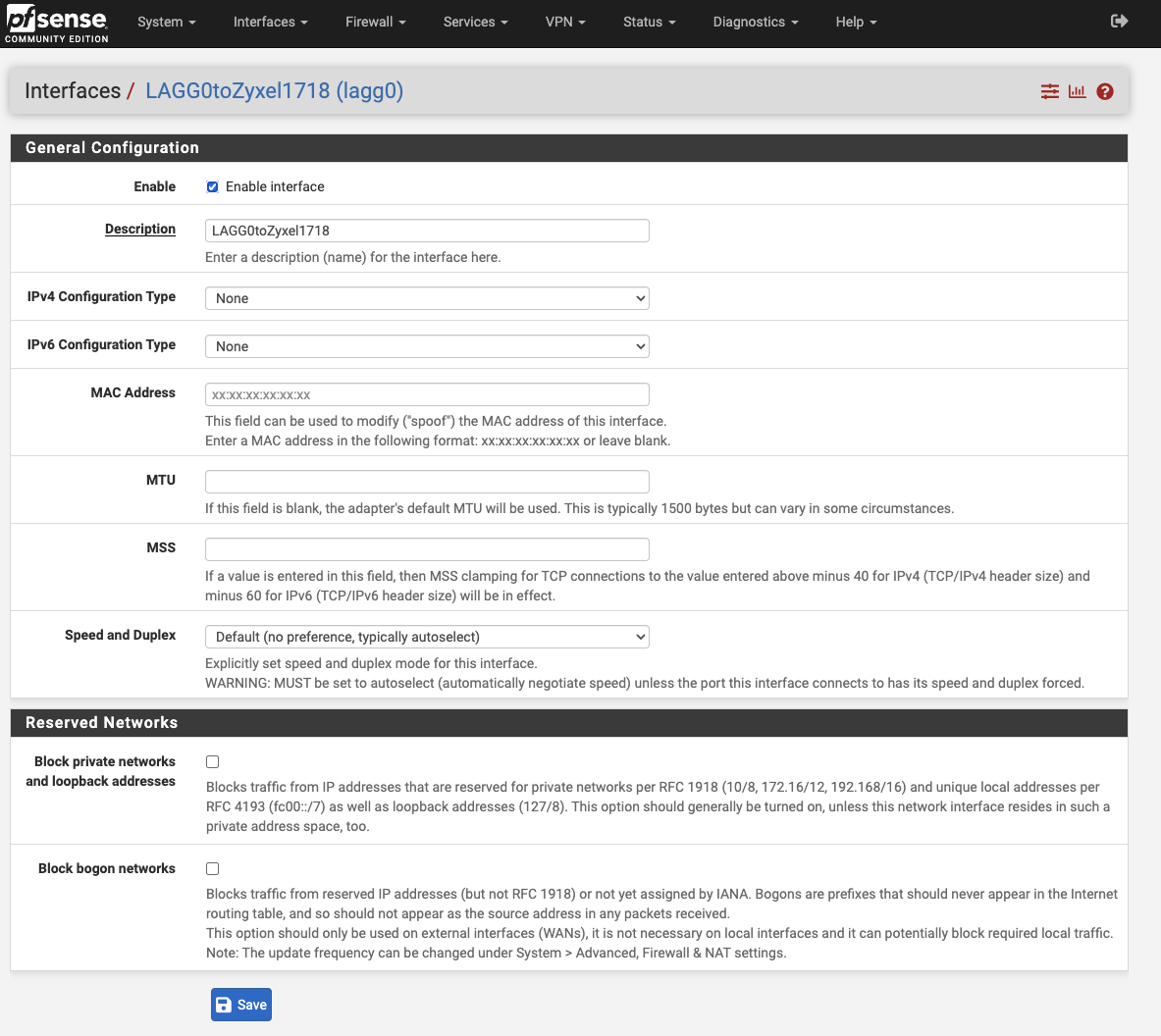
I have a DIY pc (S920 Fujitsu) running pfSense. It has an unused onboard realtek NIC and a four port Intel PCIe NIC: Currently em0 is WAN, em1 is LAN and the em2 and em3 are a LAGG to ports 17&18 on a 24 port Zyxel managed switch. The LAGG is set to LACP.
The LAGG is currently unused as I’m still joining some dots with basic principles and planning - which is complicated by the fact that I need to connect the Zyxel 24 port (which doesn’t do PoE) to a 5 port TP Link PoE managed switch to run a Unifi U6 access point, which has its own GUI to configure of course. This PoE switch will also power a couple of security cameras eventually.
So I’ve got GUI’s for pfsense, Zyxel, TP-Link and Unifi to deal with and they all seem to use slightly different terminology, which makes life interesting! /s
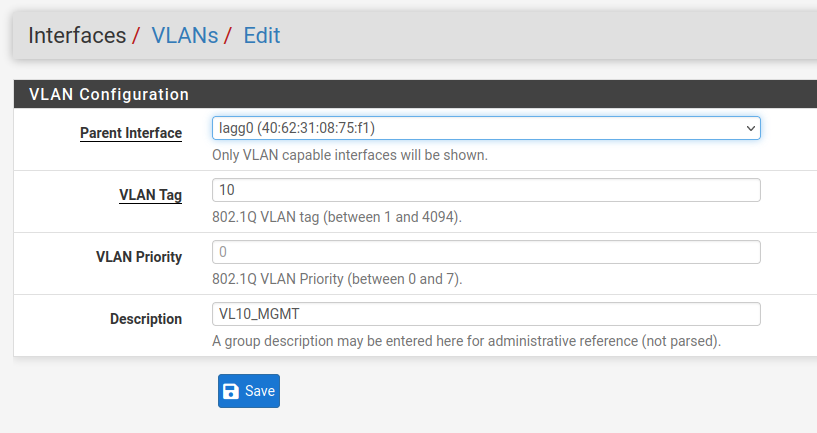
My first question is about setting up the LAGG - this is just to serve as the parent interface for VLANs, so I was looking for some advice about what to do with the LAGG’s own IPv4 configuration. Can I just enable the interface and leave IPv4 set to ‘None’ ? I don’t need DHCP on the LAGG itself, just the VLANs it’s a parent to.
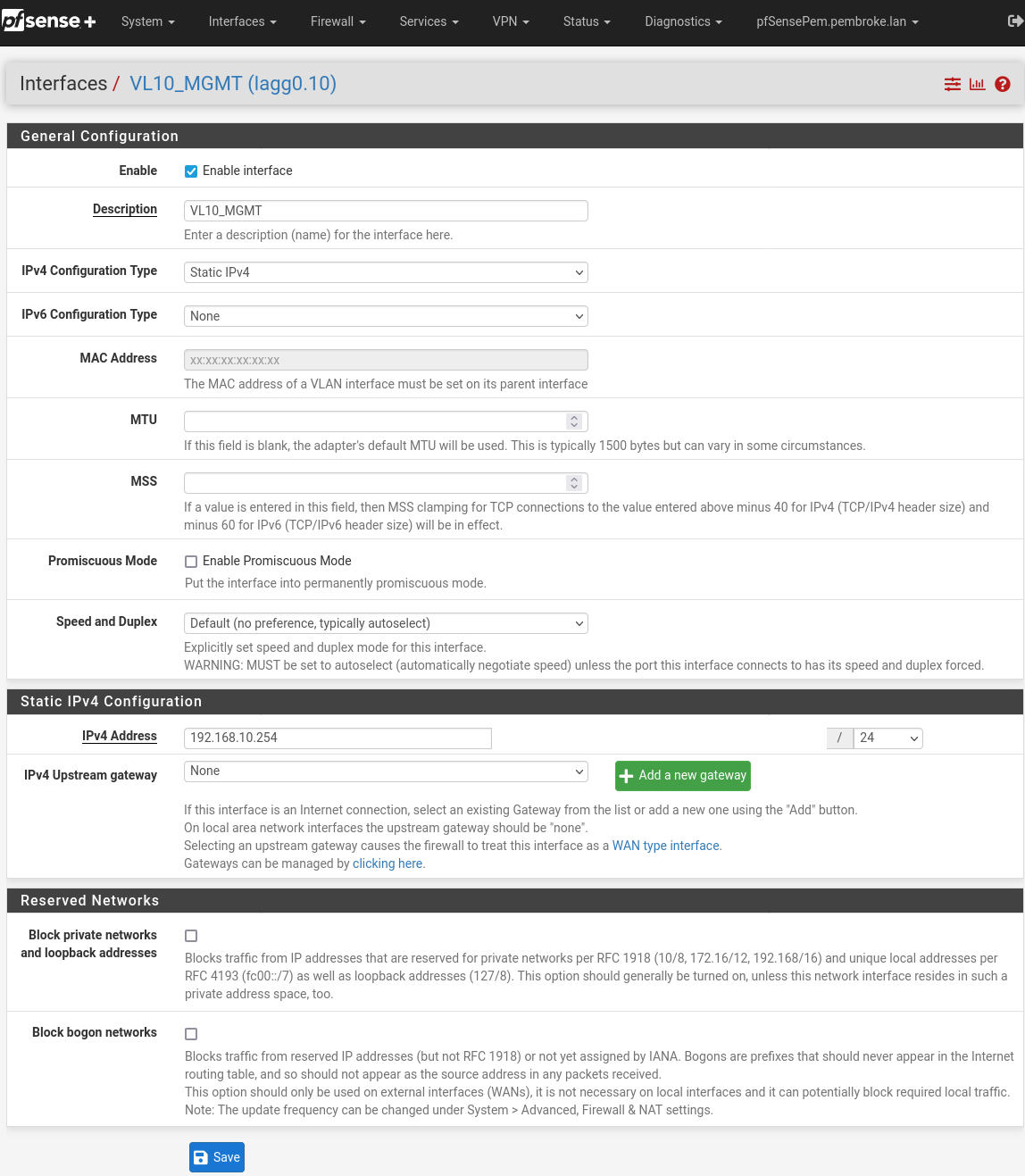
Then add the VLANs and relevant DHCP to this as the parent so that everything going over the LAGG is tagged?
I then need a tagged/trunk port to connect from Zyxel to TP-Link - on this switch there is a 5th non-PoE ‘data’ port which I’ll use for this. The port connecting on to the U6 AP should (I think) also be tagged so it can deal with Home wifi and Guest wifi VLANs.
I’ve also read that I’d ideally change the home LAN DHCP range to something other than 192.168.1.0/24 and I was thinking that a way of doing this would be to have a ‘HOME LAN’ VLAN , say on 10.0.100.0/24 with a corresponding 100 VID, with other VLANs, such as those for Guest Wifi, IoT, CAMs etc at 110, 120, 130 etc. for the third octet and the VID respectively.
The switch ports that connect to various family PC’s and unmanaged switches would presumably then need to be set to Untagged on the switch, while any connection to managed switches would be Tagged and also a trunk port.
Does that sound about right?
If so, how do I go about keeping the current LAN with DHCP range of 192.168.1.0/24 active and working on most of the home network devices (i.e. those belonging to my family) while using my own devices, which have assigned ports on the switch, to test and experiment with?
Right now the switch is just using default VLAN 1 - the ports aren’t set to either Untagged or Tagged, just blank. I admit I’m a bit confused by this - but if I take “Untagged” to mean removing VLAN information from the packet then maybe I should be setting all of the devices ports to Untagged, including those to dumb switches? All the wired home devices have assigned static IP’s in the 192.168.1.0/24 range via the LAN DHCP.
Sorry this is so long - my wife is disabled and totally reliant on a working home network and internet access, so I need to try to make sure things are working properly through testing my own gear before making changes that are going to take me a long time to roll back.
Any advice, including links to videos or other forum posts I should read very welcome. Thanks.