I have set up Wireguard on my pFsense SG5100 and my iPhone based on the Tom’s video. (THANK YOU). This creates a split tunnel - traffic to the SG5100 goes through the encrypted WG tunnel and other traffic does not (unencrypted). How do I configure pFsense to send ALL traffic through the tunnel with traffic to external sites going via through the SG5100 . On the iPhone, I have added 0.0.0.0/24 as an allowed IP.
Any suggestion would be greatly appreciated.
Change the allowed IP’s to 0.0.0.0/24
I also needed to add DNS = 8.8.8.8
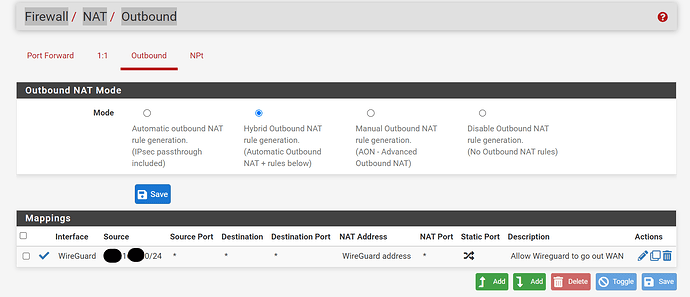
You have to create a NAT rule ,
https://youtu.be/8jQ5UE_7xds - time 9:25
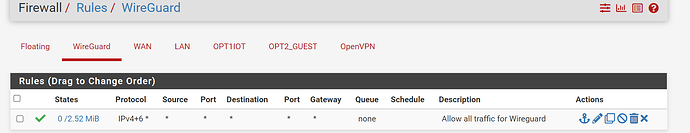
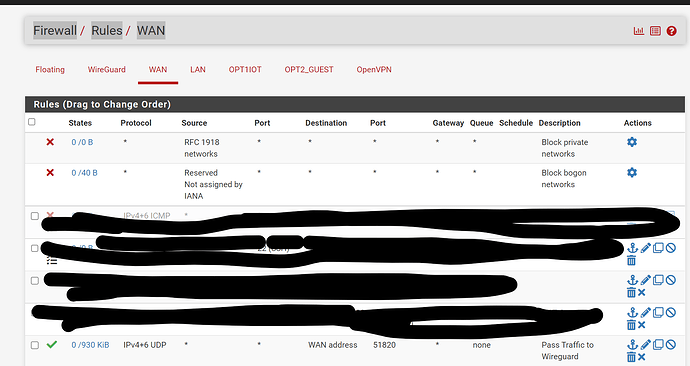
Firewall rules - just make sure you are not blocking the traffic from the vpn client. - you have a allow all rules on the wireguard network
Thank you. I believe I already have the rule you suggested:
Allowed
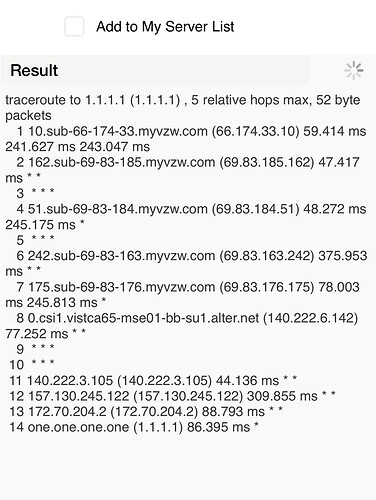
As you can see the tracert goes from Verizon through some intermediary nodes to 1.1.1.1
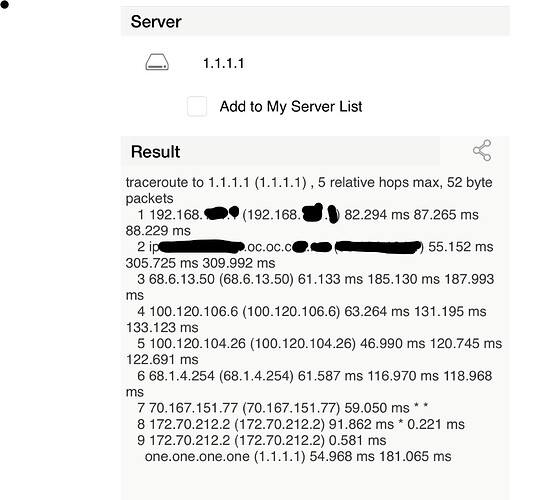
I then compared it to my OpenVPN in which the tracert shows that it is going through my OpenVPN tunnel.
Any additional suggestions to direct traffic from my iPhone through the pFsense 5100?
Have you created the outbound nat rule ?
Try 0.0.0.0/0 (not 24) on both the iPhone and the peer configuration for the tunnel.
0.0.0.0/0 on my iPhone did not work. I could not tracert internal to my network or external to my network addresses.
I don’t know what you meant by the peer configuration for the tunnel. thanks
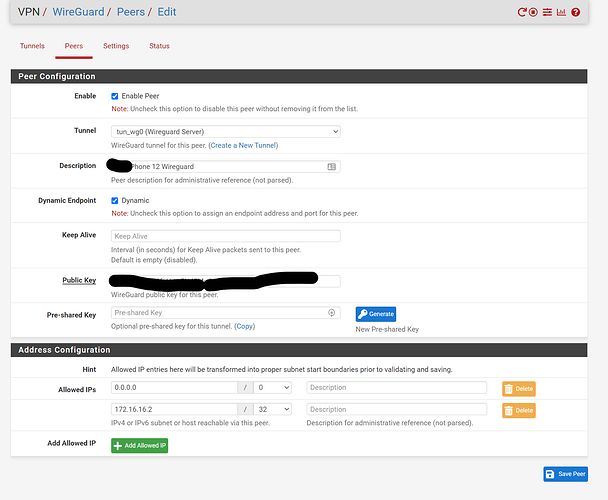
Sorry about the lack of clarity. In pfSense, go to “VPN”, “Wireguard”, “Peers”. Select the Peer for your iPhone, and edit that. At the bottom is the Address Configuration where you list the Allowed IPs. Use 0.0.0.0/0 there.
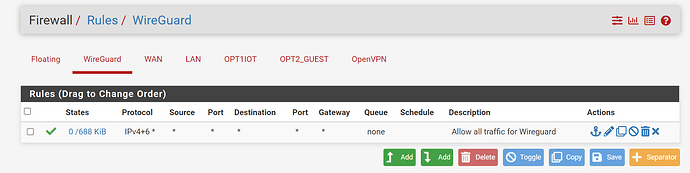
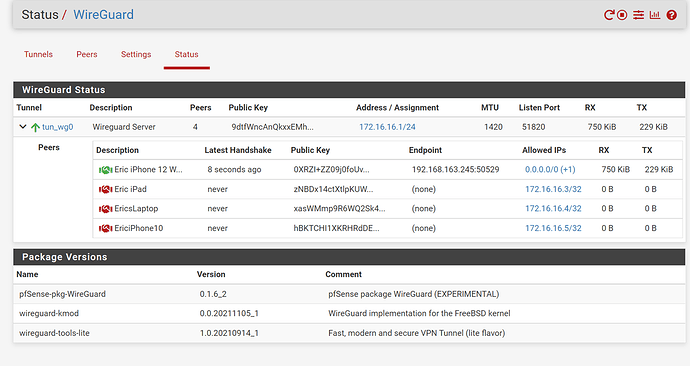
The internal network works as before. However, I still cannot get the remote device to send traffic externally through my pFsense. I have include more pFsense configuration data. Please let me know if you require more data.
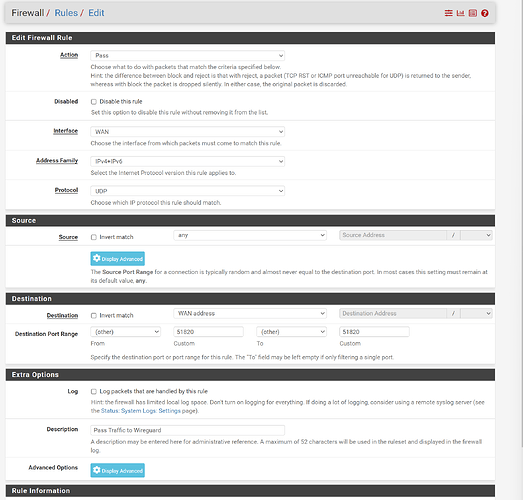
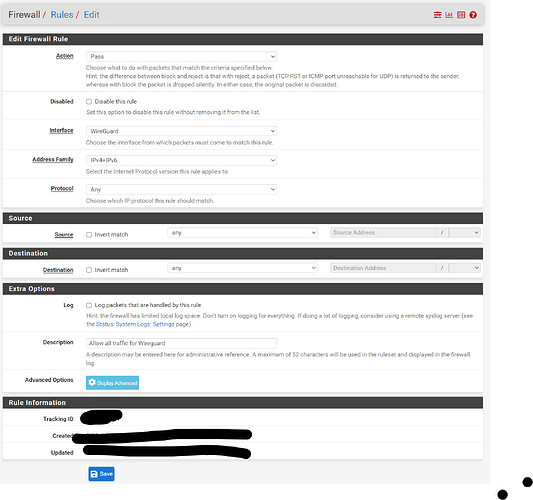
In pfSense, go to Interfaces, Interface Groups. Do you see an interface group named “WireGuard”, which should have been created automatically when you set up the tunnel? If so, go to Firewall, Rules, Wireguard, Edit (your last screenshot above). Change the Interface to WireGuard. Also, change the protocol to “any”. You can tighten this rule down if you want to limit traffic from the Wireguard tunnel, but it’s best to keep it open until you get it working.
Sorry, I assumed you last screenshot was the rule for the Wireguard interface. I realize now that it’s the rule for the WAN. (The small type on my screen is hard to read.) I do see the WireGuard rule further above, and it appears to be open. Make sure it’s on the Wireguard interface (which I assume it is).
I don’t have any other ideas. Maybe you can upload a shot of your client configurations in pfSense and on the iPhone.
I mean your peer configurations. (The pre-shared keys should be dotted out.) Also, the tunnel configuration.