Hey all! Just have a quick one for ya that I was hoping you could help with…
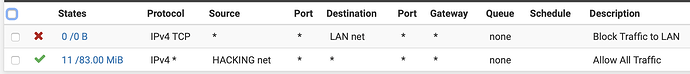
I have PFsense (of course) with a VLAN for Hack The Box. I want the VLAN to not be able to talk to my LAN. Pretty easy, right? I have a screen shot of the simple rules I created. One rule to allow everything, and the other to block everything to the LAN network. Problem is, I can still ping my LAN while I’m on my VM. I am fairly new to PFsense, so what rules should I have set up on the VLAN? Again, I thought this was pretty straight forward, but it didn’t work. Thoughts? thanks!!
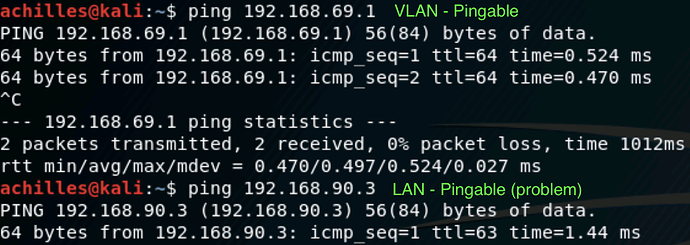
I should mention that I am using a Windows system on my LAN net which houses a VMware instance of Kali which is dedicated to a separate network card in the machine which only receives the VLAN. It’s ip address is from DHCP within that VLAN, but can still ping the LAN net. I’m hoping it’s a PFsense rule that I’ve overlooked, but I admit that it could be something within VMWare… still trying things to figure this out. Any insights are welcome!
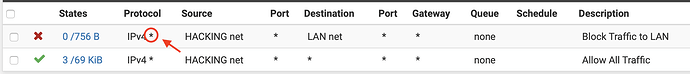
Your block is only for TCP. You probably need to change that to *. I believe that ping is ICMP and thus not blocked.
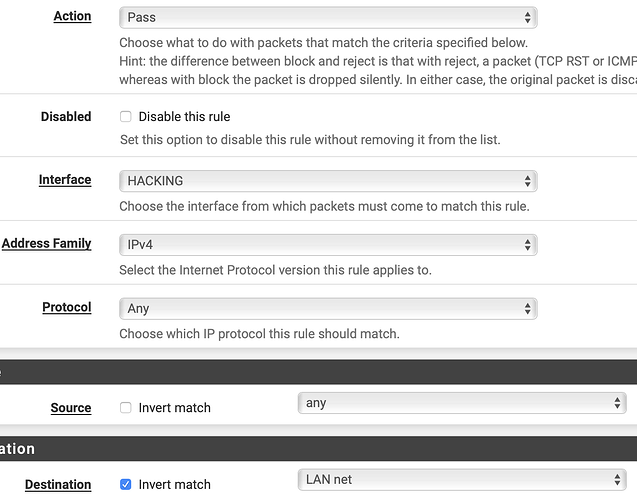
Another way you could do it is having the allow rule with an inverted match to LAN net. That would allow traffic to anything not LAN net.
1 Like
Nailed It!!! Thank you @mouseskowitz
I had just completed a test when you posted this… Here’s the new rule, and you were absolutely right.
1 Like
by the way, I will try your suggestion. I’m already in testing mode, so this is fun. A cool thing about PFsense is you can hit that beautiful APPLY button, and go back to the VM to test right away. It’s not always that easy!
so, you may need to show me the inverted rule… as I have it with the allow and the inversion, it’s still letting everything through…
Here’s the rule I set up…
BTW, thanks for helping us all learn!! Love it.
I’m not that good with inverted rules either. Try specifying the source as the subnet that the traffic is coming from.
Another thing to check is rule order. They are processed from top to bottom and if there is a rule that applies no other rules are checked.
When it came to the rules I found it was better to start from scratch, my aim was security rather than ease of use 
I defined my vlans/subnets in an alias and my ports in another alias. This made it much easier to control the routing between the routing between vLans, the ports took a while to suss out. If you don’t use alias then you end up with more rules and it can be tricky to determine what is actually going on.
So for example, on my Guest vLan I have a Reject for subnet alias. Hence I can see the guest vlan but my guest vlan can’t see the others. Though i have another rule for ICMP as it allows me to troubleshoot, in your scenario i would just reject that rule to block pings.
@neogrid,
the Alias is definitely the way to go. I appreciate the best practices. This PFsense box is for home hacking use, but I have others that connect multiple locations with several different VLANS and subnets. As you mentioned, the rules got pretty complicated, so I may change things around to use Alias… it’s good timing with the businesses being down for a while.