Hello, im setting up HAProxy on my PFSense box and having some troubles. I followed a few different guides, and i feel like i have a decent understanding of what needs to be set and where.
But i think im missing something.
Setup:
Google domain name
Cloudflare account, created a “A” record for subdomain sub.domain.com to point to my public IP
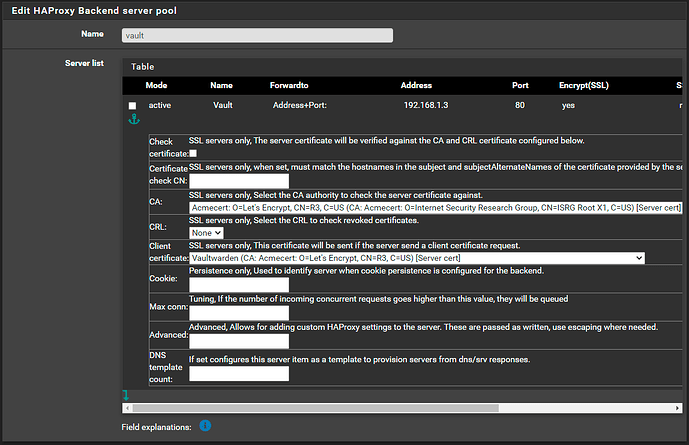
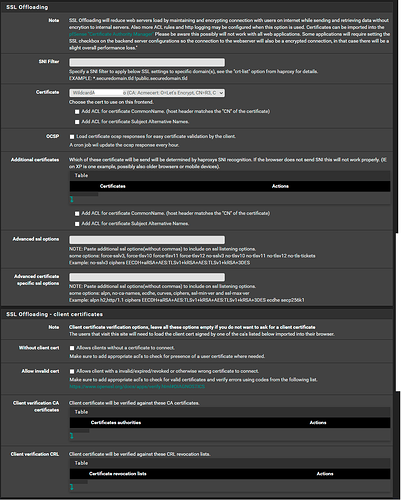
Used ACME to successfully create a SSL certificate.
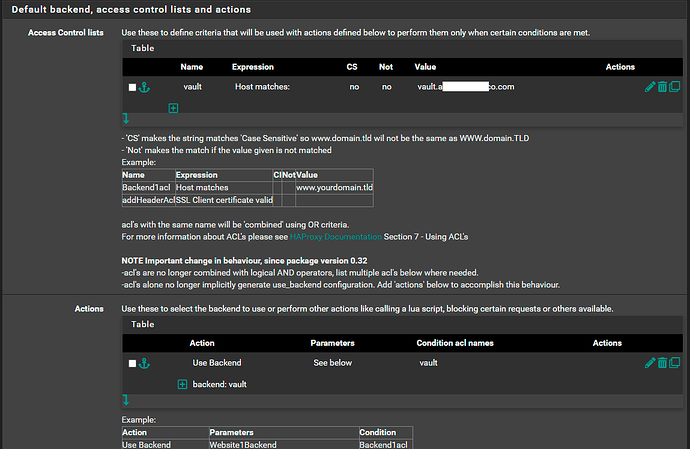
set up HAProxy’s back end, with the local IP of my end device
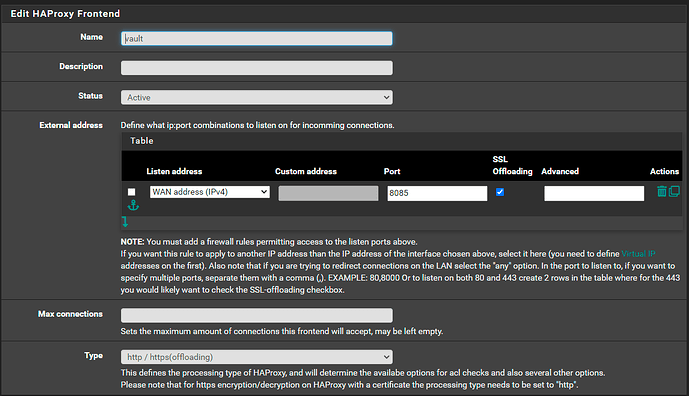
Set up HAProxys front end to listen on my WAN address port 8085 and to send data to the pre configured back end
Created a firewall rule to allow access on the WAN at port 8085.
When i look at my firewall log, i can see the entries for access on port 8085 of WAN, but i get nothing through the proxy, and the web browser errors with a “timeout”.
To test the forwarding of the domain to my public IP, i briefly exposed the port for the PFsense login and i was able to access it, so i know that’s working. (and i disabled that rule quickly)
Not sure what information to post that would help, but i can post whatever is needed.
Any help would be much appreciated.
Thanks!