IpSec Tunnel Setup
Pfsense Box 1
Running DHCP and Resolver
IP range of LAN subnet = 10.1.1.0/24
WAN is set as DHCP and gets ip from ISP
IPSec Tunnel Info:
- Phase1:
Interface = LAN
Remote Gateway = 10.1.1.9 (Ip address of the Pfsense Box 2 is getting as it is connected to LAN network of Box 1)
- Phase2:
Mode = tunnel
Local Sunnet = 10.1.1.0/24
Remote Subnet = 172.10.10.0/24
Pfsense Box 2
- Phase1:
Interface = WAN
Remote Gateway = 10.1.1.1
- Phase2:
Mode = tunnel
Local Sunnet = 172.10.10.0/24
Remote Subnet = 10.1.1.0/24
The issue:
I am currently working from a system that is attached to the 10.1.1.0/24 network on the Box 1 system. The tunnel is up and both phase1 and 2 f the tunnels is showing as connected. From the 10.1.1.0/24 network I can ping systems on the 172.10.10.0/24 network both by IP and FQDN name. This also holds true when I am connected to a VM on the 172.10.10.0/24 network, from that VM I can ping the gateway of both Pfsnese boxes, so network traffic between the two networks is passing through with out issue. The kicker is, from a vm or system on the 172.10.10.0/24 network I am unable to get out to the internet. Such as when I try and ping 8.8.8.8 or google.com the network doesn’t look to be either getting out or the return is not getting back in. I say not getting back in because when doing packet captures on both the Pfsense boxes I can see ICMP traffic coming through with the correct source and destination data.
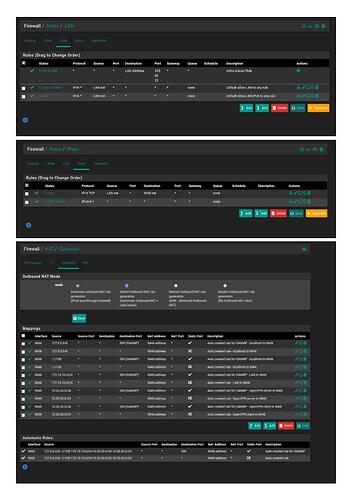
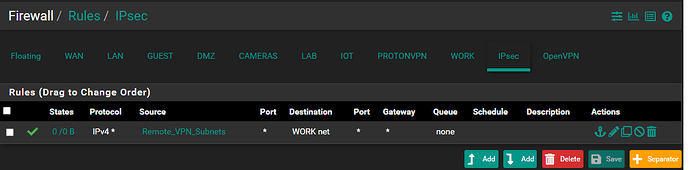
I followed the instructions on Netgates docs page along with looking over and following along with other tuts to set up an ipsec tunnel.The difference with my setup is my tunnel are not connecting over both WAN connections but rather LAN (Pfsense Box1) to WAN (Pfsense Box2). As for firewall rules, under the IPSEC tab in Rules its wide open with the following,
Protocol = ip6
Source = *
Port = *
Dest = *
Port = *
Gateway = *
Queue = None
This type of rule is the same on both systems.
Any help with this would be awesome. Thank you