I let this thread go stale as I have not been home/had time to deal with this issue, but today I am away from home with family for the long holiday, and I am noticing the same exact seemingly DNS issue on my VPN split tunnel setup. I have wireguard running on pfsense and have 2 VPN’s set up for my laptop, one for split tunnel and 1 for full tunnel.
I am starting to thing it is not DNS…
The only difference between my wireguard configs on the client side are the “Interface Address” (same subnet, only off by 2 numbers in the last octet, and the “AllowedIPs” for the full tunnel being
AllowedIPs = 0.0.0.0/0, ::/0
And the split tunnel being a set of my prive IP’s that I use:
AllowedIPs = 10.1.15.0/24, 10.90.5.0/24, 10.80.5.0/24, 10.81.5.0/24, 10.70.5.0/24, 192.168.69.0/24
All other settings (minus keys) are the same. Both VPN’s work fine except for some websites I just can’t get to on the split tunnel much like the issue I have with certain subnets within my LAN. While on the split tunnel, I can ping a website like CNN via terminal, and I get responses, but the website just does not load.
In wireguard, for both tunnels, DNS is set to 10.1.15.1 which is the “wireguard” subnet I have set up in pfsnese. I really don’t know the full tunnel works fine, and the split tunnel reacts exactly like I am on one of the internal subnets that doesn’t seem to be getting correct routing. If I edit the split tunnel AllowedIP’s to be 0.0.0.0/0, ::/0, that connection suddenly works fine.
I am entirely at a lost, but I alst only know enough to know enough… I don’t even know where to start with this issue. I know at some previous point in time my split tunnel worked perfectly, but I have not used it in a while and I am not sure when it started to work incorrectly. I can’t imagine what I would have changed that caused this for the split tunnel or the other subnets - I assume its a single issue affecting both scenarios.
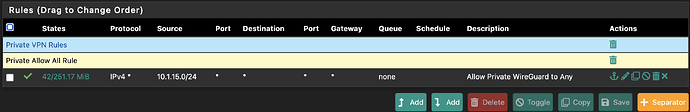
Rules for this subnet are extremely simple:
Wireguard settings for split tunnel:
[Interface]
PrivateKey = xxxx
Address = 10.1.15.4/24
DNS = 10.1.15.1
[Peer]
PublicKey = xxxx
PresharedKey = xxxx
AllowedIPs = 10.1.15.0/24, 10.90.5.0/24, 10.80.5.0/24, 10.81.5.0/24, 10.70.5.0/24, 192.168.69.0/24
Endpoint = xxxx
I can’t get the split tunnel interface to work correctly even just removing 1 subnet at a time from the AllowedIPs list. Only once I set it to 0.0.0.0/0, ::/0 does it work correctly.