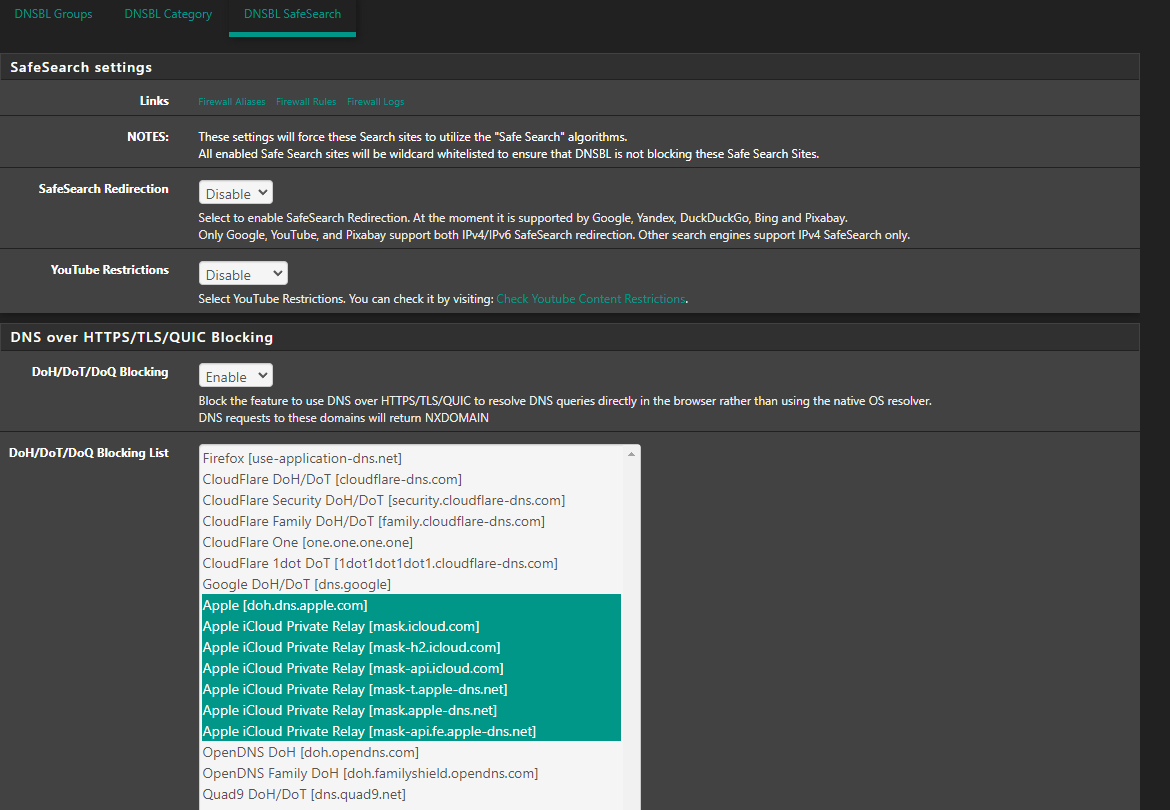
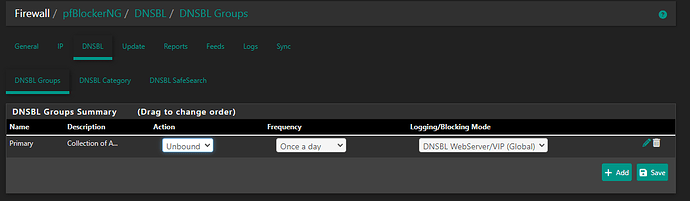
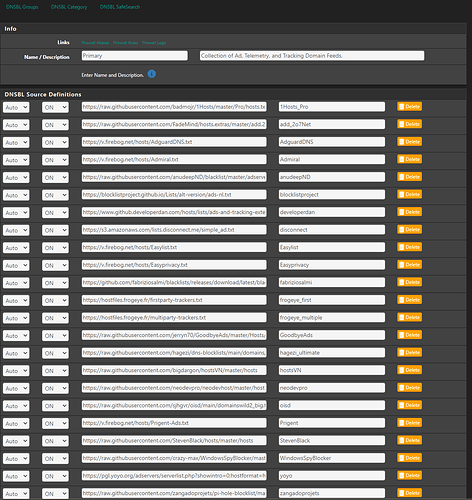
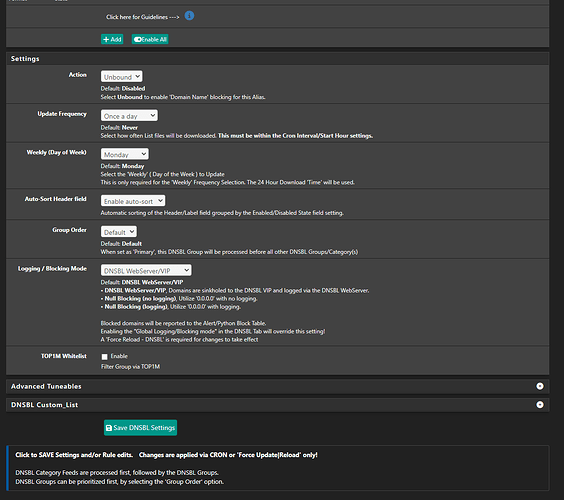
I run pfsense at home and I am experiencing some strange issues seemingly to do with pfblockerng.
The issue I was seeing was my IoT & guest vlans were not resolving certain websites. I didn’t really notice since I personally never use these… but strangely I am on vacation this weekend and am seeing this issue on 1 of my 2 wireguard connections as well. On my laptop I have a full tunnel and a split tunnel config, same subnet on the pfsense side… only 1 has allowIPs of:
AllowedIPs = 10.1.15.0/24, 10.90.5.0/24, 10.80.5.0/24, 10.81.5.0/24, 10.70.5.0/24, 192.168.69.0/24
and the full tunnel is:
AllowedIPs =0.0.0.0/0, ::/0
I am seeing the same issue I see on my local vlan subnets across these two different wireguard client configs.
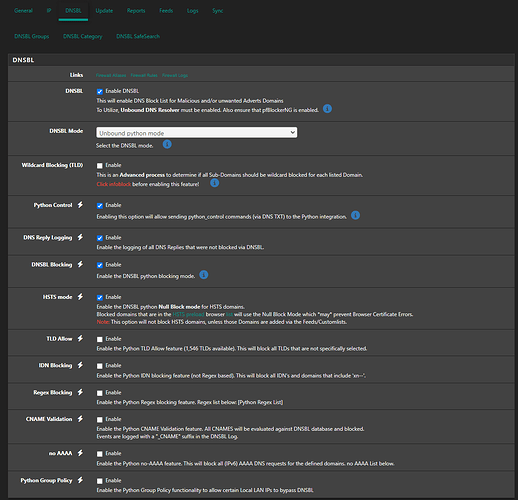
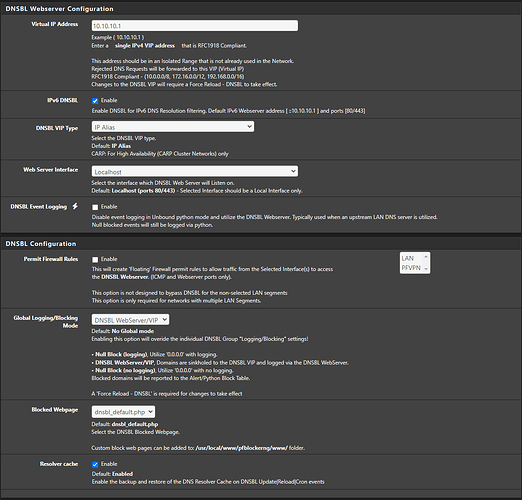
I have been playing around with settings and it seems like if I dissable pfblockerng and dnsbl, reset pfsense states, and bounce unbound, things start to work as expected. I am testing this via trying to resolve cnn.com. When I am in the state of this issue, I can’t get it to load (it will eventually load… after minutes) on my split tunnel nor on a VM I spun up on my IoT network back at home. As soon as I take pbclockerng down, clear states and bounce unbound, I can immedietly get to cnn.com again.
Of note, which makes no sense to me, I don’t have this issue on my full tunnel with
AllowedIPs =0.0.0.0/0, ::/0
Originally I thought this was a DNS issue, but even when I am in the state of not being able to load the website, I can ping cnn.com without issue. What the heck is going on? Any ideas how I fix this?
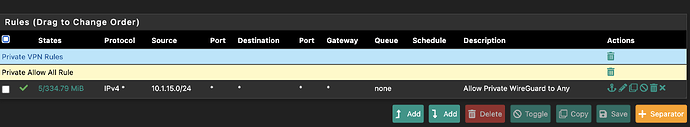
My IoT subnet rules are a little more involved, but seeing as I can replicate it on my wireguard subnet… this is about as simple a ruleset as you could get…
Wireguard settings for the split tunnel:
[Interface]
PrivateKey = xxx
Address = 10.1.15.4/24
DNS = 10.70.5.1
[Peer]
PublicKey = xxx
PresharedKey = xxx
AllowedIPs = 10.1.15.0/24, 10.90.5.0/24, 10.80.5.0/24, 10.81.5.0/24, 10.70.5.0/24, 192.168.69.0/24
Endpoint = xxx
Wireguard settings for the full tunnel:
[Interface]
PrivateKey = xxx
Address = 10.1.15.4/24
DNS = 10.70.5.1
[Peer]
PublicKey = xxx
PresharedKey = xxx
AllowedIPs =0.0.0.0/0, ::/0
Endpoint = xxx