Hello All,
Longtime YouTube viewer, brand new forum user. Apologies if my questions are n00bish or just plain stupid. Multi-tiered architecture design is completely new to me.
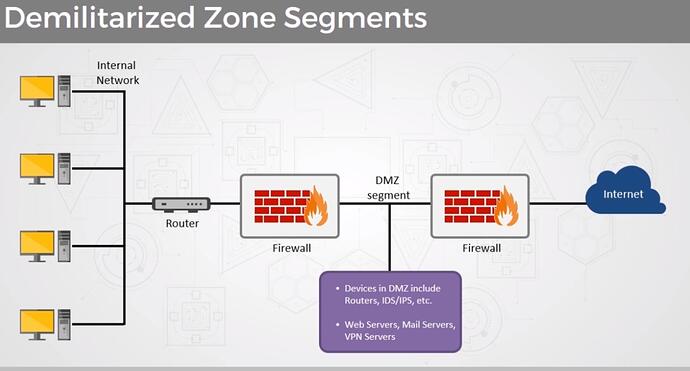
I’ve been searching for information around a two router setup for better DMZ management and I have hit something of a wall from a practical standpoint. I understand the concept of using an edge-of-network WAN router to control the DMZ and a separate LAN router to further secure personal machines, but I’m having trouble grasping how I do that.
First and foremost, my concern is double NAT. I know I can disable NAT entirely, but if I know anything about networking it’s probably only one of many things I need to do. I have some vague notions about using a static route to point to the upstream WAN router, or to use a gateway definition (?) but I’m otherwise clueless.
This diagram captures generally what I’m looking for…
-
WHY do I want to do this?
– Practice, and the advantage of using distinct physical devices/software to manage the devices that should be publicly accessible, and the devices that shouldn’t. This is just generally good practice from what I understand. If a vendor-provided software like pfsense is exploited (unlikely, but possible) at the DMZ level, the chances of the same exploit being present in a lower-level router are pretty high. -
HOW do I want to do this?
– I have a dedicated physical router with OPNSense I would like to use as my WAN router
– I currently use a virtualized PfSense router for pretty much everything, including my various VLANs, firewall policies, etc. I want to have this machine only handle my internal machines, and to point their traffic up the chain to the WAN router
– This virtual machine runs on the same physical hypervisor as my access bastion (basically useless security at that point if the hypervisor were ever compromised)
– I’d like the WAN router to handle traffic to/from the DMZ, to contain the port-forwarding rules needed to access them, and to keep LAN traffic completely separate from the DMZ
Any and all help is appreciated and thank you ahead of time
Edit 1
My WAN Is a single public IP. This is for a homelab setup and learning purposes only.