Hi, I’m using Cisco terminology, but this should apply to other switches.
There Are two main operation modes for switch ports. Trunk and Access.
What it really means is this: Trunk uses VLAN tags and Access doesn’t.
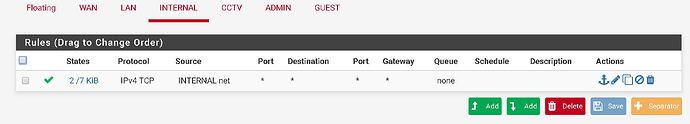
When you connect PFSense without VLANs, it should connect to an port in Access mode. Access mode by default it’s associated to VLAN 1 (in Cisco), but you can associate to any VLAN. (all the ports on the same VLAN can access each other) But only one VLAN at one time.
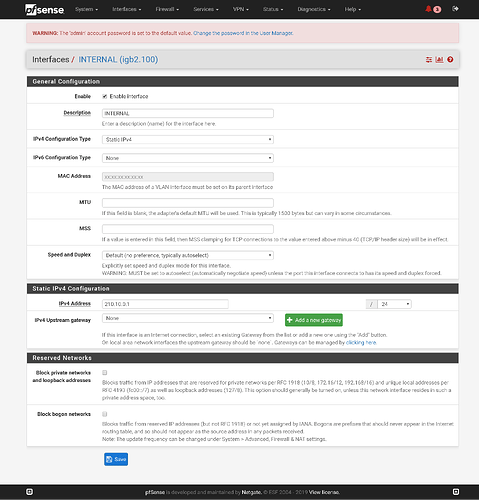
When you associate an Interface to a Vlan on PFSense, it starts using VLAN Tags to identify each frame.
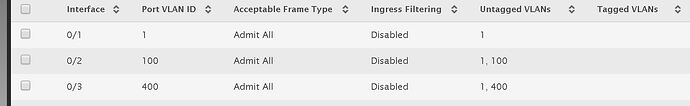
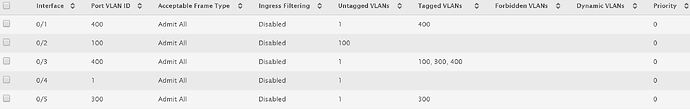
On the switch you should use trunk mode and allow the VLANS you need on that interface. Trunk mode allows to use many VLANs on the same port at the same time. That’s why it needs to be tagged, to differentiate each frame and know which VLAN it belongs.
Check if your Switch supports trunk mode (the name can change depending on you switch brand)
I’m not Cisco expert but.
VLAN 1 on Cisco does not use TAGs, so you cannot connect VLAN 1 on PFSense to a Switchport on trunk Mode with VLAN 1. VLAN 1 is just a name but it’s not tagged as VLAN 1
Assigning interfaces on PFSense directly (native) and via VLANs at the same time is possible but it’s complicated on the switch side.
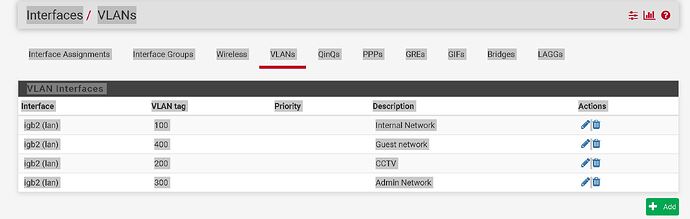
I think you should not use the native interface (directly) and only use only VLANs. So you need to create an additional VLAN, let’s say 500 and assign your LAN interface to it. For example:
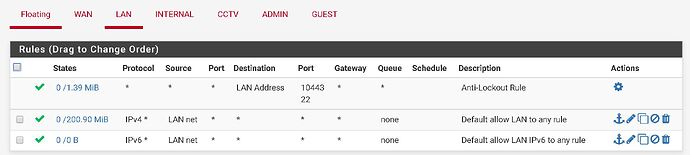
igb1.500 = LAN Devices eg. switch, uap-lr, servers.
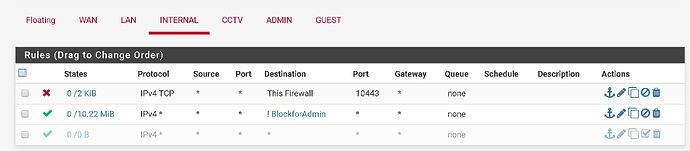
igb2.100 = offices PC access only internet and servers that it is on LAN network.
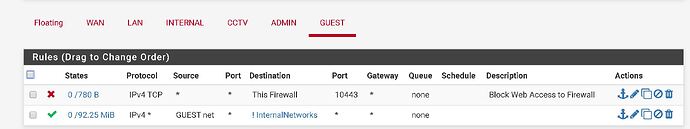
igb2.200 = CCTV
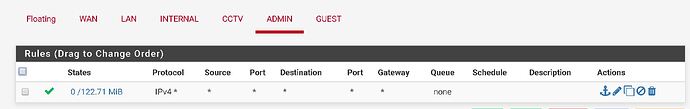
igb2.300 = Admin PC eg. my laptop that can manage all devices
igb2.400 = Guest access only internet
(if you’re using igb2 directly at the same time, that’s probably the problem)
Because you’re using igb2 for everything I’m assuming you’re using igb1 for LAN and igb0 for WAN (or vise versa)