Hello everyone,
I have a NAS Synology DS918+ that hosts calendar on port 5006 and some other things behind a pfsense 2.4.5 box connected to 2 WAN from 2 diff providers with each a fixed public IP. A FQDN corresponds to each public IP.
Each internet connexion has its own modem with public IP and NATs to the pfsense box. Load balancing is set on pfsense as well as fail over.
So Internet Modem1 is 8.X.X.X, nats to 192.168.6.1, then pfsense box has a WAN1 192.168.6.2 with a gtw 192.168.6.1
Internet modem 2 is public IP 15.x.x.x, nats to 192.168.5.1, then pfsense box has a WAN2 192.168.5.2 with a gtw 192.168.5.1.
LAN is 192.168.20.1/24
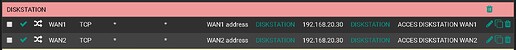
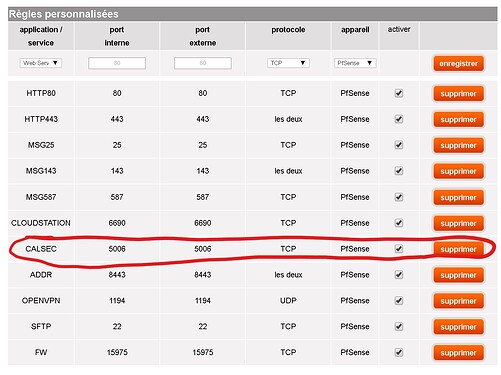
All works fine, no problem there but I created a rule to allow all to the NAS for port 5006 allowing me to synchronise my agenda with phones, etc from the outside. So calendar on phone is set to https://mydomain.fr:5006/web/calendar/etc.../
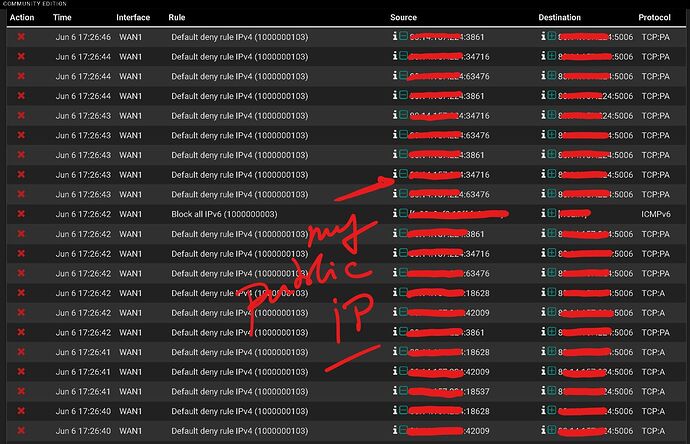
For some reason, pfsense blocks my public IP on WAN1 and port 5006 when I try and synchronise my calendar from outside.
I don’t understand why. Can someone explain what I am doing wrong?
Thank you for your help.
"Default deny rule IPv4 " is the message you get when you don’t have the port open in the firewall to allow the traffic.
Thank you for your answer.
Agreed except that I created a Nat rule that allows all to NAS IP and 5006 port (caldav) among others.
Anyway, why would pfsense block traffic from my public IP address? Pfsense doesn’t know my public IP as the modem transforms the public IP into 192.168.6.1 (WAN1GW) and then redirects it to 192.168.6.2 (pfsense ).
Sorry but I’m starting with all this and comprehension level might not be up to par!
Hi again,
On the modem pretty much everything is directed towards the pfsense box.
The weird thing is that pfsense blocks only the WAN1 IP not WAN2.
When you’re testing this port forward and seeing it blocked, are you inside your network? Meaning are you on your LAN. Can you test from your cellphone with the wifi disabled, so you are outside your network?
Hello Bruce. Thank you for your answer.
So sorry for the delay in my response. Kinda crazy here!!
Yes from inside the network. I’ve just tried from the outside connecting my laptop to my cell phone and it works.
What is the problem then? I do not understand this concept.
It’s called hairpinning. By default any traffic originating from the inside of a network that travels to the firewall and then needs to be routed back into the same network is blocked by default. This is to prevent DDOS attacks trying to degrade external network access such as the internet. Since the deny rule would be the last one for the traffic to hit, it would require the most processing by the firewall as well.
Hello and thank you for your answer.
OK Got it!
It’s going to be a bit complicated to set up in thunderbird one agenda with a local address to have my agenda when I am on the local network and another one when I am outside… I tried to put a rule allowing all traffic from this specific public IP address but it doesn’t work.
Weird thing though is that it blocks only WAN1 and not WAN2. Does this mean that the modem on WAN1 is not “hairpinning compatible” and modem on WAN2 is ?
It doesn’t have anything to do with the modems since they only route. Are you using a URL for your destination address in your setup? If so, does it use the IP on WAN 1?
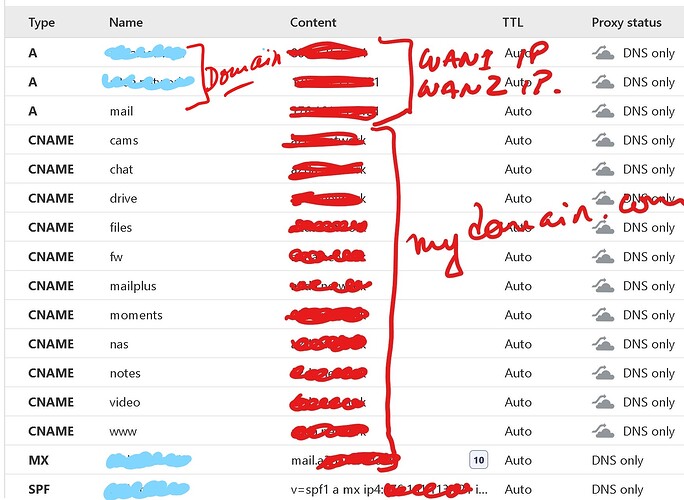
Yes I am using nas. mydomain. com:5006/web/calendar/user to access my calendar on lightning/thunderbird
On the Cloudflare side, nas CNAME mydomain.com and mydomain.com A with both public IP addresses
The thing is it never blocks WAN2 public IP only WAN1 public IP.
I believe that when you use WAN 2 for internet it is still resolving your URL to the WAN 1 IP. So traffic comes out WAN 2 and then comes in WAN 1 to reach your NAS. If you want to test it, create a hostfile record on your system for your URL with the WAN 2 IP and see what it does when using WAN 2 for internet.
1 Like
If you just want to enable hairpin NAT, and be aware of the potential for DOS attacks FrefFarrell mentioned, then in PFSense go to System > Advanced > Firewall & NAT > Network Address Translation, and set “NAT Reflection mode for port forwards” to “Pure NAT”. You may need to reboot the router if it doesn’t automatically reload the firewall rules at that point.
1 Like
Sorry for the delay in my answer. It works now from outside. I set NAT to pure nat and rebooted but it doesn’t seem to do much…
All I care is to have my agenda available and its modifications updated in real time!
Thank you for your help!!
@paddaone did you consider setting up OpenVPN ? I’m using an ownCloud calendar which can be reached and synchronised everywhere. I’d say your approach is risky, though I’m no pentester. I see numerous alerts from QNAP that seem to put these NAS devices at risk, for sure I wouldn’t allow any type of access over the internet. In principle the only point of risk is OpenVPN which is fairly robust.