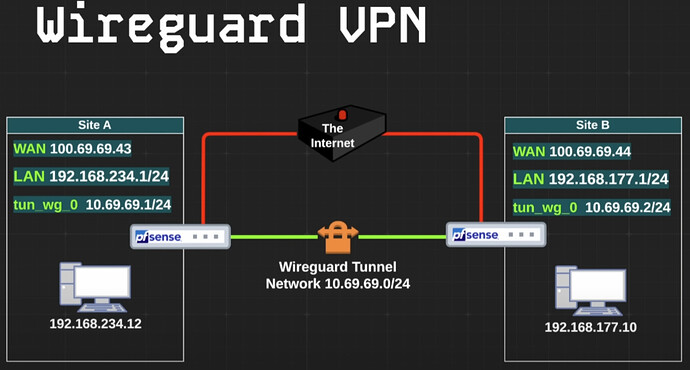
I was watching Tom’s video about configuring a site-to-site VPN using WireGuard (https://www.youtube.com/watch?v=WXkWP-JZOd8&t=703s) between 2 pfSenses, where he showed this diagram:
Assume everything that he showed on that diagram is already working for me (i.e. site A can access LAN IPs on site B and vice-versa)
I would like to do the following:
a) route all non-private (i.e. non RFC1918) traffic from Site A (192.168.234.1/24) to Site B and out to the internet through site B’s WAN gateway (100.69.69.44) → goal is to use Site B’s WAN as the egress point of all non-private traffic originated in A.
b) route all non-private (i.e. non RFC1918) traffic from Site B (192.168.177.1/24) to Site A and out to the internet through site A’s WAN gateway (100.69.69.43) → goal is to use Site A’s WAN as the egress point of all non-private traffic originated in B.
What configs do I need to add (gateways, static routes, allowed IP’s in each of the peers, policy-based routing, etc) that accomplishes this?
I tried allowing 0.0.0.0/0 on both peers but that appears to cause some kind of conflict.
Thanks!
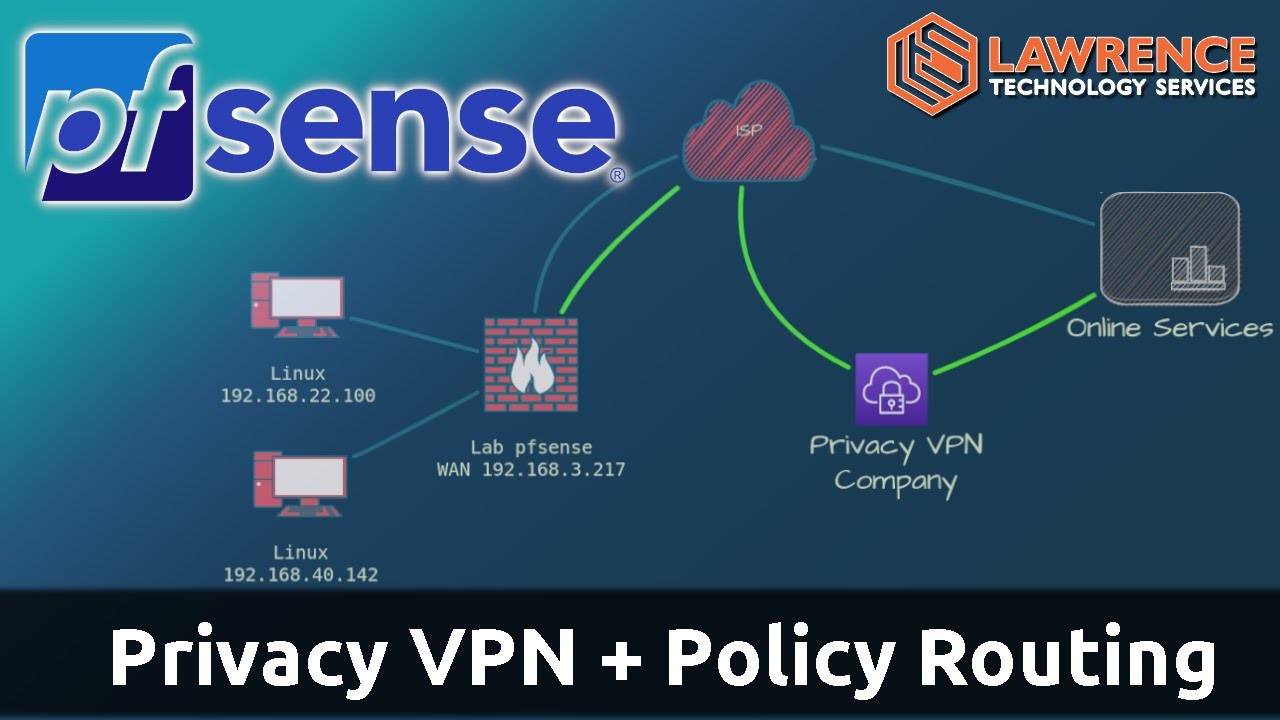
Not something I have done because I think it’s a bad idea, but you should be able to build a rule for each network that uses WG gateway for egress. It would be similar to how I do it in this video:
Funny you mentioned that video, that was one of the first ones I saw on your channel which made me start using pfSense!
Can you elaborate on why you think it’s a bad idea? Do you dislike the general principle of what I’m trying to do or the implementation choice?
My intended use case is to simply allow users in site A and B to bypass geoblocking and have an egress point in a different country. Each site has a WAN IP from traditional ISP’s which avoids all the VPN detection from some sites (including streaming) that I would encounter were I try to use commercial VPNs… both LAN A and LAN B are in dedicated VLANs in their respective sites, with other local VLANs for other uses (IoT, cameras, DMZ, computers, servers, etc…)
I avoid that setup because it add latency and if the main site goes down it breaks the internet. An alternative is to create policy rules that only push the traffic over the VPN that is needed for the site services that care about where the IP is geo located.