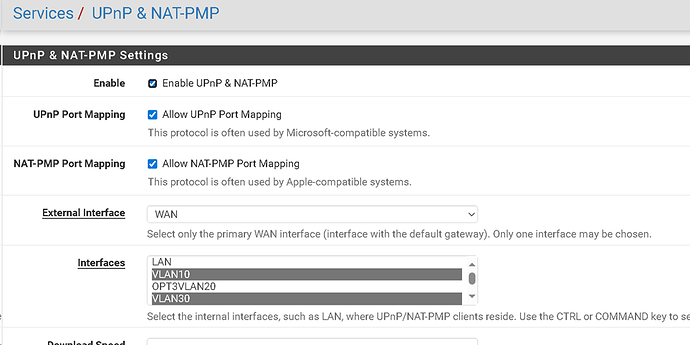
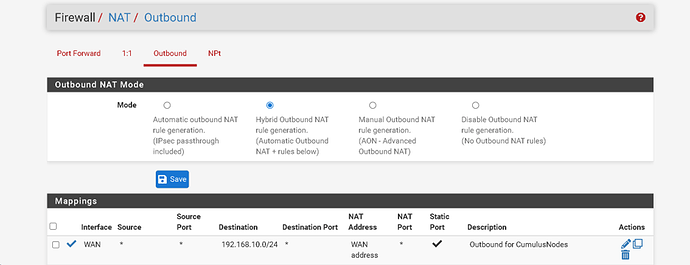
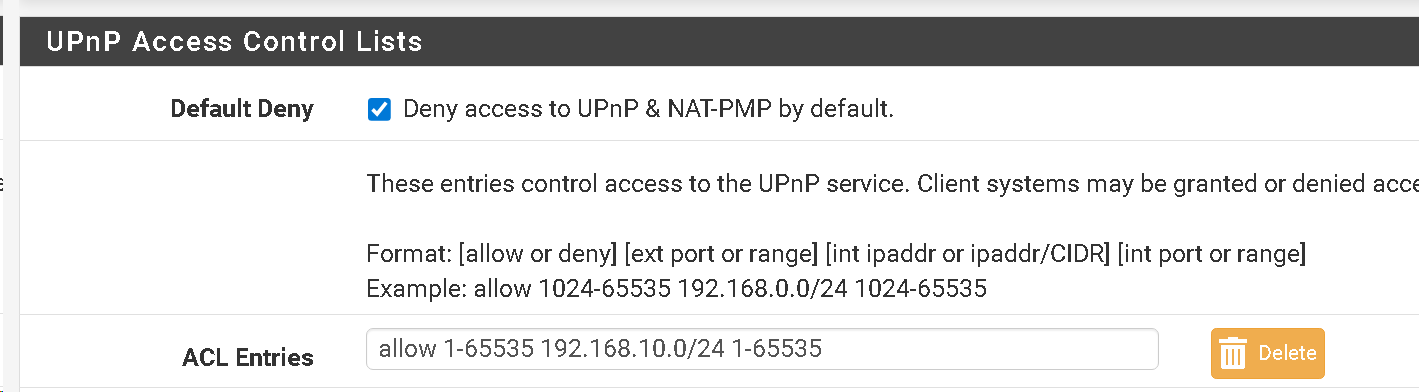
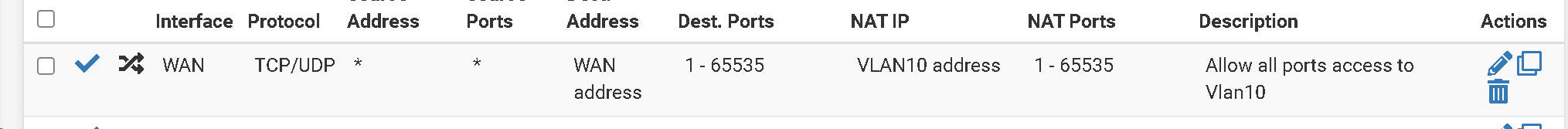
I’m trying to run programs for crypto that specifically require UPnP to be active.
I’m currently running pfsense v 23.09.1.
I have my regular LAN set for 192.168.2.0/24 for my desktops.
I have several Vlans and all are isolated by firewall rules so they can’t communicate to each other.
I setup a separate Vlan 192.168.10.0/24 called Vlan10 for these crypto programs.
The program requires the ability to be connected by random ports from outside the network at various times, thus the need for UPnP.
I was instructed to setup the outbound nat this way as well.
I am still getting errors with the program complaining ports are not reachable from outside.
Error:
Benchmark failed
Reason:
Failed: Error on FluxOs response - Ports tested not reachable from outside, DMZ or UPNP required! All ports that have failed: [12843,12844,12845,12846,12847,12848,12849,12850,12851,12852,12853,12854,12855,12856,12857,12858,12859,12860,12861,12862,12863,12864,12865,12866,12867,12868,12869,12870,12871,12872,12873,12874,12875,12876,12877,12878,12879,12880,12881,12882,12883,12885,12886,12442,12467,12468,12469,12470,12471,12472,12473,12474,12475,12476,12477,12478,12479,12480,12481,12482,12483,12484,12485,12486,12487,12488,12489,12490,12491,12492,12493,12494,12495,12496,12497,12498,12499,12500,12501,12502,12503,12504,12505,12506,12507,12508,12509,12510,12511,12512,12513,12514,12515,12516,12517,12518,12519,12520,12394,11238
There are no firewall rules setup for this Vlan10 so as not to conflict.
FWI I have another entirely different program for another crypto on my Vlan30 that is also setup for UPnP that does not have this problem so right now I’m only focused on the problem above.
Can anyone tell me how to correct this problem?