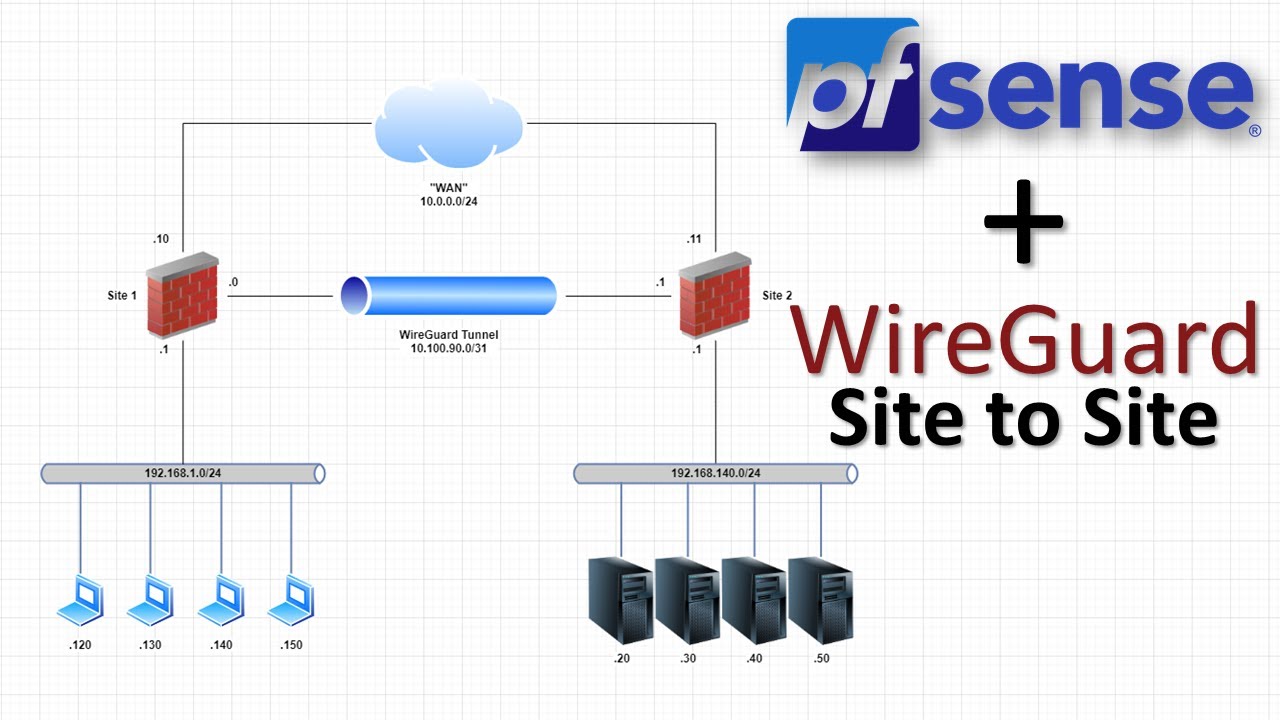
Hi there,
I am using pfSense on multiple sites and they are connected by wireguard site-to-site tunnels. The incoming connections have firewall restrictions to make only specific hosts reachable which works fine.
What doesn’t work is to restrict the incoming IP addresses. I assume that is because the traffic ist NATed by the Wireguard Gateways on each device. The incoming traffic is virtually originating from the remote gateway, not the real remote IP address.
What I would like to achieve, is a mac-filtering for the devices which are allowed to enter the tunnel. I read about captive portal and would give that a shot if you tell me that could work.
Is there another solution to restrict tunnel entry?
Thanks Sebastian
MAC addresses function at the data link layer which is layer 2 in the OSI model and Wireguard only supports only layer 3.
That much I know.
My question was rather how that could be achieved?
Thanks, Sebastian
Watch Christian’s Wiregaurd site to site video, he covers how to do it with out NAT.
Thank you very much!
Great link!
Sebastian
I have been able to route traffic without NAT over the Wireguard site-to-site tunnel.
What I would like to achieve is Mac address filtering through the Pfsense captive portal.
I understand that the packets going through the tunnel are using a gateway on each Pfsense, but not the standard gateway which would provide the captive portal filtering/login. Is that correct?
Is that why there is no login page / filtering applied?
Can that be achieved?
Thanks, Sebastian
Not something I have tested.