Hello all…
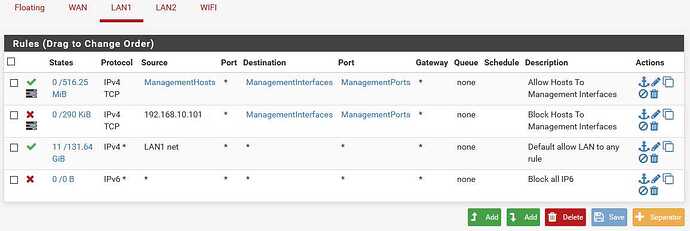
My goal is to allow one host [for now] to access various management interfaces.
Those interfaces are: pfSense, a wireless a.p., and a Cisco switch.
The first two are blocked, but I’m still able to access the switch from another host.
It’s clearly not hitting the rule. But I don’t know how to determine
what Cisco is using, and therefore update the rule.
Any specific packet-capturing to achieve this?
Only allowed to post one picture, so here are two:
https://postimg.cc/gallery/0NTd0Wq
For each interface you need an allow rule with the IP address (or alias) you want to allow and the management port. Then below that on each interface you need a deny rule to that port. If you deny access to the management IP, then the device will not be able to get out.
Seems that nothing prevents my second pc from accessing the Cisco mgt gui.
I’ve configured it to http and https, and specified that 192.168.10.101 cannot reach it,
but it doesn’t care for my desisres Tom 
It is being blocked from reaching the A.P. and pfSense mgt tho…
I’m 2/3 complete