I have some users connected to the LAN interface but as the administrator I want to be the only person that can access the Firewall for configuration whiles the other users are blocked to do so. I could have put the users on a separate VLan but from experience when I did that and with the various systems in place that Cisco Management Switches and Windows Active Directory Servers and File Servers, when users are connecting to the Windows File Servers and it takes sometime before documents open and that makes the the users complain. So in order to solve that I had to put the servers and the user computers on the main LAN.
Now I tried setting up a rule in the LAN firewall to allow only my IP to have access to the firewall and block the others but it did not work. I think it was because the Anti-Lockout Rule was enabled. But before I disable that I want to know if my rule will work because I don’t want to be locked out of the system for good.
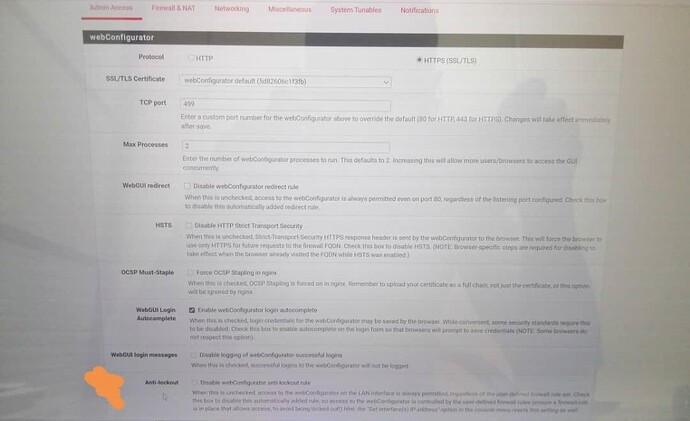
Disabling Anti-Lockout Rule:
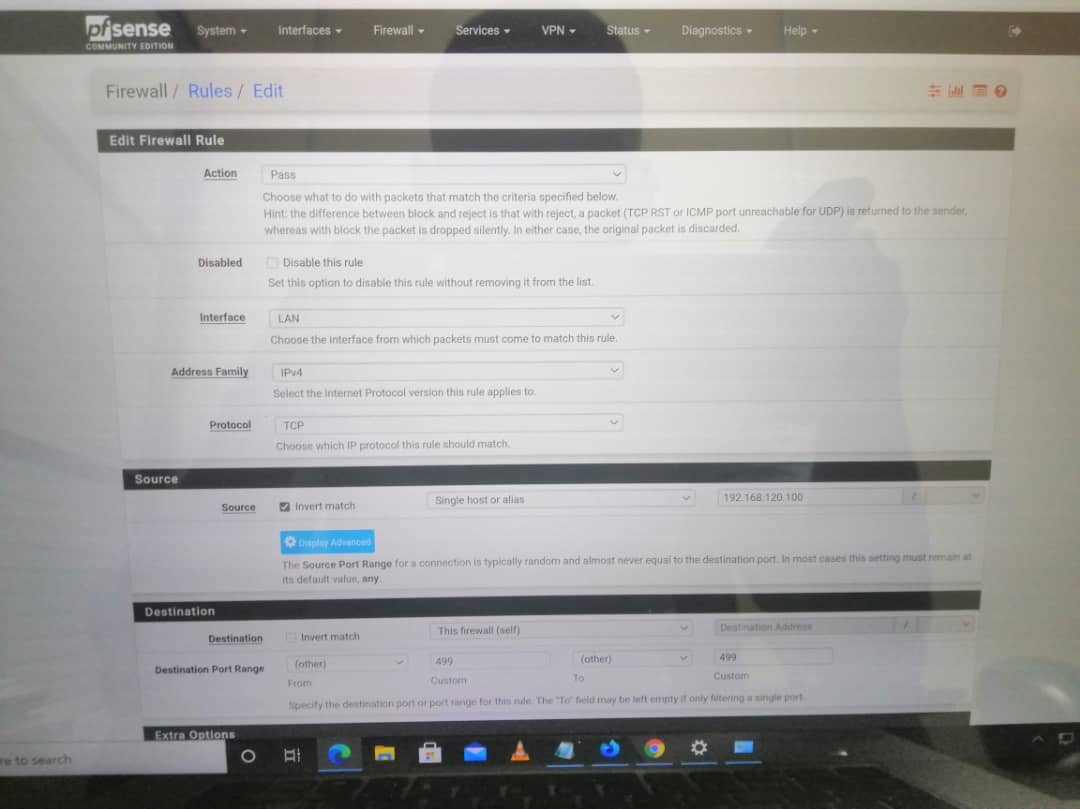
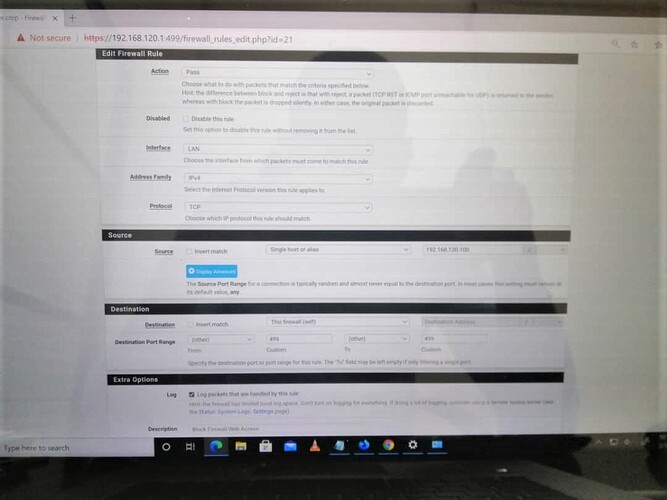
Rule to allow only my IP to have access to the Firewall for web configuration:
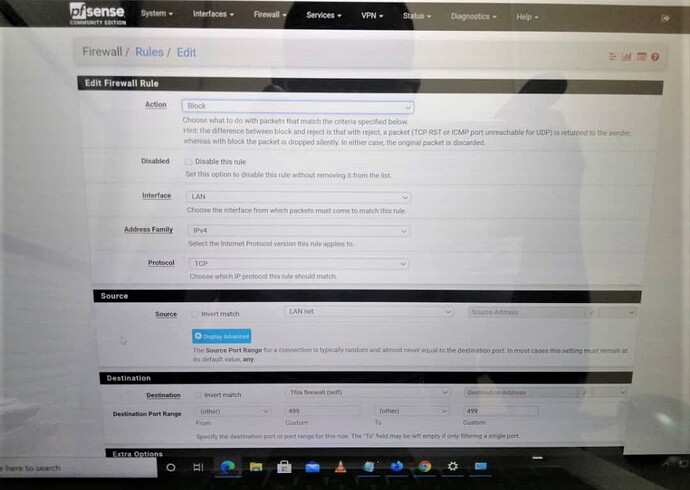
OR I should have these two rules instead
1.
Counting you guys.
Thanks