Change the “Gateway” IP in the Unifi networks to something that doesn’t conflict with the PFSense. This is just defining what IP the UDM-Pro will program itself with.