EDIT: Sorry, the forum only allowed me to post 1 embedded media per post, so I had to post the additional 3 images as separate posts…
EDIT 2: Received badge to be able to post multiple embedded images, so deleted the other posts and re-embedded the images in original post…
Long time follower of Lawrence Systems on YouTube. I have learnt and configured a lot on my pfSense box using LTS videos. Finally hit a snag which is either not available in any video or I am too thick to understand. So here I am…
I recently got a TP-Link EAP 225 with the hopes of setting up different VLANs for the various networks that I wanted to segregate. I have set up 4 separate SSIDs with different VLAN ids but I don’t get internet access on any of them. I have a 5th SSID which has no VLAN id associated and that works just fine. Note that I get the correct IP assigned to the device while on the network, I just am not able to access the internet. I can also ping the X.X.X.1 (which is the gateway IP for the VLAN that I am connected to via that SSID)
My network structure is simple:
modem → pfSense on bare-metal → switch → AP
- Trunk – Switch Port 45 carries LAN, WORK & GUEST networks from pfsense to switch
- Trunk – Switch port 46 carries CCTV & IOT networks from pfsense to switch
- Trunk – Switch port 7 carries everything from switch to AP
I have 2 trunks from pfsense to switch because the cameras are chatty and wanted to separate those over different trunks – eventually I may separate the switch and APs too in order to get them completely independent of each other. Also, I had extra ports available in my pfSense network card
Here’s my pfSense configuration for the different VLANs
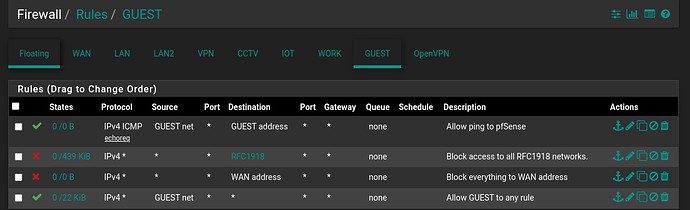
Firewall rules:
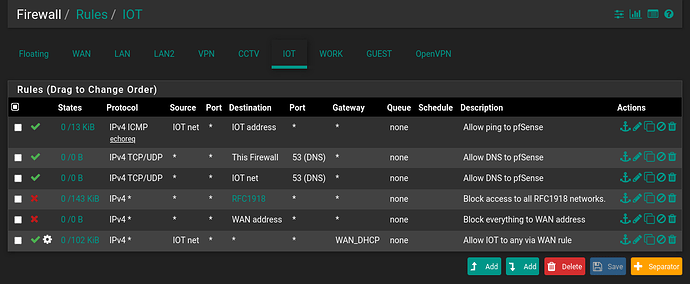
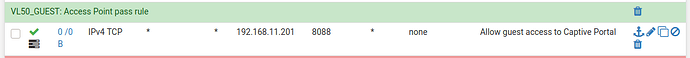
Initially I thought that I might need a allow rule so that the network could access the pfSense for DNS, but even when I added that rule it didn’t make any difference. Here’s a screenshot with the rule added for the IOT network. Still no internet access.
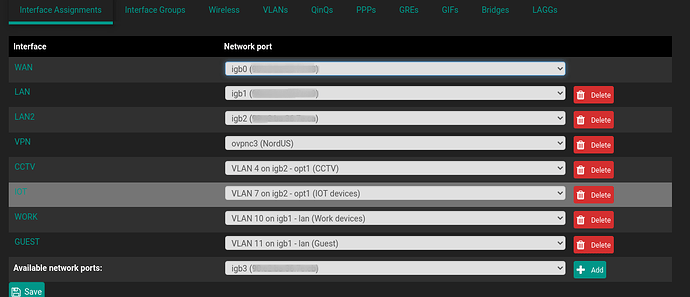
Here’s how my interfaces are assigned:
For each one of these interfaces, I have enabled the DHCP server under Services → DHCP Server
Secondly, here’s my switch config: It’s a Cisco 3750X POE+ switch.
cisco3750X#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/1, Gi1/0/2, Gi1/0/3, Gi1/0/4, Gi1/0/5, Gi1/0/6, Gi1/0/8, Gi1/0/9, Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13, Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17, Gi1/0/18
Gi1/0/19, Gi1/0/20, Gi1/0/21, Gi1/0/22, Gi1/0/23, Gi1/0/24, Gi1/0/25, Gi1/0/26, Gi1/0/27, Gi1/0/28, Gi1/0/29, Gi1/0/30, Gi1/0/31, Gi1/0/32, Gi1/0/33, Gi1/0/34
Gi1/0/35, Gi1/0/36, Gi1/0/37, Gi1/0/38, Gi1/0/39, Gi1/0/40, Gi1/0/41, Gi1/0/42, Gi1/0/43, Gi1/0/44
4 CCTV active Gi1/0/47, Gi1/0/48
5 MAIN active
6 UNUSED active
7 IOT active
10 WORK active
11 GUEST active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
Here are my trunk ports:
Port 45 carries the LAN, WORK & GUEST networks from pfSense to the switch.
cisco3750X#sh run int gi1/0/45
Building configuration...
Current configuration : 164 bytes
!
interface GigabitEthernet1/0/45
description LAN trunk
switchport trunk allowed vlan 1,5,10,11
switchport trunk encapsulation dot1q
switchport mode trunk
end
Port 46 carries the CCTV & IOT networks from pfSense to the switch
cisco3750X#sh run int gi1/0/46
Building configuration...
Current configuration : 217 bytes
!
interface GigabitEthernet1/0/46
description LAN2 trunk
switchport access vlan 4
switchport trunk allowed vlan 4,7
switchport trunk encapsulation dot1q
switchport trunk native vlan 6
switchport mode trunk
end
Port 7 is the trunk between the Switch and the wireless AP (TP Link EAP225)
cisco3750X#sh run int gi1/0/7
Building configuration...
Current configuration : 173 bytes
!
interface GigabitEthernet1/0/7
description Switch-AP trunk
switchport trunk allowed vlan 1,4,5,7,10,11
switchport trunk encapsulation dot1q
switchport mode trunk
end
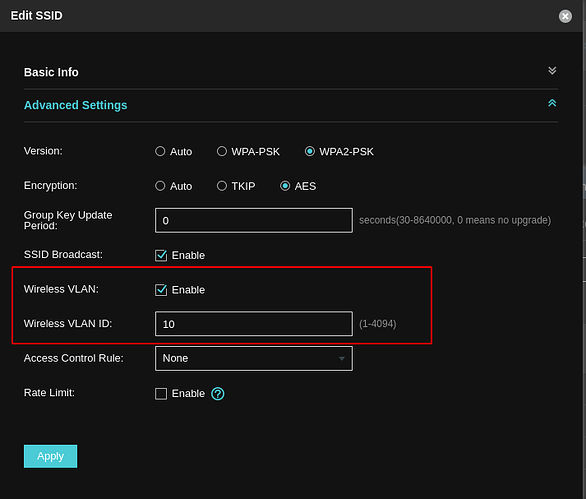
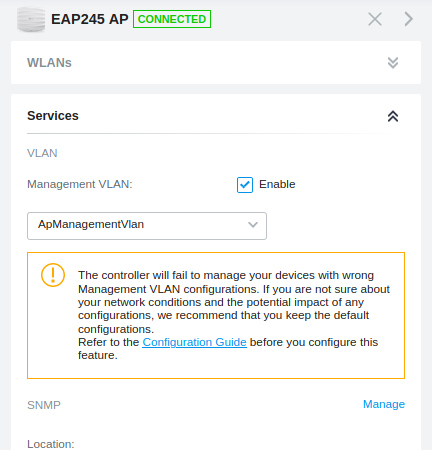
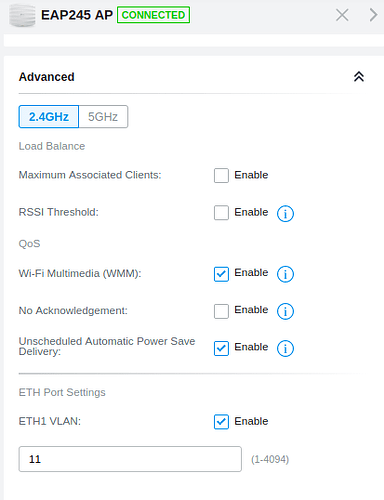
Finally on the AP I have set it up via Omada Software Controller:
The highlighted part is the only difference between the SSID without a VLAN vs a SSID with a VLAN. I have 4 SSIDs with VLAN and 1 without.
My eventual goal is to also move my main LAN to VLAN 5 – but before that, I need to be able to get the GUEST, WORK and IOT networks working correctly.
The aim is to have the GUEST & WORK networks pretty locked down such that they can only access the internet. IOT needs internet access and also access to my media server. I haven’t set that rule up yet, I will once I get the other things working in order.
Would you please let me know what configuration am I missing that these VLANs don’t want to play ball?
Thanks in advance. Let me know if there is any additional information that you might need. Sorry for the long winded post.