I am having issues setting up the routing to a new subnet on my LAN. I should know how to do this, I’ve done it in the past “manually” with plain Linux and Shorewall, but my brain’s gone blank trying to do this in pfsense. I’ve got a simple home network set up through a pfsense box, just WAN and LAN. Now, I’m in the process of adding an IP camera server with two interfaces: one for LAN, and one to isolate all the camera traffic. Pretty much have the camera server’s routing and firewall set up, but telling pfsense about that camera lan has me confused. I have tried making the camera server a gateway to the camera lan, and then adding a static route to pfsense using that gateway, but I’ve definitely not done something right.
Can’t set up a vlan because I don’t have a smart enough switch at the camera server.
Since I only intend to access the cameras through the camera server, should I just do NAT on the camera server for the camera lan? Pretty sure that would end the problem, except that I’d like to be able to administer the POE switch there from the LAN and not just the camera server.
Beside, I think this should work, once someone goes through the routing/setup process in pfsense enough for me to facepalm and go, “well, duh.”
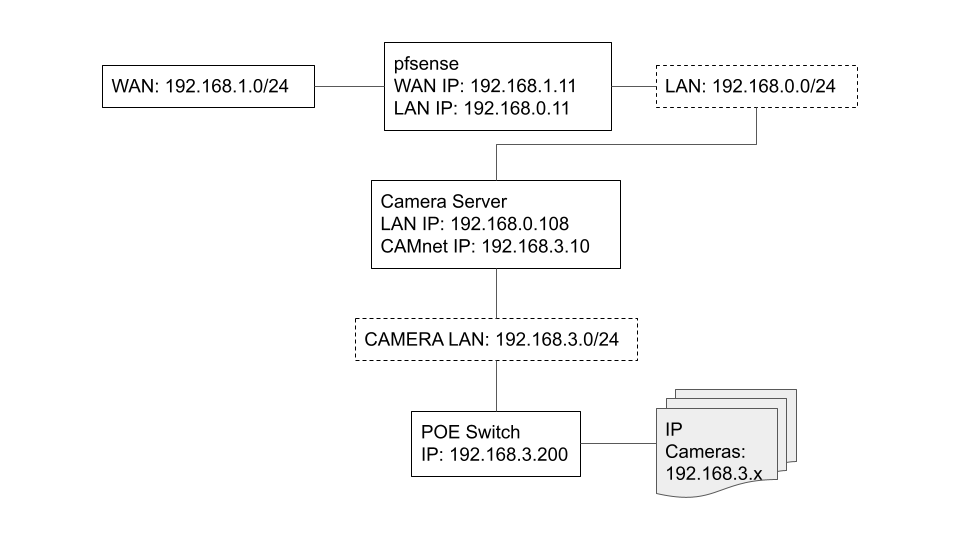
Below is a diagram of the relevant part of the network. So, can I get a hint of how to tell pfsense about that 192.168.3.x network accessible through the camera server, so that traffic can flow between LAN, WAN, and the camera network? Yes, that’s wide open, but I intend on locking things down once I get the camera network working at all!
Not certain but wouldn’t a static route from pfSense to Camera Server and vice versa solve your problem. Not how I would do things, a managed switch would make life easier.
True, and true. In pfsense, I’ve set up the camera server (192.168.0.108) as a gateway, and then defined a static route for 192.168.3.0/24 through that gateway. On the camera server, I’ve set pfsense as the default gateway. I need to go back through that step by step and see if I’ve messed that up.
As for a managed switch, yeah, then I could just create a VLAN. I do have a managed switch for the main network (192.168.0.0/24), but as I understand VLANs, you have to define those by the port on a switch, and the port that has the camera server on it also has other devices. Which I think means that I’d need another managed switch on that run, at the camera server, and define the VLAN there. Don’t have another managed switch, and I really don’t want to run a dedicated line down there, so that makes the easy way out, well out.
Besides, what I have should work: a dedicated camera network isolated by interfaces in the camera server. I’ve actually done this before, the “hard way as in not with pfsense”, so I’m just missing something simple. At some point, the facepalm will happen, and the light bulb will come on; I just need to make a cup of tea and stare at it.
If your LAN is a managed switch, I would create a CCTV vlan on it.
You can plug your dumb switch in to a VLAN port.
Connect your CCTV server in to the LAN switch and expose it to the vlan and LAN.
Use pfSense to route between the two.
I can’t see why that would not work.
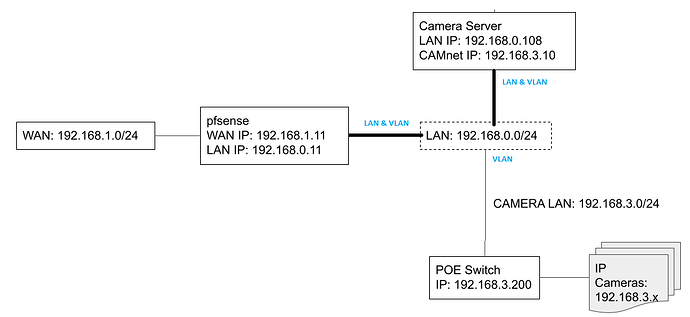
Update : like this :
Yes as @daninmanchester says that sounds like it will work.
Hmmm… my knowledge of VLANS is all reading, and my practical experience predates them (subnets by different NICs, routing, and firewalls). Let me see if I am understanding this.
- On my managed switch, create a VLAN on two ports.
- Set up the 192.168.3.x subnet on that VLAN, and those two ports will now be that subnet.
- Connect the camera server up to one of the ports, and the POE switch to the other port.
- Enjoy?!
I think my issue with this is the physical layout of the wiring, and the port usage. I’ve only got one cable that runs towards where all the camera cabling enters the house, and that cable currently has multiple 192.168.0.x devices connected to it along the way. I know, I know; this home network has evolved over almost 30 years. In a perfect world, I’d run a new cable down there just for the camera server, but it’s just not practical right now. So, if I made that one port that reaches the camera server a VLAN port, then would not all the other devices along that leg now be in the 192.168.3.x subnet?
In the meantime, I’ve just set up ip masquerading on the camera server, so the 192.168.3.x subnet is hidden behind the server. The home lan only sees the camera server’s 192.168.0.x NIC. That’s working fine until I learn the pfsense way. I’ve got Shorewall and the routing set up on the camera server’s two NICs, and that’s working. All the ip camera traffic is isolated to it’s own subnet, and only accessible through the camera server. The rest will dawn on me at some point!