Hi there,
I have recently stumbled upon your Youtube channel and have been checking some video’s. Great content. Wish some were a bit more in depth.
We have been changing our network for a while now, but I am stuck in between 2 consultants and would like to get some more input from others if I am going down the right path or not.
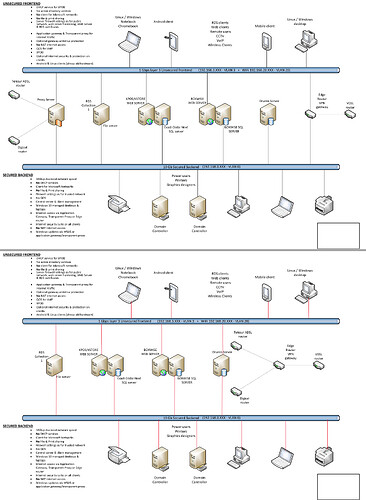
I have attached 2 schematics of how are network is now, and how I think we will go to.
For now, we are using n 8 port Ubiquiti Edgerouter, with some Cisco SG200, 250 and 300 switches.
The servers are split into 2 server rooms, with each a SG300 connected to eachother, with only 1 switch connected to the EdgeRouter.
All other switches are connected to these 2 switches.
For now, both frontend and backend are on the same switch, but we have plans to upgrade the backend switch to a 10Gb switch.
The Wifi is a mix of Unifi AP AC Pro’s and Mesh, controlled by a Unify Cloud Key. All are connected to several of the switches in the LAN.
We also have a seperate management VLan and a VOIP VLan, all mixed into the network.
The issue is the router. The consultant who implemented it wants to upgrade it to a FortiGate FG-100E basic for $3,000, which is too expensive for us.
We were thinking of a Sonicwall TZ350 or 400, which is halve the price or less.
Looooong ago I have set up a VPN link between 1 office and this LAN using 2 Sonicwall TZ100’s.
I am unfamiliar with CLI.
We have about 32 RDS users on VLAN 3 and 15 pc’s and printers/mfp’s on VLAN 0.
We have other offices with static routes coming into the LAN and also some users connecting with OpenVPN.
Please let me know what you think of this matter.
Regards,
Winston