Hi all
Hope everyone is well. Hitting my head on the table at the moment . Not sure if this issue Im facing is due to a mis-config, or some undocumented behavior with the consumer smart switches Im using (GS105E & TL-SG108PE).
Would be grateful if I could get another pair of eyes over the setup and config.
Like many I’ve attempted to moved my flat home network into a VLAN setup. And to be honest, using the two consumer switches was a bit of a mission. Though so far, its working, except for the ping issue.
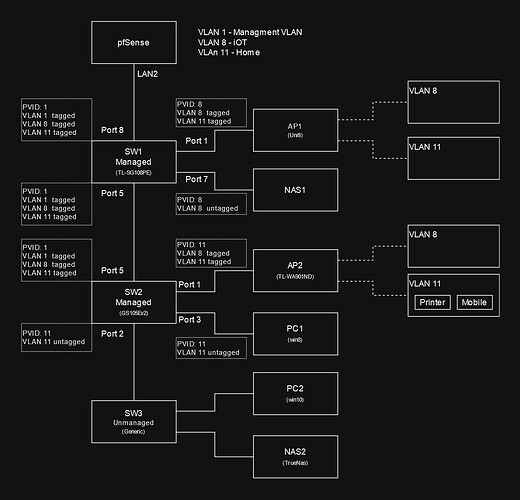
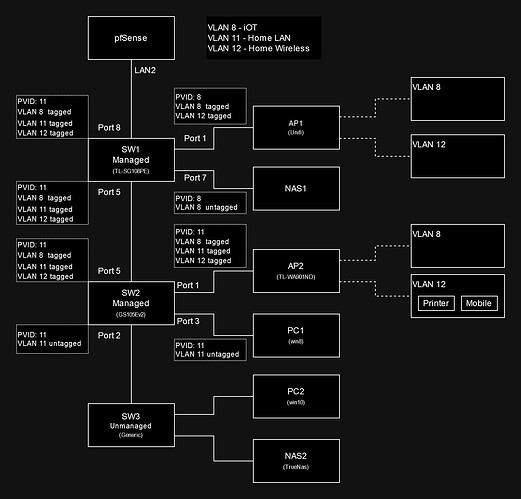
Network layout:
.
All VLANs are setup under 802.1Q in the switches, port-based VLAN is disabled.
Devices in VLAN11 can access everything, WAN and devices in VLAN8.
Devices in VLAN8 can access WAN, blocked from VLAN11.
PC1 and PC2 are under VLAN11, both have IPs provided by the DHCP server in VLAN11 (within pfsense). Can access WAN without a hitch. Can ping all devices in VLAN8 without issue.
PC1 and PC2, have no problem pinging any LAN devices.
For those who are wondering why VLAN1 is the management VLAN. Mainly because the switches seem to refuse to get an IP from any other VLAN except for VLAN1. I feel maybe there is a bug with the switches or something Im not understanding with the configs.
========== ISSUE ===============
PC1 and PC2 cant ping the wireless printer under SW2.AP2.VLAN11, unless the printer is freshly booted while the PCs are on. Ping error below.
Reply from PC-IP: Destination host unreachable
Similar issue occurs with the mobile. Both PCs are unable to ping the mobile unless the mobile pings the PCs first. Once the mobile initiate the pings to the PCs, thereafter, the PCs would be able to ping the mobile device.
Same issue occurs if the network adapter is disabled and then re-enabled on the PCs. Both PCs would lose the ability to ping the wireless devices under VLAN11, but still ok with devices in VLAN8.
Checking the ARP table. Once the network adapters is disabled and re-enabled, most of the entries in the ARP tables disappears. Some entries do come back, but the wireless device’s ARP does not appear unless they are rebooted or a ping is initiated by the wireless device.
=============================
Any thoughts or pointers is greatly appreciated ![]()
![]()