(first time poster - huge fan of the YouTube channel)
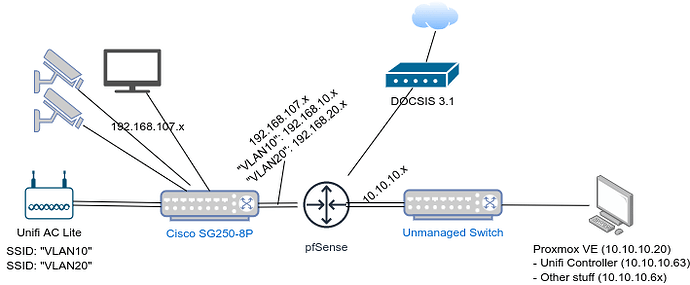
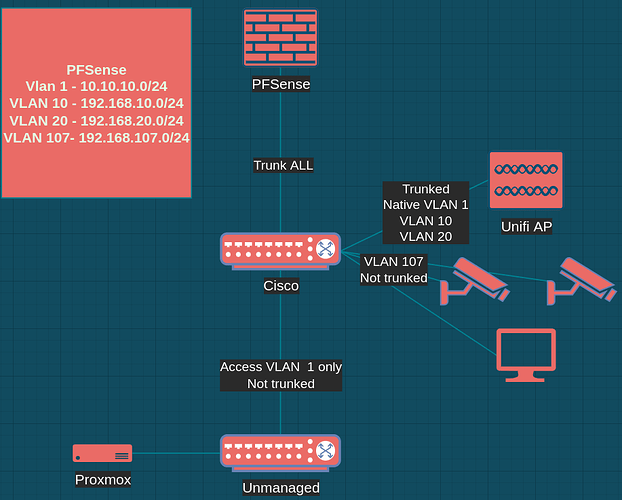
Hi, this is my first foray into VLANs and I’m having trouble to setup the Unifi AP in this setup (think homeish setup/livingroom like):
The right side of the router (10.10.10x) is trusted with no restrictions, while the left side of the router (192.168.107.x) is generally untrusted and can only get to the internet. To allow the AP to serve devices out of both categories, I created two VLANs: one for ‘AP management/internal/trusted LAN’ and one for ‘IoT/guest’.
The Unify Controller (10.10.10.63) is in a Proxmox container ‘on the other side’ of the router, which is VLAN-unaware (the 10.10.10.x switch is unmanaged).
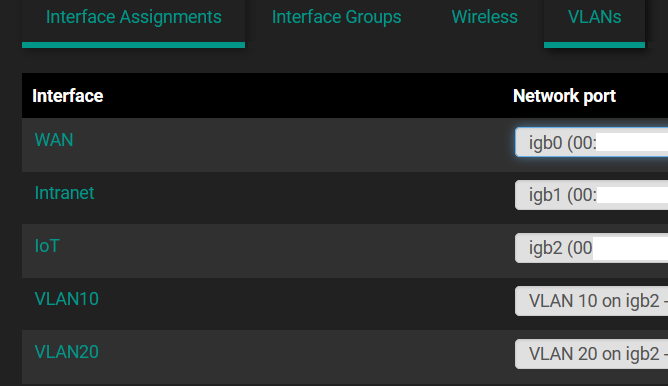
I created VLANs 10 and 20 on the pfSense router:
Interface: “VLAN10”, static IPv4, 192.168.10.1/24, DHCP enabled, BBOOTP/DHCP Options:43, String, 01:04:0a:0a:0a:3f
Interface: “VLAN20”, static IPv4, 192.168.20.1/24, DHCP enabled, BBOOTP/DHCP Options:43, String, 01:04:0a:0a:0a:3f
To simplify debugging, there’s only one rule in the FW settings for each VLAN right now: IPv4: any, any, any, …
The 10.10.10.x subnet also has a rule to access anything: IPv4: any, any, any, …
From the 10.10.10.x side of the network, I can reach the web UI of the Cisco switch via all three IP addresses: 192.168.107.20 (no VLAN/well default VLAN, I guess), 192.168.10.2 (VLAN10), 192.168.20.2 (VLAN20).
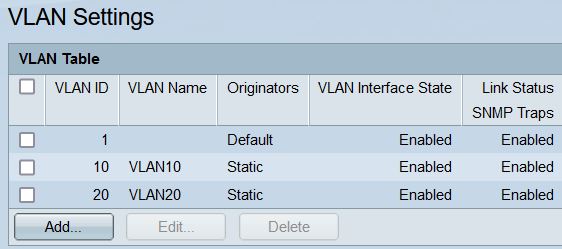
I created VLANs 10 and 20 on the Cisco switch.
The uplink port (#8) (to the router) and the port to the UAP (#7) are configured to be “Trunk”, all other ports are “Access”
For VLAN ID 1: All ports are untagged
For VLAN ID 10: ports #1…#6 are Excluded, #7, #8 are Tagged
For VLAN ID 10: ports #1…#6 are Excluded, #7, #8 are Tagged
I adopted the UAP while it was on the 10.10.10.x subnet and created both VLANs in the Unifi Controller SW. Now that I’ve moved the UAP behind the managed switch, it won’t stop blinking and the Unifi controller SW can’t see it anymore.
How do I get the UAP and the Unfify controller to caommunicate with each other?
Thank you!
Update1: Additional infos:
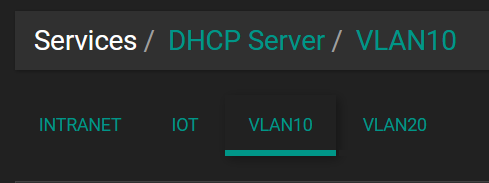
- I have static reservations for the APs MAC ID in all four DHCP configs (Internal, IoT, VLAN10, VLAN20).
- The access point is configured for DHCP.
- I cannot ping the access point once it’s on the Cisco switch.