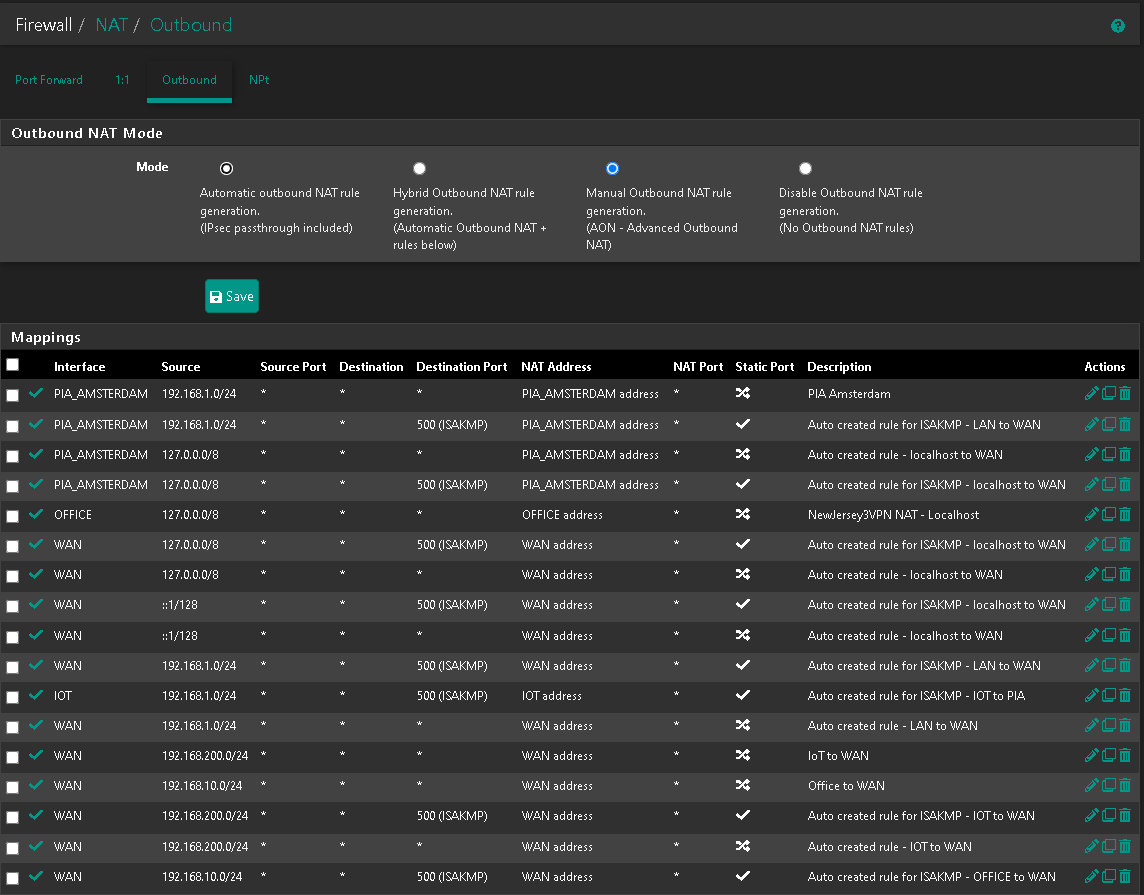
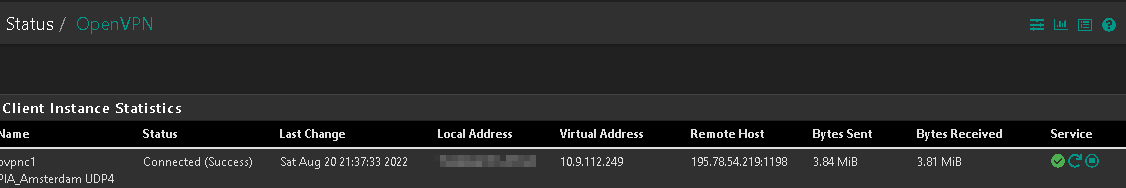
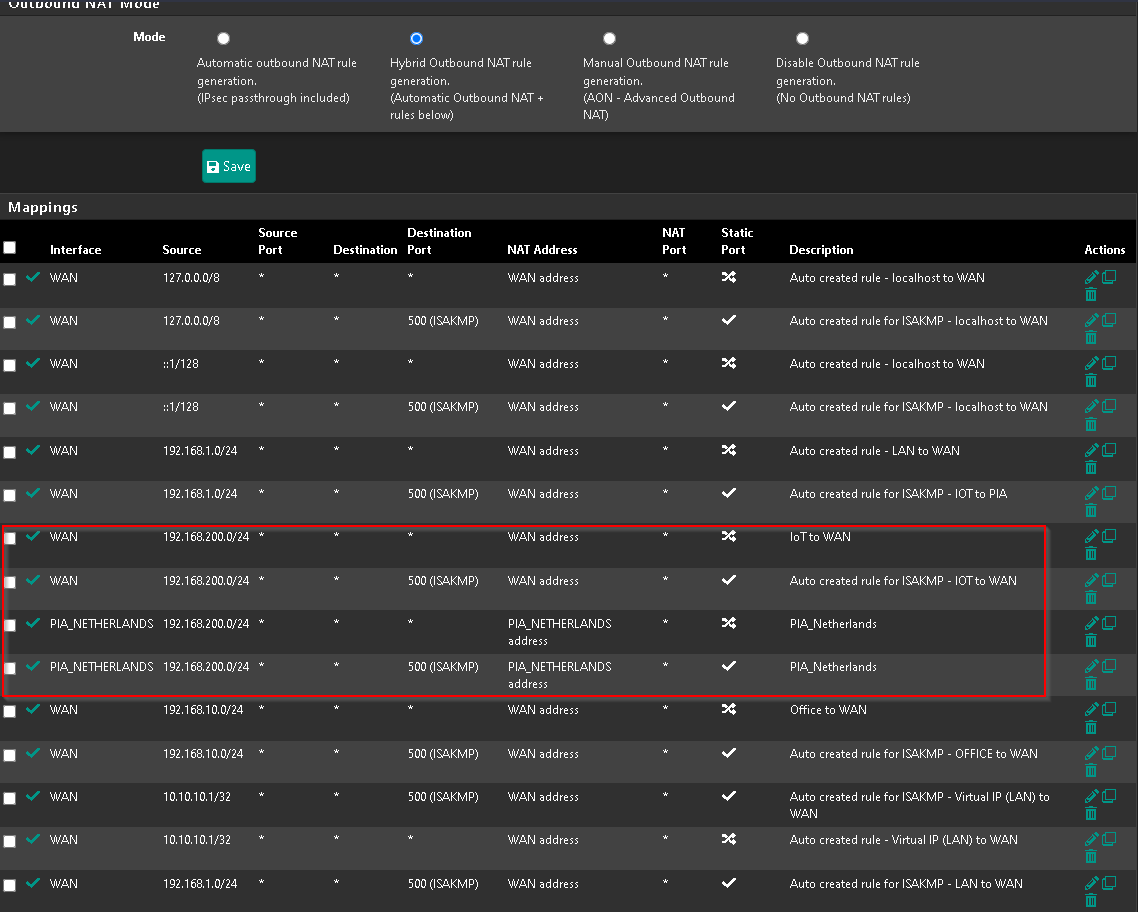
Greetings all, I am having troubles routing particular traffic to my PIA Gateway. The OpenVPN, Interface, Gateway are all showing enabled and up however when I put a rule in to route a particular host to it, it does not seem to be working - all traffic continues to route out to my WAN. I have followed the guides, and pretty sure I have it setup properly. I used to do this via ExpressVPN but just made the switch over to PIA, and cannot for the life of me figure out where I am going wrong. I have the FW rules configured along with the outbound NAT…the major difference I see between ExpressVPN and PIA, is that I appear to be getting an internal virtual IP address which I did not get with ExpressVPN. If I run a ping test to the virtualIP via the PIA openVPN interface, that passes. Anything beyond that (1.1.1.1, 8.8.8.8, etc) fails. And of course when I do an IP lookup, it comes back as my WAN IP and not my PIA VPN IP. Any thoughts?
My hunch is my outbound NAT is not setup properly…and unsure if I need to take into account he virtual IP to PIA VPN remote IP.
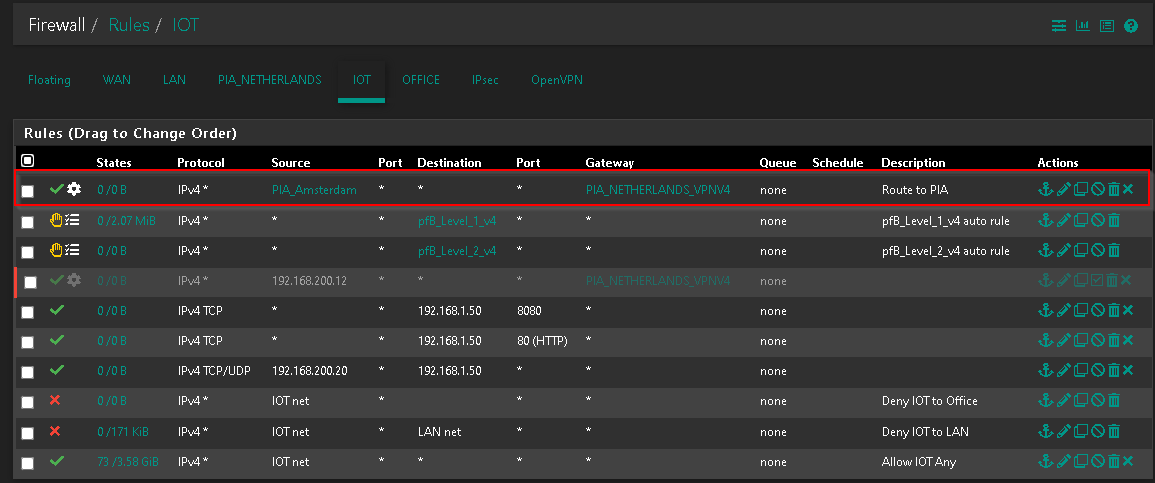
I tore down the PIA config and started from scratch - originally I re-purposed my old expressVPN config and was wondering if something was stale (even after reboot). I am now able to ping out from the VPN interface, however my FW rules that are configured to route particular hosts through the new PIA gateway don’t seem to be taking effect as I am still showing my public ISP address rather than my PIA public IP address. I’ll take the small victories…but not sure why my policy based routes aren’t working…
Are you following my latest video for the process?
It’s much easier to set up vlans, then have one where all the traffic leaves via the ISP and the other where all the traffic leaves via VPN, then you can be certain all the time of where your traffic is going.
Thank you for the feedback - I did not follow the new one but rather one of the older ones…as well as a few others out there in the web. I am going to tear down and try once more…I think the only difference in mine was that I did not setup a kill switch…but maybe I missed a checkbox along the way. I will step through shortly and report back…much appreciated!
Thanks for the feedback neogrid - I do have vlans setup but mostly for segregation of internal traffic (IoT vs Office, vs guest wifi)…and I agree with you completely. However, I am looking for a quick and dirty way of selectively routing various devices at the flip of a switch. One use case is to bypass certain streaming restrictions, and another is for testing things for work…I am in IT and sometimes I need to apply various security policies based on things such as geography…so having the ability to quickly drop a test machine into various regions throughout the day is extremely useful for me.
In your case, you could just setup a trunk port, then connect your laptop say, entering the vlan in the interface config and you’re good to go. Gotta say I haven’t tested it out but it sounds like it ought to work if you want to flip between vlans on one connection.
Still no dice. I have it setup per the video but still not routing out openvpn. I also put in the kill switch however I still have WAN access. Here are a few screenshots…apologies as I am listed as a new user so I can only post one at a time
Thanks, I may set that up…I am like a dog with a bone right now, don’t want to let this go until I figure it out (especially since I had this working but with a different VPN provider - I have upgraded the firmware recently so not sure if that is having some effect)…but even if I do, I will likely give your suggestion a shot.
Okay, so I moved my kill switch rule off of the floating rule and just below my lan rule that is routing to my PIA gateway…and that killed my WAN access…so another small victory. Now I just can’t figure out why the rule preceding it to send it to my PIA Gateway is not working.
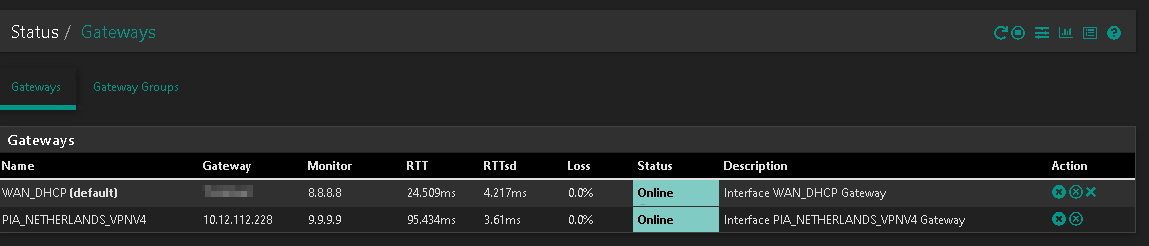
EDIT - NVM, my PIA GW was down while I tinkered…as soon as I brought it back online, I defaulted back to my WAN IP.