You are excellent!!! All my purchases are based on your video. I have an all UnFi setup with a USG, UniFi Switch and a couple of ACs.
But OpenVPN on USG is just horrible as you mentioned in your videos. I have a spare Atomic PI and thought maybe I can offload OpenVPN by setting up as pfSense on it.
I have managed to setup pfSense (192.168.1.3) to connect as VPN Client client for my VPN service (KeepSolidVPN).
pfSense shows that the VPN connection is working. I was thinking if i just point my clients to the IP of this setup it will funnel connections similar to PiHole (192.168.1.2; UniFi Controller also runs here) which I have now. I already have a fully running DHCP via Unifi (192.168.1.1) hence I don’t really want to create additional networks of set this pfSense as a replacement router/dhcp. I just needed to set it up as a vpn gateway for my clients. But doing so gives my clients the usual PiHole’d data but not VPN’ed.
Reading through this forum mentions portforwarding rules but its not really clear to me.
Please help. Thank you in advance.
The easy solution would be to have pfsense at the head end, can you draw a map of what exactly you are trying to do?
Thank you for responding.
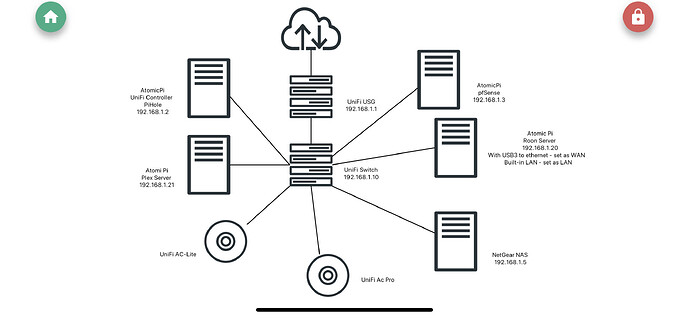
I made a crude map as you asked.
I am happy to offload the pihole and just run my all my DNS and adblocker off pfsense but I cant waste my USG.
The best way to have the pfsense act as the VPN for tunneling all the devices traffic through it is to put the devices you want behind it.
In your setup, I can’t see how you can prevent VPN traffic going out via the ISP if the service fails for some reason. Segmenting traffic makes it much easier to have an idea of what is happening.
Thank you for your feedback.
Is there no way to make it act like a dns gateway only? That way I can just point some devices like apple tv’s, fire tv’s to it? Use its IP as a DNS?
One option is to make the pfsense an edge device in between the modem and the usg. Is that possible? That way pfsense is a vpn and transparent and usg retains all network tasks?
Sounds like a lot of effort to configure PfSense only to host a VPN client. I have a backup VPN (server) on a NAS, it’s probably much easier to host your VPN client on a Raspberry Pi and use static routes.
It would be much easier to use Pfsense as your router, introduce vlans, setup your VPN client then setup a OpenVPN server to access your VPN service remotely 
I really like single view pane. But vpn performance of the usg is poor. I have a spare atomic pi that i was thinking I can double duty as a dns gateway and vpn client.
I am open to your ideas but losing unifi single pane and ease of use routing, managing access point and switch might be hard.
I’d say as you wouldn’t have to buy any new kit, then you can easily try the PfSense as your router, hopefully your switch can handle vlans. Then you need only have an ISP-vlan and VPN-vlan and it will give you what you want.
If it doesn’t work for you then you can easily revert back to your current state.
vlans aren’t too difficult, if you’re already familiar with PfSense then you have a setup that can easily accommodate further enhancements 
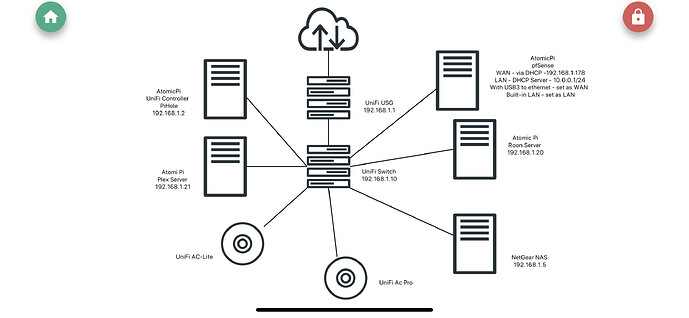
I managed to run the pfSense/AtomicPi inside my existing network.
I connected the WAN (dhcp) to one of my unifi LANs, the pfSense LAN is with a DHCP server that is 10.0.0.0/24. Clients on this subnet are now on VPN!!!
I guess the question is how do I let my existing network (192.168.10/24) on UniFi access the new (sub)network (10.0.0.0/24) on pfsense? That way I can make a separate WLAN on the Unifi that points to the pfSense Subnetwork. Also allows the clients on the sub network to access my NAS and Plex servers.
I have have attached an updated diagram.
Once again thank you for your patience and support guys.