Hello all, I am having issues with Remote access being good but users outside my network how being able to always reach my plex server.
If I turn off Snort it works.
I got this reply from Snort and think what he is saying is to do the following
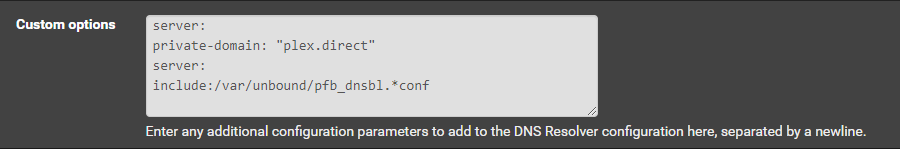
After I turned off the rebind protection it started working. The article says that to add the: below to my current set up
server:
private-domain: “plex.direct”
Are you saying I should add it as using your example above?
server:
private-domain: “https://192-168-9-8.11b1ea3fe92c7b8.plex.direct:32400”
I am not sure about turning off rebind but even with rebind off its 50/50 on if people can access it.
Please let me know what your thoughts are.
That sort of issue would be better fixed with a local host override or just turning off rebind protection for the plex.direct domain. If your having issues you prob have issue with rebind protection. Because the url you could use to access would be something like
https://192-168-9-8.11b1ea3fe92c7b8.plex.direct:32400
Where that would be some random token. You can find that in your xml… go to
https://plex.tv/pms/resources.xml?includeHttps=1You can set plex.direct to not use rebind protection so when you query for that name you get back your private IP. Out of the box pfsense would block getting back rfc1918 for a query and you get back nothing. So you see when I do a query for that fqdn get back no answers.
I then add in the unbound advanced custom box to turn off rebind protection for plex.direct and then I get an answer back of my local IP.
DNS — DNS Rebinding Protections | pfSense Documentationprivate-domain: “plex.direct”
See the rebinding section on the plex support site for https as well
How to Use Secure Server Connections | Plex SupportThe most important port to make sure your firewall allows is the main TCP port the Plex Media Server uses for communication:
- TCP: 32400 (for access to the Plex Media Server) [required]
The following ports are also used for different services:
- UDP: 1900 (for access to the Plex DLNA Server)
- TCP: 3005 (for controlling Plex Home Theater via Plex Companion)
- UDP: 5353 (for older Bonjour/Avahi network discovery)
- TCP: 8324 (for controlling Plex for Roku via Plex Companion)
- UDP: 32410, 32412, 32413, 32414 (for current GDM network discovery)
- TCP: 32469 (for access to the Plex DLNA Server)