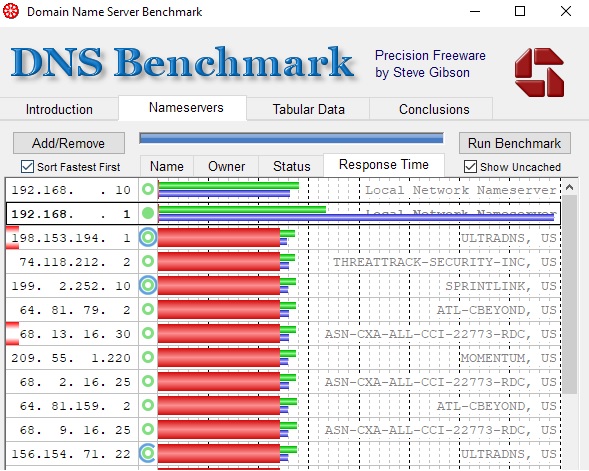
I’m running a pfSense on very beefy hardware. I have recent transitioned over to pfBlockerNG from a Pi-hole. I noticed my name resolution seemed noticeably slower. I found DNS Benchmark from Gibson Research and ran a test against my still in place Pi-hole (nothing points to it but the Benchmark) and my pfBlockerNG.
In the benchmark you can see that the .1 has much slow DNS return on non-cached queries. The Pi-hole is much faster and you can see it’s only slightly slow their going directly to some of the big resolvers.
One of the main reasons for this is that due to the country I live (temporary) in I have all of my traffic run over a VPN to come out near my permanent residence in the US. I have followed some guides for all traffic to go over a VPN Gateway Group, everything is tagged and if it tried to go out any other interface it gets dropped.
The Pi-hole fits into the that model easy because it’s just another IP in my network and come in a LAN interface.
I think pfBlockerNG does not follow this model because it’s being sourced as the pfsense. I have the DNS Resolver setup as a Forwarder that way pfBlockerNG still works and it’s a little faster because I’ll use a big resolver like 1.1.1.1 or 8.8.8.8. To try and force all traffic from the DNS Resolver / pfBlockerNG to go through the VPN, I have the Outgoing network Interfaces set to the 3 VPN Interfaces that make up the Gateway Group (GG wasn’t an option). To prevent async-routing or other issues, only one VPN is enabled at a time. I have a work, and two home VPNs that are needed at different times so I figured a Gateway Group would be easiest to not change the main rule for each vlan each time I need to switch VPNs.
pfSense General Setup, has 1.1.1.1 and 8.8.8.8 with disable DNS Fowarder. The thought behind this was to remove the chicken and egg issue. DNS Resolver must go through the VPN or be dropped, VPN requires DNS name resolution to build the tunnel… 
It sounds more complicated than it is. Everything seems to work fine but my DNS resolution is noticeably slower than a pi-hole.
I’m happy to throw up more configs to help troubleshooting.
That’s an interesting observation, I previously used a pi-hole in-conjunction with my Asus router. When I switched over to PfSense, I assumed, apart from the GUI, there would be no difference with using the pi-hole lists in pfblocker. From your experience it looks like not the case.
Whilst in lockdown, I thought I would try to get a deeper understanding of how DNS and OpenVPN really works with respect to being secure. I’m never really sure if I am actually secure or things just seem to work until they don’t.
With respect to your “chicken and egg” situation, I use AirVPN, when I setup the OpenVPN client I use an IP address to their server so there is no need for DNS to establish the tunnel. The DNS resolver is on AirVPN servers, so this seems the most secure with respect to privacy, when I run a DNSSEC check it comes up positive so I ought to be getting legitimate sites.
I’m debating whether I should be passing all traffic through AirVPN, I believe it ought to be the most private but I can’t work out if it is the most secure. Certain email servers and financial sites really don’t like VPNs so I’m trying to workout the best way to mitigate that too. Looks like I’ll have the time.
I am running dnsperftest with pfblocker tuned on running on my SG-1100 at home while I don’t have a pihole to compare it you, I would not say the DNS is slow at all in pfsense. But this could probably vary a bit base on how many rules you have loaded. Here is a link to the tool I used. GitHub - cleanbrowsing/dnsperftest: DNS Performance test
It’s just an observation and it could really be because of how I have it setup. In theory it shouldn’t be different, one is running unbound and other dnsmasq both are good and can be fast.
I don’t use my VPN provider as a DNS because I switch between 3 VPNs as needed, ExpressVPN for streaming and general usage, work for times I need to work, and a friends house for sites to do taxes. I didn’t have a problem with banks and ExpressVPN but man several tax sites would not accept Nord, Express, or PIA.
I could look at getting the IP address of my VPNs but I prefer to have DNS resolve them as I know a few of them change.
Passing all traffic through a VPN is going to be a personal choice, I’m not doing it for total privacy from everyone. I know that the VPNs I use can see my non-TLS data but I wanted to get my data back to the states or at least to a GDPR country.
One of the things I wanted to do without breaking anything is have the DNS come out at the same location as the VPN that way sites that block content if the DNS provide IP is no geolocated to your traffic… mainly my streaming services.
Hey @LTS_Tom, thanks for your quick response.
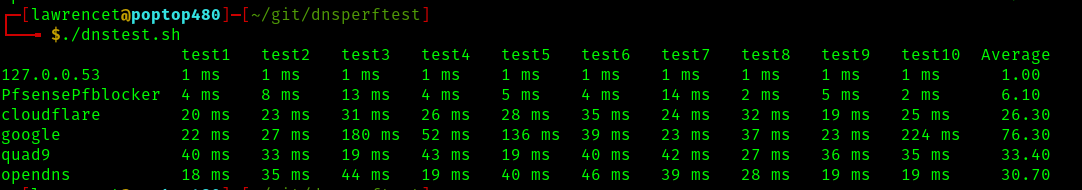
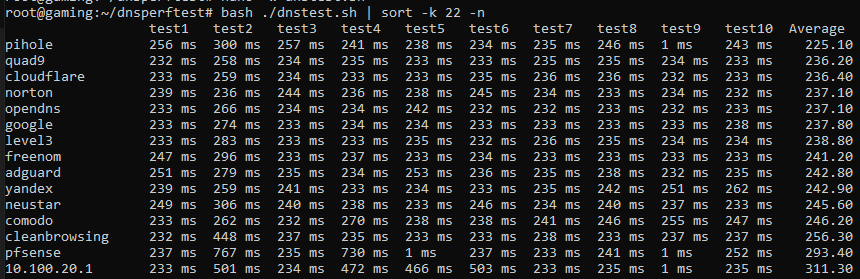
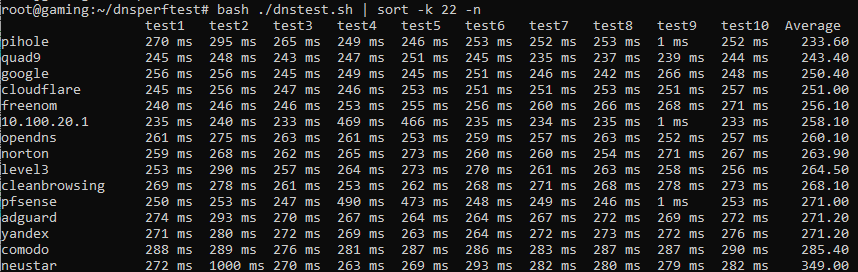
I modified the source to add my pihole and pfsense. As you can see 100ms difference which is weird because they are going through the same openvpn to either 1.1.1.1 or 8.8.8.8, can’t remember which is first in each config.
I need restart the resolvers on both the pfsense and on the pihole as I turned of pfBlockerNG and both devices reports 1ms… darn caching.
After restarting both resolvers I reran the test and while the pfsense w/o pfBlockerNG is better it’s still not as fast.
So my default GW which is pfSense is added to the list, not sure why I didn’t see it before. Also disregard the difference in the pfsense and 10.100.20.1 subnet, my local is 20.1 and the pfsense that I typed is another approved vlan so it’s routing that request.

![]()