I have spent two solid days trying to figure out my port forwarding issues to no avail. Everything was working until I updated my pfSense to 2.5.1. I revisited pfSense troubleshooting guidance and Lawrence’s guidance videos on port forwarding but still having issues.
Regarding my home network setup. I have a pfSense router at 192.168.0.1 I have the following interfaces:
(1) WAN
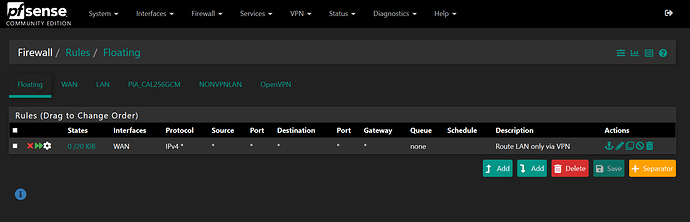
(2) LAN (vpntraffic only and used for all personal computers) 192.168.0.X
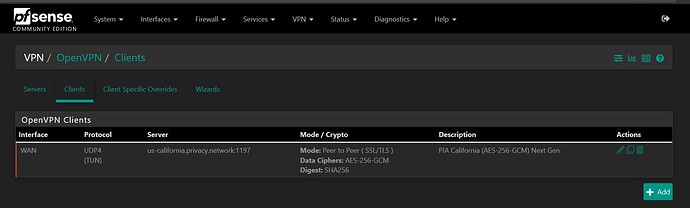
(3) PIA OpenVPN client
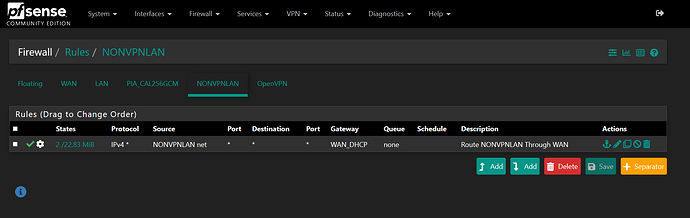
(4) NONVPNLAN (on a VLAN through a ubiquiti managed switch - used for my business computers) 192.168.1.X
For VPN traffic computers on (2) LAN interface, I used Lawrence’s guidance (pfsense OpenVPN Policy Routing With Kill Switch Using PIA / Private Internet Access - YouTube) and it works perfect. For non VPN traffic computers on (4) NONVPNLAN interface, I have a separate VLAN network and it works perfect.
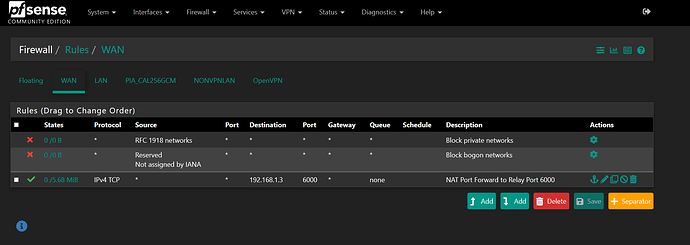
I followed this video for Lawerence (How To Setup Port Forwarding on pfsense 2.4 - YouTube) to set up a port forwarding rule to send all external TCP internet traffic packets on port 6000 on WAN to single computer on the (4) NONVPNLAN (VLAN) with an internal address 192.168.1.3 on port 6000. However, when I check on (yougetsignal port forwarding testing tool website) to see if the port forwarding is working, the results show my external IP address on 6000 is CLOSED.
To troubleshoot, I first wanted to make sure the port forwarding rule on the WAN was working. So I monitored Status>System Logs>Firewall>Dynamic View and filtered all requests to my 192.168.1.3 computer destination and then did a test again on (yougetsignal port forwarding testing tool website) to my external address on port 6000. I was able to see that the port forwarding rule passed the TCP packet to my 192.168.1.3 computer without blocking it. So it looks like the port forwarding is working on pfSense.
I then took Lawrence’s recommendation for test the port in Diagonstics > Test Port to ensure I can send a TCP packet on port 6000 between the pfSense router (192.168.0.1) and the computer on 192.168.1.3 that is listening on 6000. The results show successful, so I that means I have clear communication between pfSense and the computer on 192.168.1.3 on port 6000.
The last thing to check was to check directly on my computer 192.168.1.3 that it was actually receiving the TCP packet when I sent a TCP packet from (yougetsignal port forwarding testing tool website). I ran a tcptrack command on my 192.168.1.3 computer to monitor port 6000 and can see that 192.168.1.3 computer is receiving the packet…
So in summary I am very confused why on (yougetsignal port forwarding testing tool website) I see that my my external IP on port 6000 is showing CLOSED when I can see the TCP packet being received on my 192.168.1.3 computer. At this point I am at a dead end in trying to solve this after two solid days…
Is there any other methods to further troubleshoot to see where the issue could be or does anyone know what could be the issue? Any assistance would be greatly appreciated!!!