Wow, thanks fo the detailed response @BuckeyeNet. I’ll be looking up more information about this configuration over the weekend as well.
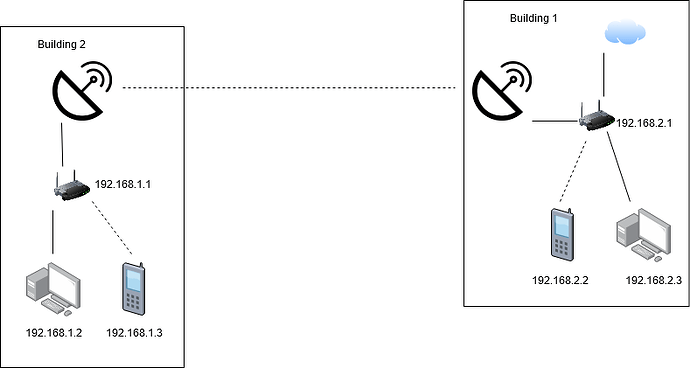
Just to clarify, the RTR2 eth1 default gateway is 192.168.215.1, but all devices on the 192.168.214.x should use 192.168.214.1 as their gateway (since the 192.168.214.x devices would not know how to reach 215)?
Yes, if RTR2 has a dhcp server configured, it should send its own 192.168.214.1 address as the default gateway for its clients. The RTR2 router itself should forward packets that are not on any of its connected networks to RTR1’s eth2 (192.168.215.1). Once the packet gets there, RTR1 will route to appropriate network (either 192.168.213.0/24 out RTR1 eth1 or to internet after being NATed)
Example client leaving the network:
192.168.214.3 → 192.168.214.1 → 192.168.215.1 → ISP IP
As well, for RTR1 and RTR2 what IPs would they assign themselves on the 192.168.215.x side? Since you gave the IPs for the transmitters, unless you mean those are the IPs for the router on either end of the transmitter and the transmitters themselves should be assigned 192.168.215.3 for example.
I was just treating the transmitters (P2P wireless) as a wire (this is just a conceptual overview or one possible way to approach the problem). I would configure the P2P radios in bridge mode. For management, you could use a separate vlan on the inter-building link (i.e. you could carry the 192.168.215.0/24 via a tagged vlan and the radios management interface could be on a separate subnet (e.g. 192.168.216.0/24 or you could split the 192.168.215 into two /25 subnets, but private ip address space is “free”). Each radio should have its own management ip address, and best practice is to prevent access to the management interface from the users in the buildings (and the internet) using the firewall in the RTRs.
Since RTR2 is not doing any NAT masquerading, is it not just doing what a basic consumer router is doing with a WAN port being eth0 and the LAN being eth1?
Many consumer routers don’t allow you to disable NAT. They are “hardwired” for the home use case that 99.99% of the users will use, a connection to a single ISP on the WAN interface, and a single LAN (likely connected to an internal 4 port switch and bridged to a Wifi).
A router like the Ubiquiti ER-X does not have any Wifi built in, but for most use cases, having separate Wifi Access points is much better, because where you have the router is probably not the best place for an Access point. So having a router that has a wifi built in is of limited value in most businesses. They may be ok in a small home, but once you use separate access points, you will never want to go back to an all-in-one Modem/Router/wifi device (at least I won’t).
For your use case, (depending on the number of users, which you haven’t mentioned), a device like an ER-X at ~ $60 - $65 is a much better fit. It is much more flexible, supports multiple routed interfaces, vlans, etc. in other words, it is a more general purpose router.
Plan on purchasing some access points. Ubiquiti Unifi is what I would use, but that’s what I have at home, so I am biased. But see Tom’s reviews as to why he likes them.
I haven’t used the SG-1100 pfsense device, and depending on the number of users it may be able to handle the load, but may not. There are larger models, and you can also load pfsense on a PC for more horsepower.
The outline I gave is pretty generic (although I used ER-X terms for the router interfaces).
Thanks again