An organization I’m helping just migrated from a small SonicWall to a larger pfSense firewall. Inside the walls, everything is working perfectly, but there is one remote access issue we’re trying to work through and I’m not sure it’s something that can be done in pfSense.
The organization has a specific LAN for their phone system that uses a their Cisco PBX as the DHCP server. With the SonicWall, they could connect to the network and had a VPN configured that assigned the remote client an IP address for that LAN.
Reading through all of the documentation on the pfSense site, I can’t find where this is even possible with pfSense. Changing the DHCP server for the PBX system is not an option at the moment, and I’m unable to configure the gateway to be the firewall. I really need for the pfSense OpenVPN client to get an address on this LAN’s subnet.
Ideas would be greatly appreciated.
OpenVPN does not assign them LAN IP addresses that would be the same as another adapter because it is not designed to work that way. But you can use FreeRadius to assign each user a static IP in the OpenVPN IPv4 tunnel network range.
1 Like
Wow – Thanks. I’ve always had the limited mindset of Radius being only authentication. This is exactly what I needed. Thank you!
2 Likes
OK, My excitement was short lived.
Quick network configuration clarification:
- Netgate 7100 is running pfSense
- Unifi 48 port switch is connected to the Netgate
- Everything is connected to the Unifi switch, and traffic is isolated with VLANS
– VLAN 2 (VOIP), VLAN 10 (STAFF), VLAN 20 (GUEST), etc…
- pfSense is DHCP server for all VLANS except VLAN 2
- Cisco PBX is DHCP server for VLAN 2
What I did:
- I set up FreeRadius3.
- Verified configuration and authentication
- Successfully got pfSense to assign custom IP address to client
The current struggle:
- If I assign a custom IP that’s in the range where pfSense is the DHCP server, all is right in the world.
- If I assign a custom IP that’s in the VOIP range, there is no response from anything – even pfSense (I have a pfsense interface IP address assigned just for grins)
Assumptions:
- I’m assuming that pfSense wants to route the traffic through itself using the default gateway parameters for the assigned interface. That would make sense when assigning it an address where it’s a DHCP server, and is pretty much a requirement if you’re going to hop subnets, like in the video.
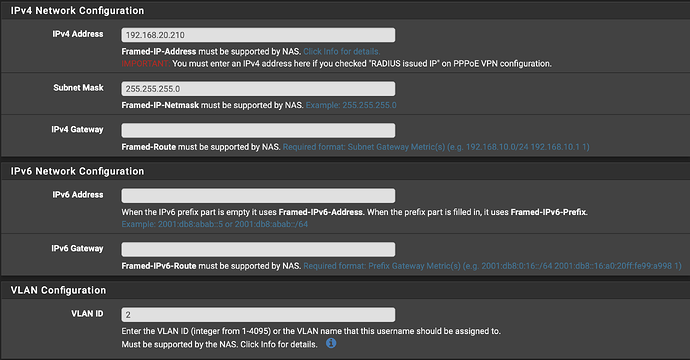
- However, I’m not hopping subnets – I’m staying in the range of the VOIP VLAN. So, the next thought is that I’d need to assign a VLAN of 2 in the VLAN section of the user config in FreeRadius (it was actually what I did first), but this doesn’t appear to work. The wording of the VLAN assignment box makes me wonder if this is only applicable to NAS installations, which is not my use case. If it’s assigning my client to VLAN 2, then the gateway should not be necessary as I’m on the proper network with a valid IP address for that network.
Thoughts?
Firewall rules? Maybe you need to add one on VOIP side
Might be more clear if you posted a map and listed out how you want the rules and routing to work between the networks.
It really could be a firewall rule issue. I’m admittedly not that experienced with firewalls with respect to VPN’s, but I’m trying to learn as much as I can.
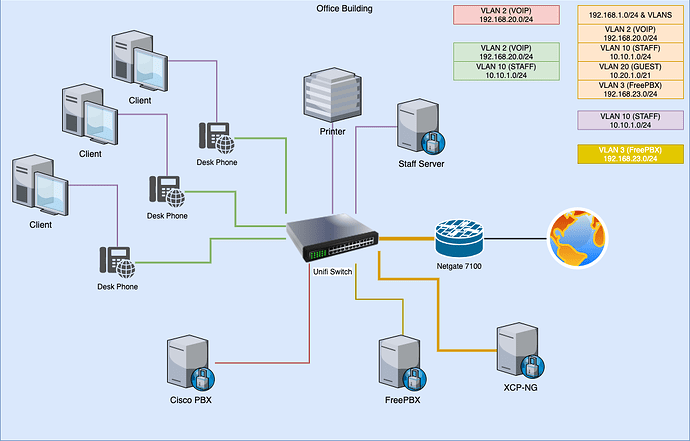
The diagram is below. I have a VM on the XCP-NG instance that is just connected to that network and can access the phone system perfectly, but it’s not an ideal remote working solution, and I can’t give that to the volunteer who is supposed to be helping manage the old phone system. I’m also working to migrate them to a FreePBX solution, which eliminates this, but I can’t do that until after travel restrictions lift.
Here are my firewall rules:
OpenVPN:
VOIP:
Only one rule to deny broadcasts at 239.2.2.2, port 2000 so the pfsense log is clean.
There is no explicit allows here. Does there need to be one? If I’m forcing the vpn user on that interface (vlan 2), why would the firewall block it?
FreeRadius User Config:
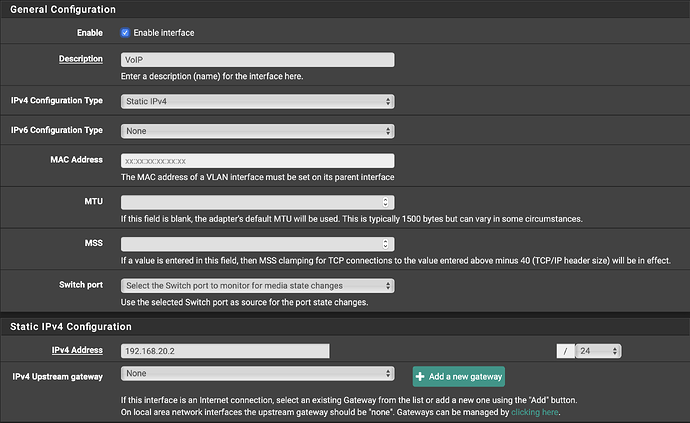
Interface settings for VOIP VLAN:
Desired Outcome:
VPN user is connected to only the VOIP VLAN with a static assigned IP address of 192.168.20.210.
The ideal way to set this up is have the assigned IP’s in the OpenVPN range and create a rule that lets them have access to the networks that needs, such as the VOIP network.
True, but the challenge is that the Cisco PBX is also the DHCP server and pseudo gateway for the VOIP network. I’m unable to modify the current assignments on that network.
I say pseudo gateway because the way the Cisco system works is the phones talk to the PBX and the PBX has a separate interface that can talk directly to the internet (I realize now I failed to document that on the diagram). As a result, there is no communication of any of the devices on the VOIP vlan to the internet or any other network.
Because of the VLAN being configured that way, there is no way to route the VLAN traffic to the OpenVPN network. This is why it’s important to assign an IP address on VLAN 2. I’m not sure how SonicWall did this (it was not an OpenVPN configuration), but it worked perfectly. Unfortunately, the old firewall was way undersized for the size of their network, and we knew that FreePBX has issues with SonicWall’s traffic prioritization. That’s why we jumped to pfSense when we upgraded.
I hope that better clarifies the reasoning for the approach and why things are in the current “intermediate” state.
It sounds like to me the issue you’re having is because you can’t configure the CiscoPBX to use another gateway, so no routing from one VLAN to another. Yes you can make traffic go to it, but it can’t get back. With that in mind, the only thing that I can think of would be to use a layer 2 “bridge” to effectively put your VPN client on VLAN 2. I’ve never done this as it’s not really something you would do, but you have no choice, so I would look at using OpenVPN in TAP mode, https://docs.netgate.com/pfsense/en/latest/book/openvpn/bridged-openvpn-connections.html as that seems to do what you need to do. Again, I’ve never tried it, but if I’ve understood the problem correctly it may be what you’re looking for.
1 Like
Yes, this would be in line with what the SonicWall was doing. Reading the OpenVPN documentation, this might just work. I’ll give it a shot and report back. Thanks!
Just to follow up and close this out, the tap connection worked like a charm. Thank you for tip!
And thanks Tom for the FreeRadius suggestion. It’s going to solve some other challenges that I hadn’t gotten around to addressing, yet.
1 Like
This is actually not that unusual a situation, and I’ve seen it many times over the years supporting Cisco IPsec Client and then AnyConnect VPN configurations. The issue usually comes up with “VPN on a Stick” designs, where the device terminating the client VPN connections is not the default gateway for the connected subnet. In the Cisco world all you had to do was assign the clients IP addresses from an unused range on the connected subnet and the ASA would use Proxy ARP for each client so they would appear to other hosts on that subnet as directly connected hosts - no explicit Layer 2 configuration was required, and it “Just Worked”. The other alternative is to continue to use a different subnet for the clients and add a static route pointing at the VPN termination device to the router that’s the default gateway for that subnet, but in this case that wasn’t an option with the Cisco VoIP server. This option also usually causes IP Redirects to happen on the LAN, but unless you have many, many clients that’s almost never an issue.
Just thought I’d add a bit of perspective to this topic. I hope it was useful.