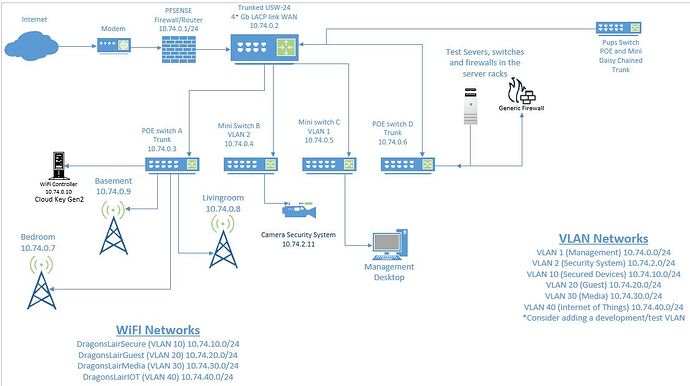
I have been working to rebuild my network from a series of 5 different cheap routers, can you say double NAT troubles, to a new pfSense and UniFi network. But I am stuck on the inter-vlan routing. I grew up with starting with a known good config and then apply security on top one rule at a time so if it breaks you know why. But my VLANS won’t talk to eachother when the rules are pass any/any/any so I can’t progress to the lock it down stage.
If I connect 3 PCs to different ports on the pfSense and keep them all on the same VLAN they talk. But the moment I pull a PC to a different VLAN it is unrachable except from the pfSense diagnostic ping. So I know the problem is at the pfSense level not the UniFi
All LAN ports are currently bridged for VLAN testing (LAGG/LCAP trunk worked fine so I will go back to that config once I can solve VLAN)
All bridges, and VLANS have been configured as interfaces with corresponding DHCP
Firewall rules on ALL interfaces are set to pass any/any/any
All VLANS are able to talk to the WAN
The pfSense can talk to any VLAN device
Devices on the same VLAN talk to eachother.
Suggestions where I should be looking in the pfsense setup? I’ve factory reset four times now, incase I had screwed something up so bad I’d never make it work. So learning the controls fairly well. 
Sounds like you haven’t allowed TCP/UDP between vlans but have allowed ICMP.
Easiest thing to do is to add your subnets to an alias, then create a rule allowing access to your vlans via the alias as your destination.
Order of your rules makes a difference too.
I may be missing what you are saying. I know what the alias feature is but how would that be set to allow it when any/any/any doe not?
If you have the rules between the subnets wide open and the devices can not ping each other then next check to make sure they have the pfsense as the default gateway.
1 Like
Thanks, alas not the whole issue but I did find out that my Unifi switches were actually trying to take charge and fixed them.
Continued testing has me convinced its that I don’t understand pfSense routing settings well enough (I’m actually a total noob at pfSense). If I configure the router on the internet side to route between the VLANS then they start talking and the firewalls can block that traffic when I take away the wide open.
So I guess the question is do I keep a serpate router, or do I keep trying to figure out pfSense routing with the limited information I can find.
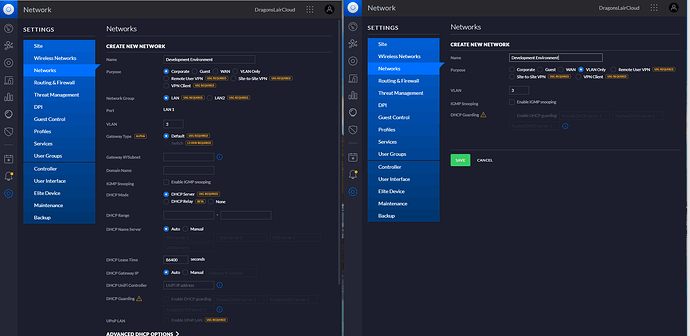
I feel like a total fool now, but given how long I struggled with this and the few unanswered topics I have found on the internet similar. I will post my stupidity for others to learn from. The screen on the left is BAD when you are doing VLANS the screen on the right is the correct way to do it.
It all works now 
![]()