Additional Resources:
How To Guide For HAProxy and Let’s Encrypt on pfSense: Detailed Steps for Setting Up Reverse Proxy
pfsense DNS host overides
Connecting With Us
- Hire Us For A Project: Hire Us – Lawrence Systems
- Tom Twitter
 https://twitter.com/TomLawrenceTech
https://twitter.com/TomLawrenceTech - Our Web Site https://www.lawrencesystems.com/
- Our Forums https://staging-forum.lawrencesystems.com/
- Instagram https://www.instagram.com/lawrencesystems/
- Facebook Lawrence Systems | Southgate MI
- GitHub lawrencesystems (Lawrence Systems) · GitHub
- Discord lawrencesystems
Lawrence Systems Shirts and Swag
►👕 https://lawrence.video/swag/
AFFILIATES & REFERRAL LINKS
Amazon Affiliate Store
![]() Lawrence Systems's Amazon Page
Lawrence Systems's Amazon Page
All Of Our Affiliates that help us out and can get you discounts!
![]() https://www.lawrencesystems.com/partners-and-affiliates/
https://www.lawrencesystems.com/partners-and-affiliates/
Gear we use on Kit
![]() Kit
Kit
Use OfferCode LTSERVICES to get 10% off your order at
![]() Tech Supply Direct - Refurbished Tech at Unbeatable Prices
Tech Supply Direct - Refurbished Tech at Unbeatable Prices
Digital Ocean Offer Code
![]() DigitalOcean | Cloud Hosting for Builders
DigitalOcean | Cloud Hosting for Builders
HostiFi UniFi Cloud Hosting Service
![]() HostiFi - UniFi Cloud Hosting
HostiFi - UniFi Cloud Hosting
Protect you privacy with a VPN from Private Internet Access
![]() Buy VPN with Credit Card or PayPal | Private Internet Access
Buy VPN with Credit Card or PayPal | Private Internet Access
Patreon
![]() lawrencesystems | creating Tech Tutorials & Reviews | Patreon
lawrencesystems | creating Tech Tutorials & Reviews | Patreon
![]() Time Stamps
Time Stamps ![]()
00:00 ![]() DNS and Certificate Troubleshooting
DNS and Certificate Troubleshooting
00:40 ![]() What is SNI (Server Name Indication)?
What is SNI (Server Name Indication)?
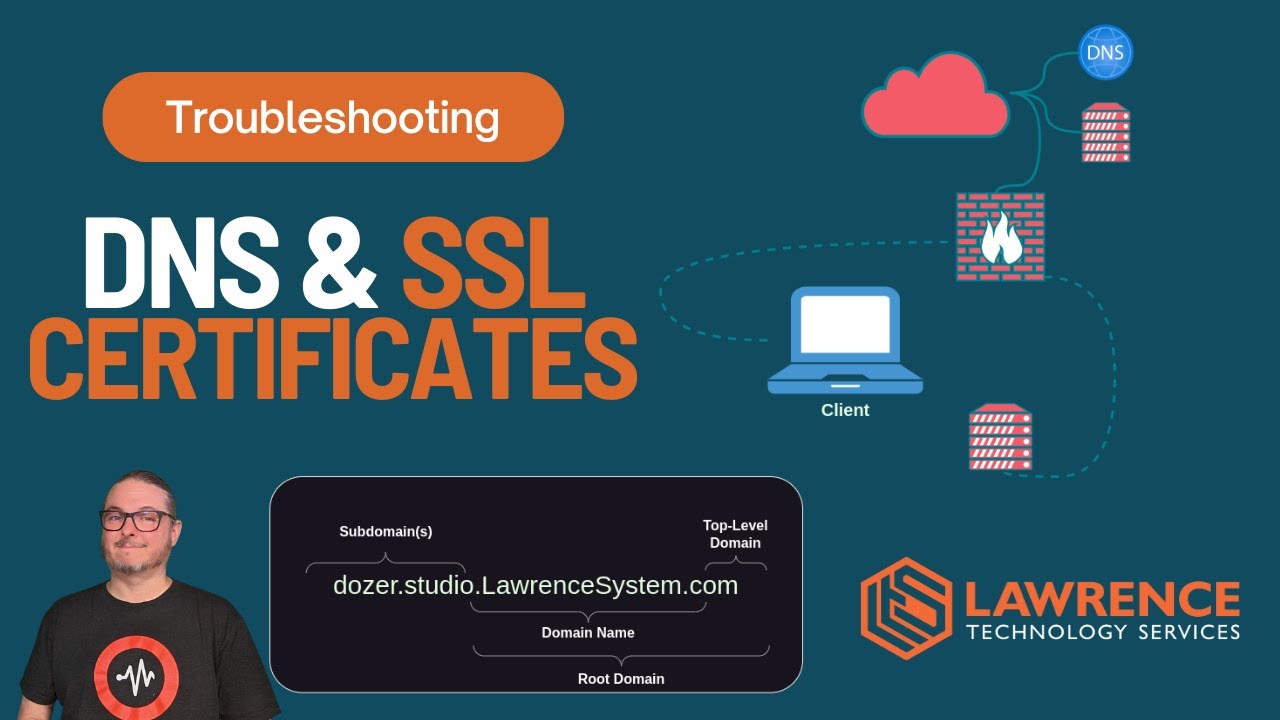
02:33 ![]() Understanding How Domains Are Structured
Understanding How Domains Are Structured
04:34 ![]() DNS Host Overrides
DNS Host Overrides
05:17 ![]() Using DIG for DNS & OpenSSL for Certs
Using DIG for DNS & OpenSSL for Certs
#network #dns #pfsense