Hi,
I just finished to get my pfSense to work in HA and I have openVPN working to access the main LAN network.
I have now created a new vlan (lan_office) on top of my LAN interface on a different subnet.
LAN: 172.16.10.1/24
LAN_OFFICE: 172.16.200.1/24
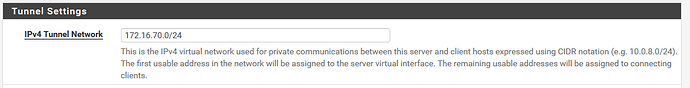
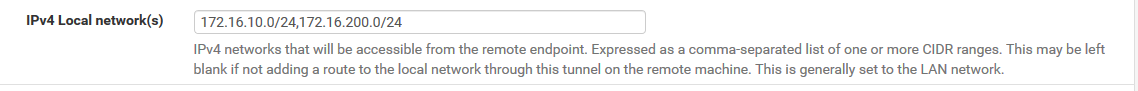
In my openVPN, I set IPv4 Local network(s) to
172.16.10.0/24, 172.16.200.0/24
From my windows machine, I connect to the vpn and I cannot ping the machine 172.16.200.201
In pfSense > Diagnostics > Ping I can ping the 172.16.200.201 when I select the openvpn source address
Can anyone please assist?
Thank you
Is that your tunnel IP ? I can’t tell from your wording, if is, then it should be on a different subnet to your vlan / lan. Then have a rule that allows traffic to move between the subnets.
1 Like
No, the 2 ip subnet above are my 2 lan.
Main LAN: 172.16.10.1/24
Second LAN : 172.16.200.1/24
The vpn tunel is just a ramdom IP I set
Do I create the rule on which interface?
At the moment I can access and ping all the machine on the main LAN when connected to the VPN
Well the way I’ve done it is to create an alias in Firewall > Aliases > IP just add your subnets 172.16.10.0/24 (include your OpenVPN tunnel subnet too) etc. Then create rules in each of your interfaces that either allow or deny your subnets/aliases as required. Then your vlans will be able to pass traffic, by default everything is blocked. At least for me it’s easier to then understand what’s going on versus having individual rules.
A side note you can also have an alias for ports then it’s trial and error to identify your ports.
Hi @neogrid
I tried adding rules but that didn’t work
I also added the following in custom code but no luck
push "route 172.16.200.0 255.255.255.0";
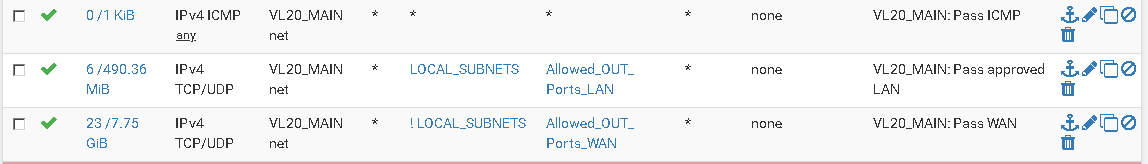
Basically I have three main rules, 1) allow traffic out to vlans (TCP/UDP) 2) invert the first rule to allow out of the WAN (TCP/UDP) 3) Allow ICMP traffic (ICMP).
Have these rules on all vlans slightly tweaked to my needs.
Don’t have to push routes on OpenVPN, I’ve basically treated it as another vlan.
I’d suggest get two vlans working with your rules, then mirror these on your OpenVPN rules.
Can you please screenshot the rules? I can do with a visual to help.
have a peruse of Mr Lawrence’s video, it covers off the basic points
This suite of rules are replicated across my vlans, without them no traffic is allowed by default.
I created a wide open rule on the LAN and NEW_LAN interface and I still cannot ping the machine on the new vlanfrom over vpn 
Does that fact that the pfSense is HA ans anything to do with it?
Did you allow ICMP protocol ? I believe that protocol allows devices on the network to ping each other, I have a separate for that.
yes, I ahve a wide open rule on all interface
I found this on the netgate doc:
If it appears that OpenVPN will not push routes to a client, ensure that a Multi-site style PKI/SSL setup is in use and not a shared key setup or an SSL/TLS setup using a /30 tunnel network.
Routes cannot be pushed on a shared key setup or an SSL/TLS setup using a /30 tunnel network. Routes may be directly added to the client configuration using the IPv4 Remote Networks list (e.g. 192.168.99.0/24, 192.168.203.0/24 )
not quite sure what it mean
Did you setup firewall rules for your OpenVPN Server ? If you have and allowed all traffic it should flow. They ought to be similar to your vlan rules.
Well I’m in no position to correct the people who made pfsense. Though I have used SSL/TLS + User Auth as my server mode though with /24 tunnel.
firewall rules for your OpenVPN Server is wide open
@LTS_Tom are you able to help please?
Bellow is the output for
route print
192.168.84.1 is Windows 10 gateway
172.16.10.1 is LAN gateway (datacenter)
So aI can see both ip been pickup but not
172.16.200.0 (NEW lan in datacenter)
===========================================================================
Interface List
26…f0 76 1c 27 d0 63 …Realtek PCIe GBE Family Controller
10…0a 00 27 00 00 0a …VirtualBox Host-Only Ethernet Adapter
#2
13…00 ff 83 af 81 48 …TAP-Windows Adapter V9
6…76 29 af 14 82 23 …Microsoft Wi-Fi Direct Virtual Adapter
#5
14…74 29 af 14 82 23 …Microsoft Wi-Fi Direct Virtual Adapter
#6
20…00 ff b6 58 52 2d …Kaspersky Security Data Escort Adapter
25…00 ff e2 26 62 30 …Kaspersky Security Data Escort Adapter
#2
15…00 ff 91 28 38 78 …Anchorfree HSS VPN Adapter
22…00 ff cd b0 d8 67 …Leaf Networks Adapter
5…74 29 af 14 82 23 …Realtek RTL8723BE Wireless LAN 802.11n PCI-E NIC
11…74 29 af 14 82 24 …Bluetooth PAN HelpText
1…Software Loopback Interface 1
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.84.1 192.168.84.4 25
127.0.0.0 255.0.0.0 On-link 127.0.0.1 331
127.0.0.1 255.255.255.255 On-link 127.0.0.1 331
127.255.255.255 255.255.255.255 On-link 127.0.0.1 331
169.254.0.0 255.255.0.0 On-link 169.254.107.230 311
169.254.107.230 255.255.255.255 On-link 169.254.107.230 311
169.254.255.255 255.255.255.255 On-link 169.254.107.230 311
172.16.2.0 255.255.255.240 172.16.70.1 172.16.70.2 25
172.16.10.0 255.255.255.0 172.16.70.1 172.16.70.2 25
172.16.70.0 255.255.255.0 On-link 172.16.70.2 281
172.16.70.2 255.255.255.255 On-link 172.16.70.2 281
172.16.70.255 255.255.255.255 On-link 172.16.70.2 281
192.168.56.0 255.255.255.0 On-link 192.168.56.1 281
192.168.56.1 255.255.255.255 On-link 192.168.56.1 281
192.168.56.255 255.255.255.255 On-link 192.168.56.1 281
192.168.84.0 255.255.255.0 On-link 192.168.84.4 281
192.168.84.4 255.255.255.255 On-link 192.168.84.4 281
192.168.84.255 255.255.255.255 On-link 192.168.84.4 281
224.0.0.0 240.0.0.0 On-link 127.0.0.1 331
224.0.0.0 240.0.0.0 On-link 169.254.107.230 311
224.0.0.0 240.0.0.0 On-link 192.168.56.1 281
224.0.0.0 240.0.0.0 On-link 172.16.70.2 281
224.0.0.0 240.0.0.0 On-link 192.168.84.4 281
255.255.255.255 255.255.255.255 On-link 127.0.0.1 331
255.255.255.255 255.255.255.255 On-link 169.254.107.230 311
255.255.255.255 255.255.255.255 On-link 192.168.56.1 281
255.255.255.255 255.255.255.255 On-link 172.16.70.2 281
255.255.255.255 255.255.255.255 On-link 192.168.84.4 281
===========================================================================
Persistent Routes:
None
IPv6 Route Table
===========================================================================
Active Routes:
If Metric Network Destination Gateway
1 331 ::1/128 On-link
22 311 fe80::/64 On-link
10 281 fe80::/64 On-link
13 281 fe80::/64 On-link
26 281 fe80::/64 On-link
13 281 fe80::58ad:fc2d:6469:6d8a/128
On-link
22 311 fe80::61ae:1d17:8b84:6be6/128
On-link
10 281 fe80::b416:aba6:d6a2:f41/128
On-link
26 281 fe80::c11f:c62a:b13b:f735/128
On-link
1 331 ff00::/8 On-link
22 311 ff00::/8 On-link
10 281 ff00::/8 On-link
13 281 ff00::/8 On-link
26 281 ff00::/8 On-link
===========================================================================
Persistent Routes:
None
Do I need to create a new openVPN server to deal with that new network?
What is the 172.16.2.0 network I’m seeing? Is that the network you’re coming from?
A good old REBOOT of the windows machine resolved my issue lol 
1 Like