Hi everyone,
This will be my first post in this forum, so if I’m not in the right section, please let me know. Also, sorry for the long post, but I want to make sure that I’m explaining the situation thoroughly.
For the past few weeks I’ve been having a problem that I’m unable to solve.
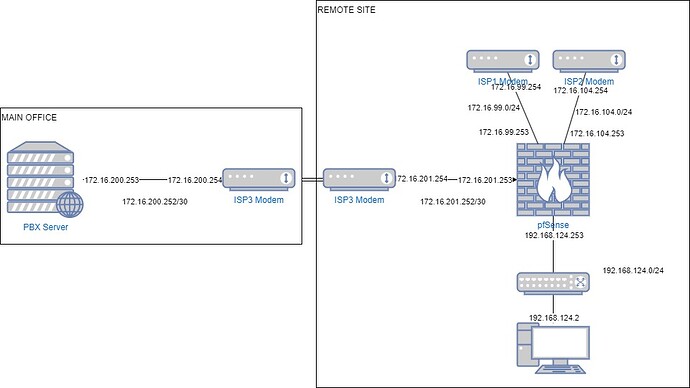
I’ve got a custom pfSense box currently in production environment that is working great. I’ve got a dual WAN setup with failover, multiple VLANs and an IPsec tunnel to our main coorporate building where the main site resides.
The issue is that some of our collaborators will be moving to this site and they will be connecting to our PBX server. Now, I could use the IPsec tunnel that is already working but I have a dedicated link that goes from this site to the main coorporate building. This dedicated link works like a VPN. The ISP gave me two network segments for each end of the link: 172.16.200.252/30 for the main coorporate building and 172.16.201.252/30 for this site.
On the main building, I’ve connected the end of the link directly to one of the PBX’s interfaces and configured it accordingly with the IP address 172.16.200.253. Routes were added to the PBX’s routing table so that it knows how to get to the other end of the link.
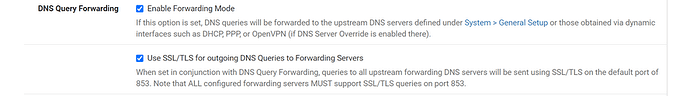
On the site that has the pfSense box, I connected the end of the link to the pfSense box and configured it as a WAN interface with a static IP 172.16.201.253. I then configured a new gateway for that WAN interface with IP 172.16.201.254. Then, I created a static route so that the destination network 172.16.200.252/30 is reachable through the created gateway. The last step was to configure a DNS resolver so that clients on the pfSense LAN can access the PBX server with a FQDN but routed through the dedicated link making it like this: pbx.example.com resolves to 172.16.200.253
Now the part that I haven’t been able to get right:
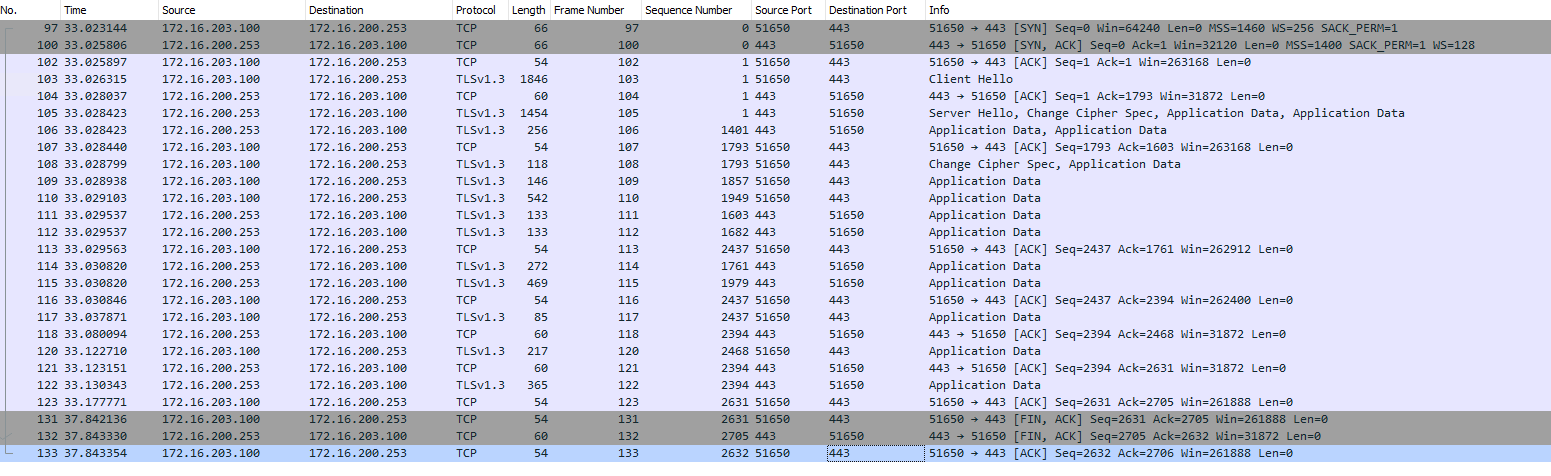
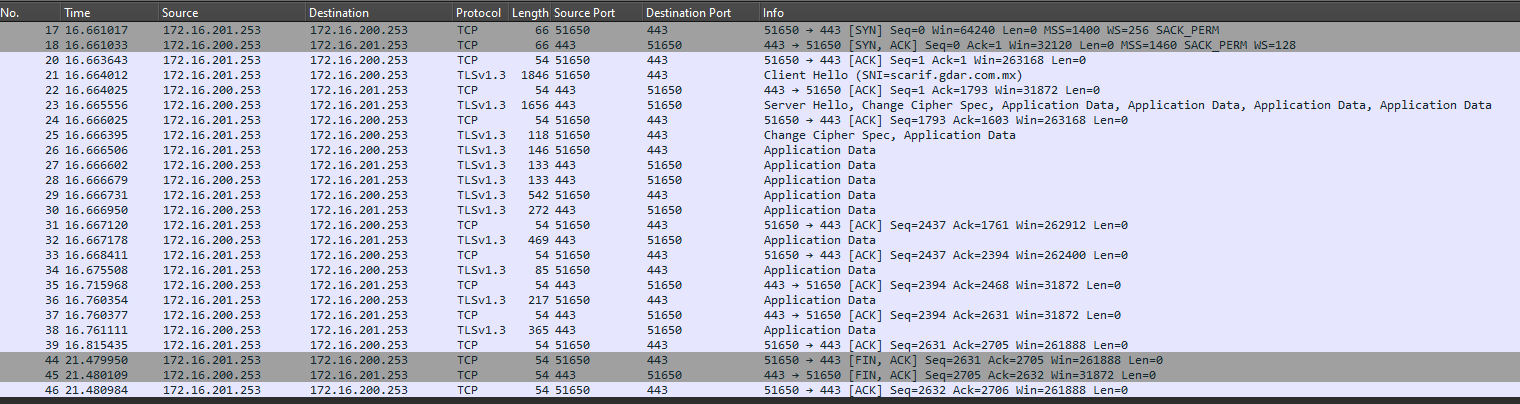
From the pfSense LAN and VLANs, I’m able to ping both the main building dedicated link gateway and the PBX server and vice versa. Also, I’ve checked that the FQDM for my PBX resolves to the correct IP in the pfSense LAN and VLANs. Traceroute from a client PC on the pfSense LAN to the PBX server is also succesful. However, when I try to use a web browser to enter the PBX system form the pfSense LAN it gives me a timeout error.
I’ve made packet captures on the client PC, pfSense box and PBX server and what I can see is that requests are getting out of the pfSense box, arriving at the PBX server, but when the PBX server replies, the packets never make it to the client PC.
The other interesting thing that I found was that if I create an allow all incoming traffic through the dedicated link interface on the pfSense box, if I try to SSH into the pfSense box, it accepts the traffic, but hangs until it says Connection closed by 172.16.201.253.
Another thing worth mentioning is that I’ve tested with an old Cisco RV320 router this same setup and it worked without any issues. The only things I did on that RV320 were configure the WAN with the same parameters as the pfSense, a static route and a resolver for the FQDN of the PBX server.
I’m really at my wits end. I hope someone can help me crack this thing.
Thank you and again sorry for the log post.