I’m a techy, geeky person, but have never had my own space to really plan my networking. I’m also a minimalist (a vague term for almost everything) and don’t want to spend or have more than I actually need. I’ve already networked several floors and a garden area with UniFi and know how to use it, and I’ve build my own cables, PCs, etc. All in all, I’m far from an expert, but I know enough that home networking can be so much nicer with a little effort (and money). I also hate the fact that my ISP multi-function device (‘router’) doesn’t get timely security updates.
I want to repeat myself that I am between noob and expert. So I want to lay out some ideas and questions so that more experienced forum members can tell me if my plans are good or bad.
My current situation is that I live with my family on two continents. I would like to share files safely between us. I have a ton of files and a solution where all family pictures, videos and media files are stored at one location sounds fantastic. I have used Synology a bit but for planning my new setup, I have been looking at TrueNAS Core and would like to build my own NAS box. Building a PC is not difficult (and I have done it several times). However, before I build a TrueNAS Core system (the free community edition), I’d like to know the best way to make it externally accessible in a secure manner.
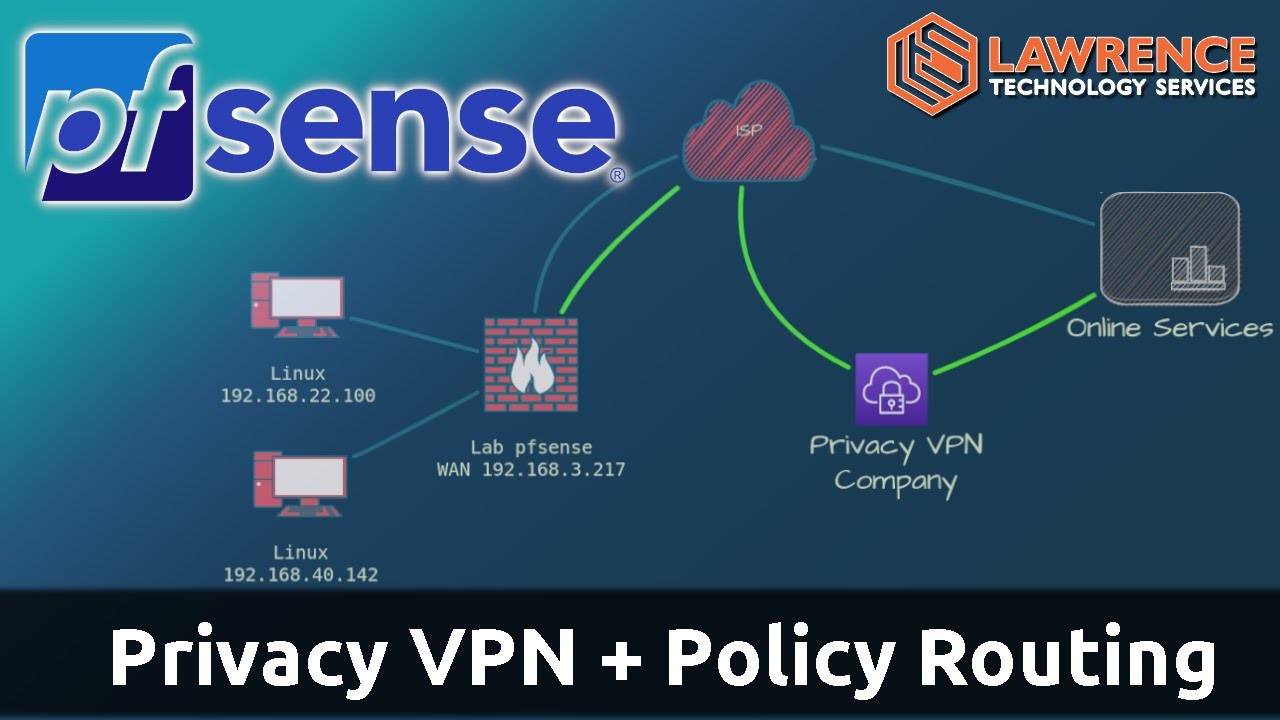
You may see that I want a bit more than just good WiFi. My focus is on privacy and security, and I don’t like vendor systems with registration which phone home all the time. To be flexible with my router settings and also get updates quickly, I want to stick my nose into pfSense. It doesn’t seem too complicated and seems like the perfect product for an open source enthusiast. What hardware would you recommend? The Netgate devices? I need to route 1Gbps (both directions) and also would like to run my own VPN for default encrypted connections.
I also think I’m right about this - but this is something I’d like clarified - that pfSense can be configured with WireGuard so I don’t have to open ports on my router. Is that correct? To be clear this is for accessing my networking securely and not to hide my traffic from my ISP.
Additionally, I’d like to know if pfSense has an option to easily integrate WireGuard for a VPN connection to a public VPN provider like Mullvad.
Back to the VPN for secure connections to my home network: I would also like to know how to access my WireGuard VPN (the one to connect to my home network) without a static IP from my ISP. Is DynDNS the solution for that?
As for my ISP: I have a 1Gbps connection with fiber optic cables. I think I can use my regular ISP router in a bridge mode or do a double NAT to be able to connect my other RJ45 cables.
Since I’m streaming for work, I think I’ll wire all my office equipment with a tiny switch and also provide a second switch for my second office and my NAS box (media server, Vaultwarden, etc.).
Also, I may want to play with PiHole and some other media related server applications, but that is still in the future. I’m aware of the TrueNAS jails, but I want to use the systems exclusively for storing and sharing files.
If I set up a VPN connection on my pfSense router so that I can connect from outside of my network, my family and friends would have to switch to the VPN connection. However, since I also run my own VPN server for my family and friends, I would like to ask if there are any security concerns if I do not set up a VPN on the pfSense box, but instead limit port forwarding for the NAS box to the public IP of my VPN server. That way there would be no need to change VPN and create a VPN to the NAS or VPN to something like Mullvad situation (on/off situation).
I would also like to use Vaultwarden. It’s pretty minimalistic and I think it would be something for a Raspberry Pi 4. How do I secure the instance so I can connect to the server with maximum security? The VPN solution with WireGuard and pfSense again?
Next, I would like to have good Wifi. I liked and used UniFi before, but I heard that you have to register to use the new devices since a software update. I don’t like that if it is true. Is this true? Is there a good alternative? I would like to have a mesh network with one device connected only to other AP via Wifi in an outdoor scenario. Also, I have two floors and I think one AP on each floor with cable uplink would be sufficient. Of course, I want roaming functionality so that I have a Wifi network that is powered by all APs and I can switch seamlessly as I go up and down my apartment.
In regards to TrueNAS, I would also like to know what the best backup solution is for the box itself. One solution would be to replicate the box to a second box on the other continent. Is this possible with TrueNAS performance? What advantages can I get from this? Isn’t this just redundancy and not a true backup? I would appreciate if someone could bring some clarity to this issue.
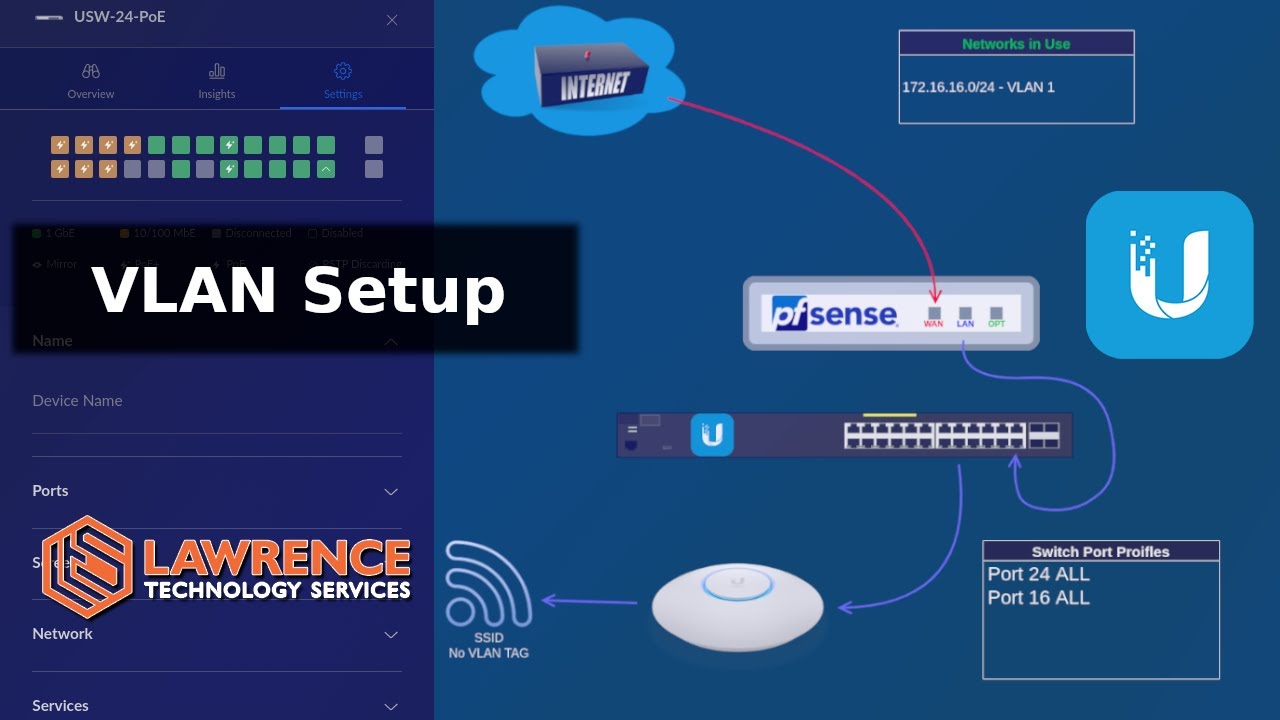
Finally, I would also like to decrease the risks by using VLANs so that all devices have to be “smart”. For example, I would like to separate devices like guest devices or my gaming consoles that don’t need to see the rest of my network topology.
Sorry for the long text, but everything is connected (literally), so please help me get out of this cyclical loop of questions.
Summary: I have a 1Gbps fiber cable that I would like to connect to a pfSense router. From there I connect two switches (one for my main office and the other for the other office and home server stuff). I would like to securely access Vaultwarden from outside of my home network. 2 wired APs and one AP connected via Wifi (mesh) is needed too. Everything should be able to be separated by VLANs. Is that plan good bad? Where can I improve or are changes needed? Please answer my questions and provice some input.
Thanks!!!