Hello all,
I am seeking assistance properly configuring Wireguard on pfSense to work with Mullvad VPN. I have followed Mullvad’s setup guides closely, but am having some confusion around the best practice for configuring NAT rules, firewall rules, and DNS settings.
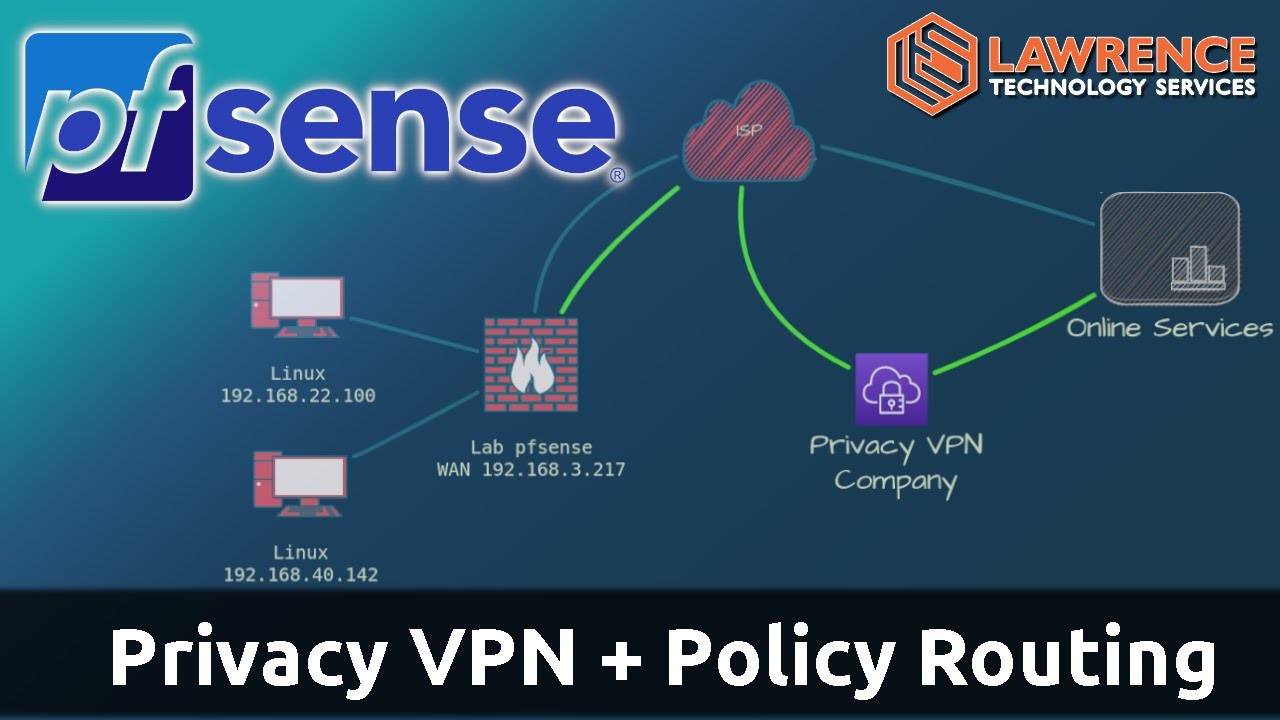
My goal is to tunnel all traffic from my LAN out through the VPN tunnel securely. However, I have come across inconsistencies between guides on how to correctly set up the NAT rules to force LAN traffic to Wireguard, firewall rules to allow/block traffic, and DNS settings to prevent leaks.
Specifically:
- Mullvad’s guides do not cover NAT configuration while Netgate’s Wireguard docs suggest specific NAT outbound rules to route LAN traffic. I am unsure which guidance to follow.
- For firewall rules to allow Wireguard traffic from LAN while blocking other unfettered LAN to WAN access, I have seen conflicting advice on the best configurations.
- DNS configuration is called out as critical for preventing leaks outside the VPN tunnel. But specifics vary across blogs/videos on the ideal setup here.
I am running pfSense 23.09 + on Netgate 1100 hardware. My core objective is simple and consist in routing all LAN traffic over WAN through the encrypted Mullvad tunnel and confirming no data or DNS leaks occur circumventing this.
Any advice from the community on the correct way to configure the NAT, firewall rules, DNS, and confirm through testing that there are no leaks would be tremendously appreciated. Please let me know if any other specifics around my setup would help diagnose the optimal configuration.
Thank you sincerely for the help!