Hello there!
I have followed a few tutorials, Tom’s… Christian’s from PFSense and such. RIght now I am trying to get a site to site vpn working with my PFSense box and a ubuntu server wireguard client.
I have the noip-duc service running on boot and then shut down and then wireguard being started 5 minutes later. There’s a script that runs every 24 hours to update the IP after shutting down wireguard and then turn it back on so we can get the proper IP.
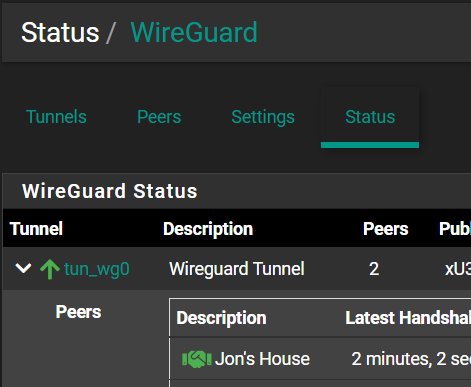
I can’t seem to get this working correctly, however. I have a peer that connects and all with the tunnel when I am local to my house. But the disconnect is seems to be translating the tunnel to an interface and assigning it as a gateway .
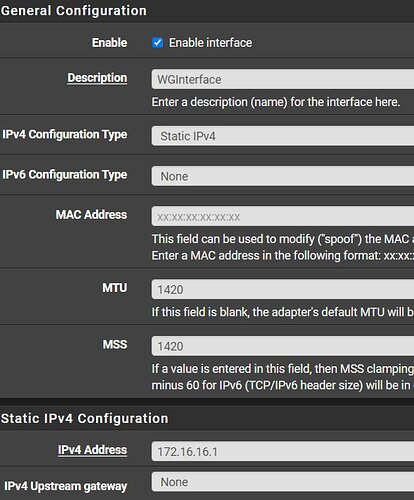
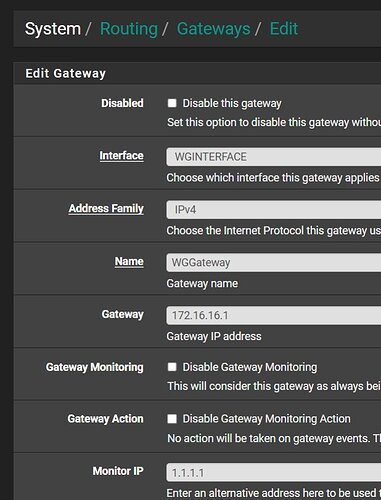
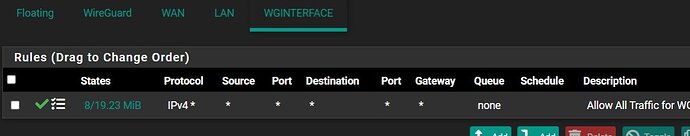
Am I right to take the tunnel connection to create a wireguard interface, assign it 172.16.16.1 /24 as the address and then it should just work? I seem to have the interface rules wide open to allow all ipv4 as well. It seems any video that I watch it is talking about a third party service like mulvad for the policy routing and such but it should be possible with a self hosted server at my friends house? I want to direct two clients at his house through his connection for his outside IP.
I have attached some screenshots in hopes there’s a glaring issue with my config. I guess I am new user so I can only post one pic at a time. Sorry.
Thanks!