I’ve asked this on Netgate forums but decided to give it another shot here.
Now, i’ve done some fairly advanced things with pfSense so i don’t consider myself novice but this situation is driving me crazy.
A customer needed to replace a aging, and failing Checkpoint with something else and naturally with covid and work from home vpn licenses were a big issue so the path forward was pfSense. The setup is, well, both simple and complex, depending from where you’re starting. To sum it all up, the migration was a sucess and all works as expected except for one tiny thing, public DNS servers in DMZ.
Here the topology:
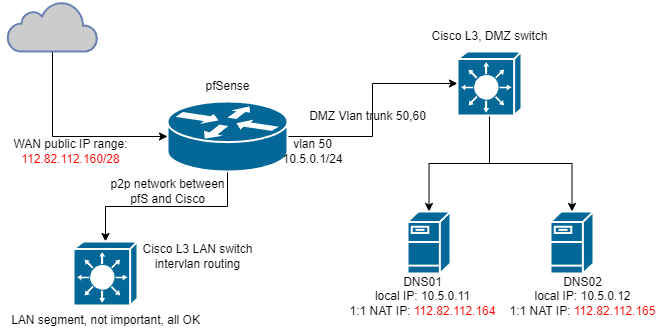
The problem is as follows… and please bear with me, I know there’s split DNS and i used it frequently but this is something i inherited so here I am.
Both DNS01 and 02 can’t talk to each other over their public IPs until I enable NAT reflection on both 1:1 mappings and enable outgoing nat for reflection, and that’s fine, I get that, so that’s enabled and now they both respond, well kind of, to queries. The problem starts when dns02 (slave) want’s to update it’s records from dns01 (master), it’s rejected - ok at least traffic flows.
Now it’s rejected because the master 112.82.112.164 (10.5.0.11) allows zone transfers to happen only from a public IP of slave which is 112.82.112.165 (10.5.0.12) and the bind log on the master says it rejected a zone transfer request from 10.5.0.1 - naturally because the config says so.
So i see there’s NATin happening, also the pfctl -sn shows additional lines when you enable reflection and outgoing nat for it but it’s using a pfSense interface address for that particular VLAN, so VLAN50 on pfSense is 10.5.0.1.
I can clearly edit the bind configuration to allow transfers from local IPs it’s just that apparently checkpoint handled it obviously differently and NATed it to public address.
Finally is this the intended pfSense implementation, to nat to it’s interface or am I missing some additional steps, like some more NATing of pfSense itself
p.s. I’m far from DNS security whiz so maybe somebody has an idea as to why are transfer limited to only public IP addresses?!